overview
neutron-lbaas 从Openstack Queens版本开始被抛弃,而被Octavia项目取代。
https://wiki.openstack.org/wiki/Neutron/LBaaS/Deprecation#When_will_the_neutron-lbaas_deprecation_cycle_end.3Fhttps://docs.openstack.org/mitaka/networking-guide/config-lbaas.htmlhttps://docs.openstack.org/octavia/latest/install/install.html
第一部分 openstack-octavia配置安装
CREATE DATABASE octavia;GRANT ALL PRIVILEGES ON octavia.* TO 'octavia'@'localhost' IDENTIFIED BY 'OCTAVIA_DBPASS';GRANT ALL PRIVILEGES ON octavia.* TO 'octavia'@'%' IDENTIFIED BY 'OCTAVIA_DBPASS';
root@controller-01:~# . adminroot@controller-01:~# openstack user create --domain default --password-prompt octaviaroot@controller-01:~# openstack role add --project service --user octavia admin
openstack service create --name octavia --description "OpenStack Octavia" load-balancer
openstack endpoint create --region RegionOne load-balancer public http://controller:9876openstack endpoint create --region RegionOne load-balancer internal http://controller:9876openstack endpoint create --region RegionOne load-balancer admin http://controller:9876
cat << EOF >> $HOME/octavia-openrcexport OS_PROJECT_DOMAIN_NAME=Defaultexport OS_USER_DOMAIN_NAME=Defaultexport OS_PROJECT_NAME=serviceexport OS_USERNAME=octaviaexport OS_PASSWORD=OCTAVIAexport OS_AUTH_URL=http://controller:5000export OS_IDENTITY_API_VERSION=3export OS_IMAGE_API_VERSION=2export OS_VOLUME_API_VERSION=3EOF
root@ubuntu:~# apt-get install python3-piproot@ubuntu:~# apt install python-virtualenv
6.2 安装disk_builder环境
root@ubuntu:~# virtualenv octavia_disk_image_createroot@ubuntu:~# source octavia_disk_image_create/bin/activate
6.3 安装必要的工具
root@ubuntu:~# apt install qemu-utils git kpartx debootstrap#或者root@ubuntu:~# git clone https://github.com/openstack/python-octaviaclient.git -b stable/trainroot@ubuntu:~# cd python-octaviaclientroot@ubuntu:~# pip install -r requirements.txt -e .
6.4 创建镜像
6.4.1 搭建创建环境
root@ubuntu:~# lsb_release -aNo LSB modules are available.Distributor ID: UbuntuDescription: Ubuntu 18.04.5 LTSRelease: 18.04Codename: bionic
root@ubuntu:~# python3 -VPython 3.6.9root@ubuntu:~# pip3 -Vpip 9.0.1 from usr/lib/python3/dist-packages (python 3.6)(octavia_disk_image_create) root@ubuntu:~# pip -Vpip 20.3.4 from root/octavia_disk_image_create/local/lib/python2.7/site-packages/pip (python 2.7)
root@ubuntu:~# cat etc/apt/sources.listdeb http://mirrors.aliyun.com/ubuntu/ bionic main restricted universe multiversedeb-src http://mirrors.aliyun.com/ubuntu/ bionic main restricted universe multiversedeb http://mirrors.aliyun.com/ubuntu/ bionic-security main restricted universe multiversedeb-src http://mirrors.aliyun.com/ubuntu/ bionic-security main restricted universe multiversedeb http://mirrors.aliyun.com/ubuntu/ bionic-updates main restricted universe multiversedeb-src http://mirrors.aliyun.com/ubuntu/ bionic-updates main restricted universe multiversedeb http://mirrors.aliyun.com/ubuntu/ bionic-proposed main restricted universe multiversedeb-src http://mirrors.aliyun.com/ubuntu/ bionic-proposed main restricted universe multiversedeb http://mirrors.aliyun.com/ubuntu/ bionic-backports main restricted universe multiversedeb-src http://mirrors.aliyun.com/ubuntu/ bionic-backports main restricted universe multiverse
6.4.2 获取源码
(octavia_disk_image_create) root@ubuntu:~# cd(octavia_disk_image_create) root@ubuntu:~# git clone https://github.com/openstack/octavia.git(octavia_disk_image_create) root@ubuntu:~# cd octavia/diskimage-create/(octavia_disk_image_create) root@ubuntu:~# pip install -r requirements.txt -i https://mirrors.aliyun.com/pypi/simple/
(octavia_disk_image_create) root@ubuntu:~/octavia/diskimage-create# cat root/octavia/elements/amphora-agent/source-repository-amphora-agent# This is used for source-based builds#amphora-agent git opt/amphora-agent https://opendev.org/openstack/octavia stable/trainamphora-agent git opt/amphora-agent https://github.com/wangguan1998-long/octavia stable/train#upper-constraints file opt/upper-constraints.txt https://opendev.org/openstack/requirements/raw/branch/stable/train/upper-constraints.txtupper-constraints file /opt/upper-constraints.txt http://172.17.61.200/config/upper-constraints.txt
Tips:在amphora-agent镜像生成过程中会去https://opendev.org站点获取依赖程序包,由于网络原因会导致超时;解决办法是:可根据elements文件的内容将需要的程序包提前下载,再上传至自己的github仓库。
6.4.4 生成镜像
(octavia_disk_image_create) root@ubuntu:~# ./diskimage-create.sh -t qcow2 -o amphora-x64-haproxy -r 1234qwer -s 4 -g stable/train...2021-02-09 02:44:36.763 | Converting image using qemu-img convert2021-02-09 02:45:25.086 | Image file root/octavia/diskimage-create/amphora-x64-haproxy-1.qcow2 created...2021-02-09 02:45:25.376 | Build completed successfullySuccessfully built the amphora using the stable/train amphora-agent.(octavia_disk_image_create) root@ubuntu:~/octavia/diskimage-create# ll amphora-x64-haproxy.qcow2-rw-r--r-- 1 root root 353865728 Feb 9 00:50 amphora-x64-haproxy.qcow2
wget https://bootstrap.pypa.io/2.7/get-pip.pypython get-pip.py
root@controller-01:~# scp image—builder-server:/root/octavia/diskimage-create/amphora-x64-haproxy-1.qcow2 /rootroot@controller-01:~# openstack image create --disk-format qcow2 --container-format bare --private --tag amphora --file amphora-x64-haproxy.qcow2 amphora-x64-haproxy
root@controller-01:~# openstack flavor create --id 200 --vcpus 1 --ram 1024 --disk 2 "amphora"
root@controller-01:~# yum -y install openstack-octavia-api openstack-octavia-health-manager openstack-octavia-housekeeping openstack-octavia-worker python-octavia python-octaviaclient
https://docs.openstack.org/octavia/latest/admin/guides/certificates.html
git clone https://opendev.org/openstack/octavia.gitcd octavia/bin/source create_dual_intermediate_CA.shmkdir -p /etc/octavia/certs/privatechmod 755 /etc/octavia -Rcp -p etc/octavia/certs/server_ca.cert.pem /etc/octavia/certscp -p etc/octavia/certs/server_ca-chain.cert.pem /etc/octavia/certscp -p etc/octavia/certs/server_ca.key.pem /etc/octavia/certs/privatecp -p etc/octavia/certs/client_ca.cert.pem /etc/octavia/certscp -p etc/octavia/certs/client.cert-and-key.pem /etc/octavia/certs/private
mkdir certschmod 700 certscd certs
10.2 创建OpenSSL配置文件
root@controller-01:~# cat certs/openssl.cnf[ ca ]# `man ca`default_ca = CA_default[ CA_default ]# Directory and file locations.dir = ./certs = $dir/certscrl_dir = $dir/crlnew_certs_dir = $dir/newcertsdatabase = $dir/index.txtserial = $dir/serialRANDFILE = $dir/private/.rand# The root key and root certificate.private_key = $dir/private/ca.key.pemcertificate = $dir/certs/ca.cert.pem# For certificate revocation lists.crlnumber = $dir/crlnumbercrl = $dir/crl/ca.crl.pemcrl_extensions = crl_extdefault_crl_days = 30# SHA-1 is deprecated, so use SHA-2 instead.default_md = sha256name_opt = ca_defaultcert_opt = ca_defaultdefault_days = 3650preserve = nopolicy = policy_strict[ policy_strict ]# The root CA should only sign intermediate certificates that match.# See the POLICY FORMAT section of `man ca`.countryName = matchstateOrProvinceName = matchorganizationName = matchorganizationalUnitName = optionalcommonName = suppliedemailAddress = optional[ req ]# Options for the `req` tool (`man req`).default_bits = 2048distinguished_name = req_distinguished_namestring_mask = utf8only# SHA-1 is deprecated, so use SHA-2 instead.default_md = sha256# Extension to add when the -x509 option is used.x509_extensions = v3_ca[ req_distinguished_name ]# See <https://en.wikipedia.org/wiki/Certificate_signing_request>.countryName = Country Name (2 letter code)stateOrProvinceName = State or Province NamelocalityName = Locality Name0.organizationName = Organization NameorganizationalUnitName = Organizational Unit NamecommonName = Common NameemailAddress = Email Address# Optionally, specify some defaults.countryName_default = USstateOrProvinceName_default = OregonlocalityName_default =0.organizationName_default = OpenStackorganizationalUnitName_default = OctaviaemailAddress_default =commonName_default = example.org[ v3_ca ]# Extensions for a typical CA (`man x509v3_config`).subjectKeyIdentifier = hashauthorityKeyIdentifier = keyid:always,issuerbasicConstraints = critical, CA:truekeyUsage = critical, digitalSignature, cRLSign, keyCertSign[ usr_cert ]# Extensions for client certificates (`man x509v3_config`).basicConstraints = CA:FALSEnsCertType = client, emailnsComment = "OpenSSL Generated Client Certificate"subjectKeyIdentifier = hashauthorityKeyIdentifier = keyid,issuerkeyUsage = critical, nonRepudiation, digitalSignature, keyEnciphermentextendedKeyUsage = clientAuth, emailProtection[ server_cert ]# Extensions for server certificates (`man x509v3_config`).basicConstraints = CA:FALSEnsCertType = servernsComment = "OpenSSL Generated Server Certificate"subjectKeyIdentifier = hashauthorityKeyIdentifier = keyid,issuer:alwayskeyUsage = critical, digitalSignature, keyEnciphermentextendedKeyUsage = serverAuth[ crl_ext ]# Extension for CRLs (`man x509v3_config`).authorityKeyIdentifier=keyid:always
10.3 为server_CA与client_CA自建CA机构创建目录
mkdir client_camkdir server_ca
10.4 创建自建server_CA机构
10.4.1 为server_CA私钥准备目录与序列号文件
cd server_camkdir certs crl newcerts privatechmod 700 privatetouch index.txtecho 1000 > serial
10.4.2 创建server_CA私钥
openssl genrsa -aes256 -out private/ca.key.pem 4096
Enter pass phrase for private/ca.key.pem:servercaVerifying - Enter pass phrase for private/ca.key.pem:serverca
chmod 400 private/ca.key.pem
10.4.3 创建server_CA
openssl req -config ../openssl.cnf -key private/ca.key.pem -new -x509 -days 7300 -sha256 -extensions v3_ca -out certs/ca.cert.pem
Enter pass phrase for private/ca.key.pem:serverca---Country Name (2 letter code) [US]:saState or Province Name [Oregon]:saLocality Name []:saOrganization Name [OpenStack]:saOrganizational Unit Name [Octavia]:saCommon Name [example.org]:saEmail Address []:sa
10.5 创建自建client_CA机构
10.5.1 为client_CA私钥准备目录与序列号文件
cd ../client_camkdir certs crl csr newcerts privatechmod 700 privatetouch index.txtecho 1000 > serial
10.5.2 创建client_CA私钥
openssl genrsa -aes256 -out private/ca.key.pem 4096
Enter pass phrase for private/ca.key.pem:clientcaVerifying - Enter pass phrase for private/ca.key.pem:clientca
chmod 400 private/ca.key.pem
10.5.3 创建client_CA
openssl req -config ../openssl.cnf -key private/ca.key.pem -new -x509 -days 7300 -sha256 -extensions v3_ca -out certs/ca.cert.pem
Enter pass phrase for private/ca.key.pem:clientca-----Country Name (2 letter code) [US]:caState or Province Name [Oregon]:caLocality Name []:caOrganization Name [OpenStack]:caOrganizational Unit Name [Octavia]:caCommon Name [example.org]:caEmail Address []:ca
10.6 创建客户端私钥(controller请求证书使用)
openssl genrsa -aes256 -out private/client.key.pem 2048Generating RSA private key, 2048 bit long modulus (2 primes)...............................+++++........................................................................................+++++e is 65537 (0x010001)Enter pass phrase for private/client.key.pem:clientVerifying - Enter pass phrase for private/client.key.pem:client
openssl req -config ../openssl.cnf -new -sha256 -key private/client.key.pem -out csr/client.csr.pem
ent.key.pem -out csr/client.csr.pem:clientEnter pass phrase for private/client.key.pem:client-----Country Name (2 letter code) [US]:caState or Province Name [Oregon]:caLocality Name []:caOrganization Name [OpenStack]:caOrganizational Unit Name [Octavia]:caCommon Name [example.org]:caEmail Address []:ca
openssl ca -config ../openssl.cnf -extensions usr_cert -days 7300 -notext -md sha256 -in csr/client.csr.pem -out certs/client.cert.pem
Enter pass phrase for .//private/ca.key.pem:clientcaSignature okCertificate Details:Serial Number: 4096 (0x1000)ValidityNot Before: Feb 23 04:13:10 2021 GMTNot After : Feb 18 04:13:10 2041 GMTSubject:countryName = castateOrProvinceName = caorganizationName = caorganizationalUnitName = cacommonName = caemailAddress = caX509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Cert Type:SSL Client, S/MIMENetscape Comment:OpenSSL Generated Client CertificateX509v3 Subject Key Identifier:18:73:79:C5:20:30:7D:EB:F1:EF:8E:4B:62:F0:BB:24:2E:C0:E9:C2X509v3 Authority Key Identifier:keyid:5F:DD:60:96:60:6F:18:4F:FA:72:73:16:CB:4D:3F:83:57:19:58:B4X509v3 Key Usage: criticalDigital Signature, Non Repudiation, Key EnciphermentX509v3 Extended Key Usage:TLS Web Client Authentication, E-mail ProtectionCertificate is to be certified until Feb 18 04:13:10 2041 GMT (7300 days)Sign the certificate? [y/n]:y1 out of 1 certificate requests certified, commit? [y/n]yWrite out database with 1 new entriesData Base Updated
openssl rsa -in private/client.key.pem -out private/client.cert-and-key.pem
Enter pass phrase for private/client.key.pem:clientwriting RSA key
cd ..mkdir etc/octavia/certschmod 700 etc/octavia/certscp server_ca/private/ca.key.pem etc/octavia/certs/server_ca.key.pemchmod 700 etc/octavia/certs/server_ca.key.pemcp server_ca/certs/ca.cert.pem etc/octavia/certs/server_ca.cert.pemcp client_ca/certs/ca.cert.pem etc/octavia/certs/client_ca.cert.pemcp client_ca/private/client.cert-and-key.pem etc/octavia/certs/client.cert-and-key.pemchmod 700 etc/octavia/certs/client.cert-and-key.pemchown -R octavia.octavia etc/octavia/certs
openstack security group create lb-mgmt-sec-grpopenstack security group rule create --protocol icmp lb-mgmt-sec-grpopenstack security group rule create --protocol tcp --dst-port 22 lb-mgmt-sec-grpopenstack security group rule create --protocol tcp --dst-port 9443 lb-mgmt-sec-grpopenstack security group create lb-health-mgr-sec-grpopenstack security group rule create --protocol udp --dst-port 5555 lb-health-mgr-sec-grp
ssh-keygenopenstack keypair create --public-key ~/.ssh/id_rsa.pub mykey
cd $HOMEmkdir -m755 -p /etc/dhcp/octaviacp octavia/etc/dhcp/dhclient.conf /etc/dhcp/octavia
注意:此处配置文件为在controller启动一个dhcp服务进程使用,为lb-mgmt-net分配网络地址;
$ OCTAVIA_MGMT_SUBNET=172.16.0.0/12$ OCTAVIA_MGMT_SUBNET_START=172.16.0.100$ OCTAVIA_MGMT_SUBNET_END=172.16.31.254$ OCTAVIA_MGMT_PORT_IP=172.16.0.2$ openstack network create lb-mgmt-net$ openstack subnet create --subnet-range $OCTAVIA_MGMT_SUBNET --allocation-pool \start=$OCTAVIA_MGMT_SUBNET_START,end=$OCTAVIA_MGMT_SUBNET_END \--network lb-mgmt-net lb-mgmt-subnet$ SUBNET_ID=$(openstack subnet show lb-mgmt-subnet -f value -c id)$ PORT_FIXED_IP="--fixed-ip subnet=$SUBNET_ID,ip-address=$OCTAVIA_MGMT_PORT_IP"$ MGMT_PORT_ID=$(openstack port create --security-group \lb-health-mgr-sec-grp --device-owner Octavia:health-mgr \--host=$(hostname) -c id -f value --network lb-mgmt-net \$PORT_FIXED_IP octavia-health-manager-listen-port)$ MGMT_PORT_MAC=$(openstack port show -c mac_address -f value \$MGMT_PORT_ID)$ MGMT_PORT_IP=$(openstack port show -f yaml -c fixed_ips \$MGMT_PORT_ID | awk '{FS=",|";gsub(",","");gsub("'\''",""); \for(line = 1; line <= NF; ++line) {if ($line ~ ^- ip_address:/) \{split($line, word, " ");if (ENVIRON["IPV6_ENABLED"] == "" && word[3] ~ \./) \print word[3];if (ENVIRON["IPV6_ENABLED"] != "" && word[3] ~ :/) print word[3];} \else {split($line, word, " ");for(ind in word) {if (word[ind] ~ ^ip_address=/) \{split(word[ind], token, "=");if (ENVIRON["IPV6_ENABLED"] == "" && token[2] ~ \./) \print token[2];if (ENVIRON["IPV6_ENABLED"] != "" && token[2] ~ :/) print token[2];}}}}}')$ sudo ip link add o-hm0 type veth peer name o-bhm0$ NETID=$(openstack network show lb-mgmt-net -c id -f value)$ BRNAME=brq$(echo $NETID|cut -c 1-11)$ sudo brctl addif $BRNAME o-bhm0$ sudo ip link set o-bhm0 up$ sudo ip link set dev o-hm0 address $MGMT_PORT_MAC$ sudo iptables -I INPUT -i o-hm0 -p udp --dport 5555 -j ACCEPT$ sudo dhclient -v o-hm0 -cf etc/dhcp/octavia
[root@openstack-controller ~]# echo -e "$BRNAME\n""$MGMT_PORT_MAC"brq70844e37-07fa:16:3e:73:07:65
Tips:理论上lb-vip-net可以与tenant-net、lb-mgmt-net是同一个网络,但是生产中为了便于做安全控制,建议将lb-vip-net与tenant-net、lb-mgmt-net分离;
openstack network create lb-vip-netopenstack subnet create --subnet-range 10.10.10.0/24 --allocation-pool start=10.10.10.2,end=10.10.10.253 --network lb-vip-net lb-vip-subnetopenstack network set --share lb-vip-net
Tips:为了给vip绑定float-ip需要将lb-vip-subnet添加至provider路由器上,否则添加不成功;
openstack router add subnet router lb-vip-subnet
mkdir etc/systemd/network/ -pvcat >>/etc/systemd/network/o-hm0.network<<EOF[Match]Name=o-hm0[Network]DHCP=yesEOF
cat >>/etc/systemd/system/octavia-interface.service<<EOF[Unit]Description=Octavia Interface CreatorRequires=neutron-linuxbridge-agent.serviceAfter=neutron-linuxbridge-agent.service[Service]Type=oneshotRemainAfterExit=trueExecStart=/opt/octavia-interface.sh startExecStop=/opt/octavia-interface.sh stop[Install]WantedBy=multi-user.targetEOF
root@controller-01:~# systemctl enable octavia-interface.serviceroot@controller-01:~# systemctl status octavia-interface.service● octavia-interface.service - Octavia Interface CreatorLoaded: loaded (/etc/systemd/system/octavia-interface.service; enabled; vendor preset: enabled)Active: active (exited) since Wed 2021-02-24 14:23:59 UTC; 11min agoProcess: 8835 ExecStart=/opt/octavia-interface.sh start (code=exited, status=0/SUCCESS)Main PID: 8835 (code=exited, status=0/SUCCESS)
root@controller-01:~# cat opt/octavia-interface.sh#!/bin/bashset -exMAC=fa:16:3e:73:07:65BRNAME=brq70844e37-07if [ "$1" == "start" ]; thenip link add o-hm0 type veth peer name o-bhm0brctl addif $BRNAME o-bhm0ip link set o-bhm0 upip link set dev o-hm0 address $MACip link set o-hm0 upiptables -I INPUT -i o-hm0 -p udp --dport 5555 -j ACCEPTelif [ "$1" == "stop" ]; thenip link del o-hm0elsebrctl show $BRNAMEip a s dev o-hm0fi
root@controller-01:~# chmod a+x opt/octavia-interface.sh
root@controller-01:~# cat etc/octavia/octavia.conf | egrep -v "^#|^$"[DEFAULT]transport_url = rabbit://openstack:RABBIT_PASS@controller[amphora_agent][anchor][api_settings]bind_host = 0.0.0.0bind_port = 9876[audit][certificates]cert_generator = local_cert_generatorca_certificate = etc/octavia/certs/server_ca.cert.pemca_private_key = etc/octavia/certs/server_ca.key.pemca_private_key_passphrase = serverca[controller_worker]amp_image_owner_id = ded04e0f8ea5491582278519ce380edcamp_image_id = 898604dc-352f-4137-8da4-e448b04846b8amp_ssh_key_name = mykeyamp_secgroup_list = dd11e4dd-7ef3-4d36-bc84-634a9f5966cfamp_boot_network_list = 70844e37-07c6-436b-bc83-4e38e2678e8famp_flavor_id = 200network_driver = allowed_address_pairs_drivercompute_driver = compute_nova_driveramphora_driver = amphora_haproxy_rest_driverclient_ca = etc/octavia/certs/client_ca.cert.pemloadbalancer_topology = ACTIVE_STANDBY[database]connection = mysql+pymysql://octavia:OCTAVIA_DBPASS@controller/octavia[driver_agent][glance][haproxy_amphora]client_cert = etc/octavia/certs/client.cert-and-key.pemserver_ca = etc/octavia/certs/server_ca.cert.pem[health_manager]bind_port = 5555bind_ip = 172.16.0.2controller_ip_port_list = 172.16.0.2:5555[house_keeping][keepalived_vrrp][keystone_authtoken]www_authenticate_uri = http://controller:5000auth_url = http://controller:5000memcached_servers = controller:11211auth_type = passwordproject_domain_name = Defaultuser_domain_name = Defaultproject_name = serviceusername = octaviapassword = OCTAVIA[networking][neutron][nova][oslo_messaging]topic = octavia_prov[oslo_messaging_amqp][oslo_messaging_kafka][oslo_messaging_notifications][oslo_messaging_rabbit][quotas][service_auth]auth_url = http://controller:5000memcached_servers = controller:11211auth_type = passwordproject_domain_name = Defaultuser_domain_name = Defaultproject_name = serviceusername = octaviapassword = OCTAVIA[task_flow]
amp_image_owner_id=$(openstack project list|grep admin|awk '{print $2}')amp_secgroup_list=$(openstack security group list|grep lb-mgmt-sec-grp|awk '{print $2}')amp_boot_network_list=$(openstack network list|grep lb-mgmt-net|awk '{print $2}')
octavia-db-manage --config-file etc/octavia/octavia.conf upgrade head
root@controller-01:~# systemctl restart octavia-api octavia-health-manager octavia-housekeeping octavia-workerroot@controller-01:~# systemctl enable octavia-api octavia-health-manager octavia-housekeeping octavia-worker
git clone https://github.com/openstack/octavia-dashboard.git -b stable/traincd /root/octavia-dashboardpython3 setup.py installcd /root/octavia-dashboard/octavia_dashboard/enabledcp _1482_project_load_balancer_panel.py usr/share/openstack-dashboard/openstack_dashboard/enabled/cd /usr/share/openstack-dashboardecho yes| python3 manage.py collectstaticpython3 manage.py compresssystemctl restart apache2
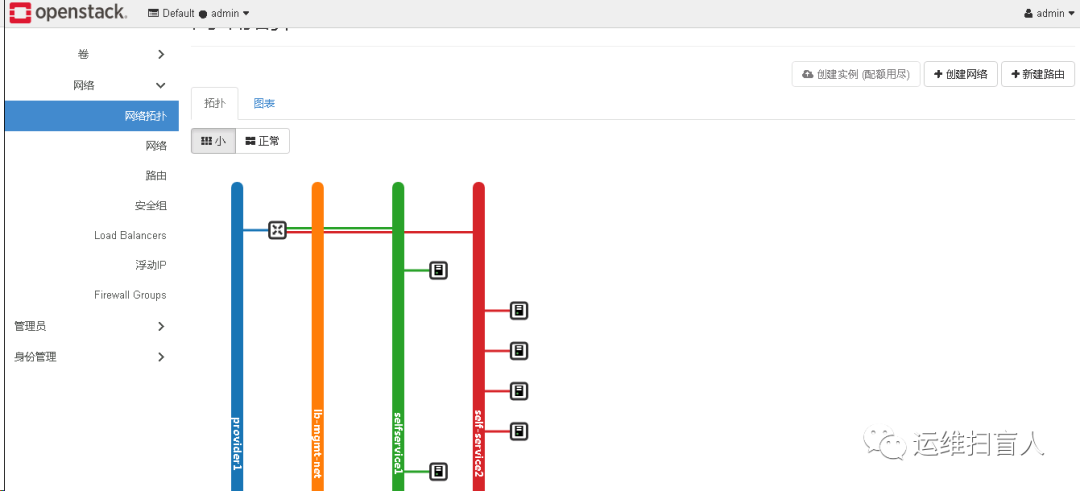
第二部分 openstack-octavia测试
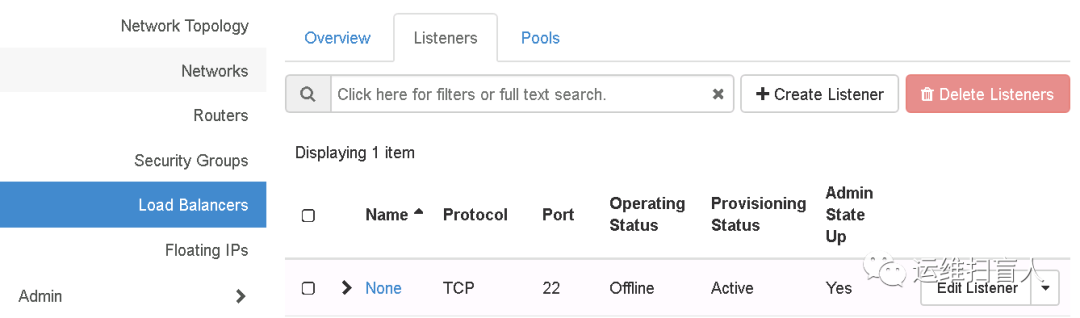
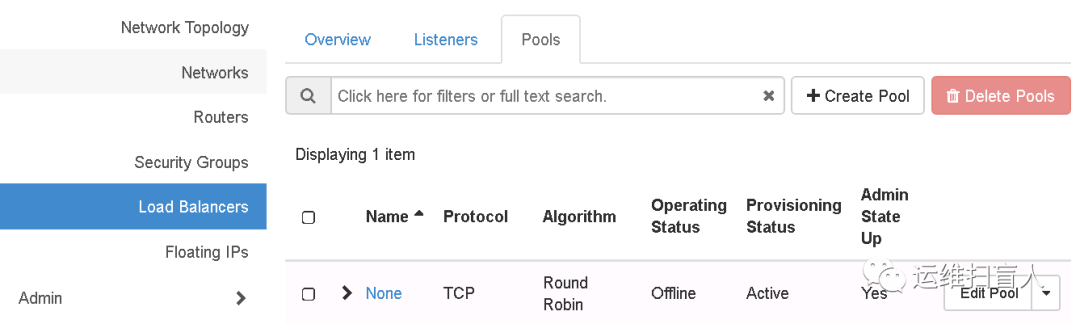
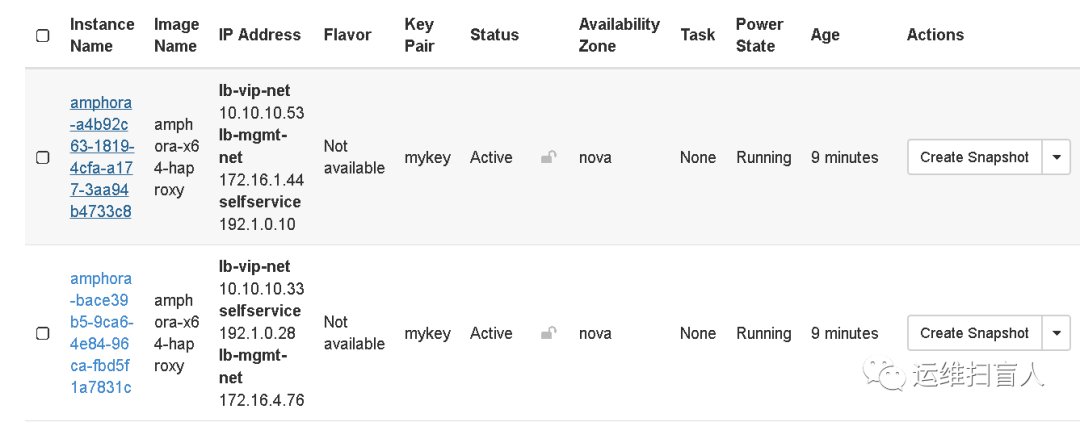
root@controller-01:~# ssh 172.16.1.44The authenticity of host '172.16.1.44 (172.16.1.44)' can't be established.ECDSA key fingerprint is SHA256:G02CH/UA1NW6UWOLdtaT2edVZPeJpucMKcKn4kJ+Ctw.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added '172.16.1.44' (ECDSA) to the list of known hosts.Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-135-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageThe programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in usr/share/doc/*/copyright.Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ifconfigens3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 172.16.1.44 netmask 255.240.0.0 broadcast 172.31.255.255inet6 fe80::f816:3eff:fe18:8ec8 prefixlen 64 scopeid 0x20<link>ether fa:16:3e:18:8e:c8 txqueuelen 1000 (Ethernet)RX packets 422 bytes 112187 (112.1 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 387 bytes 148484 (148.4 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns listamphora-haproxy (id: 0)root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy ifconfigeth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 10.10.10.53 netmask 255.255.255.0 broadcast 10.10.10.255ether fa:16:3e:db:be:e6 txqueuelen 1000 (Ethernet)RX packets 21 bytes 1194 (1.1 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 752 bytes 38092 (38.0 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0eth2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 192.1.0.10 netmask 255.255.255.0 broadcast 192.1.0.255ether fa:16:3e:c2:24:50 txqueuelen 1000 (Ethernet)RX packets 183 bytes 12886 (12.8 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 325 bytes 22322 (22.3 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
root@controller-01:~# ssh 172.16.4.76The authenticity of host '172.16.4.76 (172.16.4.76)' can't be established.ECDSA key fingerprint is SHA256:6UVkpWk1UCuuMNwh+S16222t4bOo7cRuddnuklnUUiA.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added '172.16.4.76' (ECDSA) to the list of known hosts.Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-135-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageThe programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in usr/share/doc/*/copyright.Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.root@amphora-bace39b5-9ca6-4e84-96ca-fbd5f1a7831c:~# ifconfigens3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 172.16.4.76 netmask 255.240.0.0 broadcast 172.31.255.255inet6 fe80::f816:3eff:fe0f:b2e6 prefixlen 64 scopeid 0x20<link>ether fa:16:3e:0f:b2:e6 txqueuelen 1000 (Ethernet)RX packets 475 bytes 114954 (114.9 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 407 bytes 151009 (151.0 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536inet 127.0.0.1 netmask 255.0.0.0inet6 ::1 prefixlen 128 scopeid 0x10<host>loop txqueuelen 1000 (Local Loopback)RX packets 0 bytes 0 (0.0 B)RX errors 0 dropped 0 overruns 0 frame 0TX packets 0 bytes 0 (0.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0root@amphora-bace39b5-9ca6-4e84-96ca-fbd5f1a7831c:~# ip netns listamphora-haproxy (id: 0)root@amphora-bace39b5-9ca6-4e84-96ca-fbd5f1a7831c:~# ip netns exec amphora-haproxy ifconfigeth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 10.10.10.33 netmask 255.255.255.0 broadcast 10.10.10.255ether fa:16:3e:44:ae:9f txqueuelen 1000 (Ethernet)RX packets 843 bytes 42706 (42.7 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 17 bytes 994 (994.0 B)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0eth2: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1450inet 192.1.0.28 netmask 255.255.255.0 broadcast 192.1.0.255ether fa:16:3e:8a:4d:f7 txqueuelen 1000 (Ethernet)RX packets 208 bytes 14724 (14.7 KB)RX errors 0 dropped 0 overruns 0 frame 0TX packets 364 bytes 24968 (24.9 KB)TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
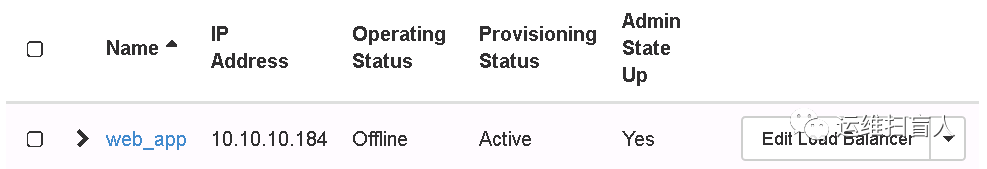
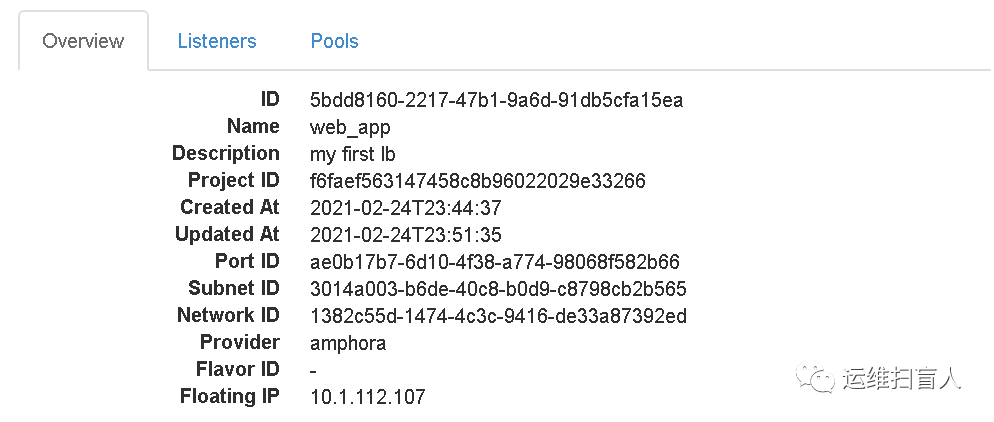
root@controller-01:~# openstack loadbalancer list+--------------------------------------+---------+----------------------------------+--------------+---------------------+----------+| id | name | project_id | vip_address | provisioning_status | provider |+--------------------------------------+---------+----------------------------------+--------------+---------------------+----------+| 5bdd8160-2217-47b1-9a6d-91db5cfa15ea | web_app | f6faef563147458c8b96022029e33266 | 10.10.10.184 | ACTIVE | amphora |+--------------------------------------+---------+----------------------------------+--------------+---------------------+----------+
root@controller-01:~# ssh cirros@10.1.112.107$ ifconfig eth0eth0 Link encap:Ethernet HWaddr FA:16:3E:71:A7:13inet addr:192.1.0.13 Bcast:172.31.255.255 Mask:255.240.0.0inet6 addr: fe80::f816:3eff:fe71:a713/64 Scope:LinkUP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1RX packets:1184 errors:0 dropped:0 overruns:0 frame:0TX packets:722 errors:0 dropped:0 overruns:0 carrier:0collisions:0 txqueuelen:1000RX bytes:101839 (99.4 KiB) TX bytes:68945 (67.3 KiB)root@controller-01:~# ssh cirros@10.1.112.107$ ifconfig eth0eth0 Link encap:Ethernet HWaddr FA:16:3E:AB:60:95inet addr:192.1.0.144 Bcast:172.31.255.255 Mask:255.240.0.0inet6 addr: fe80::f816:3eff:feab:6095/64 Scope:LinkUP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1RX packets:1395 errors:0 dropped:0 overruns:0 frame:0TX packets:891 errors:0 dropped:0 overruns:0 carrier:0collisions:0 txqueuelen:1000RX bytes:126126 (123.1 KiB) TX bytes:90362 (88.2 KiB
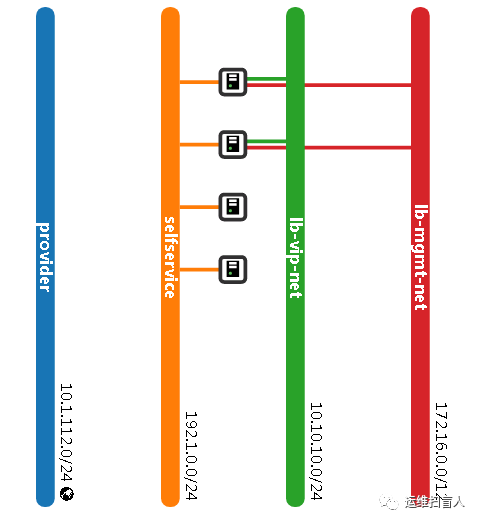
第三部分 openstack-octavia原理分析
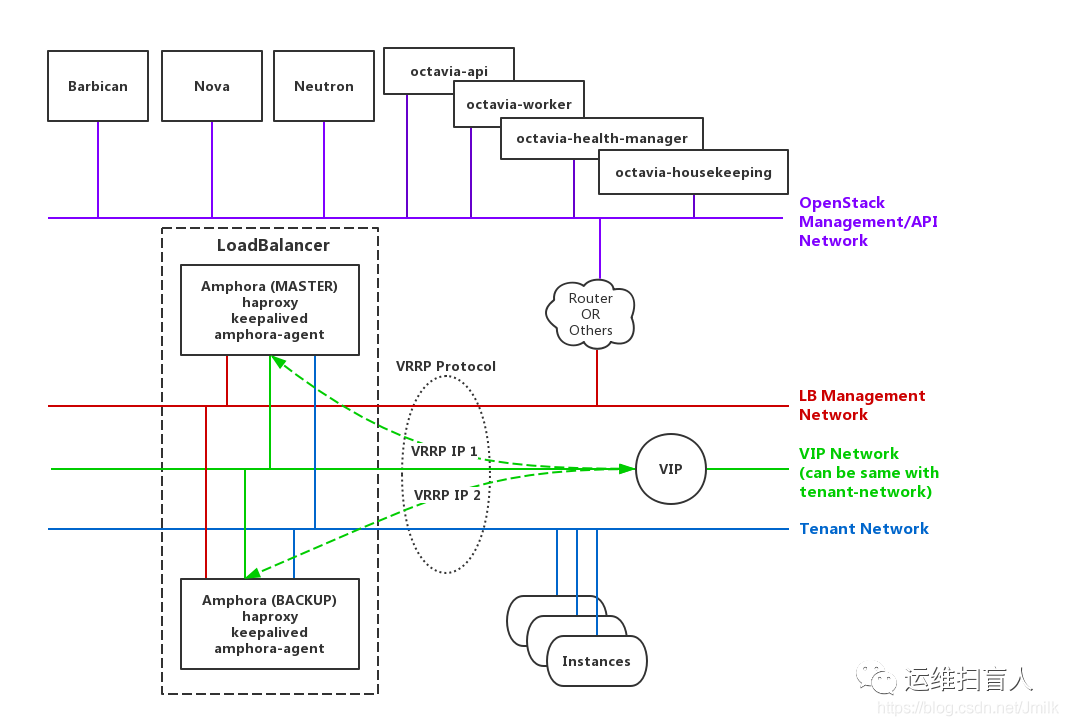
Amphora(e):实体为云主机,作为负载均衡器的载体,运行amphora-agent、haproxy、keepalived服务进程,也是 Octavia 的 Default Loadbalancer Provider。
lb-mgmt-net:是一个与 OpenStack Management/API Network 打通的网络,东侧连接 Amphora Instance、西侧连接 Octavia 服务进程。
tenant-net:业务云主机所在的网络。
vip-net:提供 VIP 地址池的网络。
Listener:下属于 loadbalancer 的监听器,用户可配置监听外部对 VIP 的访问类型(e.g. 协议、端口)。
Pool:后端的真实业务云主机集群域,一般用户会根据云主机的业务类型进行划分。
Member:业务云主机,下属于 Pool,对应传统负载均衡体系中的 Real Server。
Health Monitor:挂靠于 Pool,周期性对 Pool 中的 Member(s) 进行健康检查。
二、Octavia Amphora Provider 设计思路
Amphora 作为负载均衡器软件(HAProxy)和高可用支撑(Keepalived)的运行载体,通过 Agent 与 Octavia 服务进程通信
Octavia 服务进程接收到用户的 loadbalancer 和 VIP 的配置参数,通过 Agent 动态修改 haproxy、keepalived 的配置文件;
将 Member 处于的 Subnet 接入 Amphora,Amphora 通过 Member Socket (IP, Port) 分发请求数据包。
octavia controller worker服务是octavia服务任务的管理者;octavia-health-manager 监听于UDP 5555口,接收amphora-agent发送的来自pool member的健康检测信息;amphora-agent 作为octavia service与amphora(haproxy、keepalived)的通信中介, 监听于TCP 9443端口。
amphora 被分配到 loadbalancer 之后会添加一个 vrrp_port 类型的端口,vrrp_port 充当着 keepalived 虚拟路由的一张网卡,被注入到 namespace 中,一般是 eth1。
只有当octavia.conf配置文件loadbalancer_topology = ACTIVE_STANDBY(默认为SINGLE),创建loadbalancer时才会创建两个amphora instance,在并且在vip-net创建两个vrrp-port,作为keepalived VIP漂移的载体,;
2.1 amphora-agent服务
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ps -ef | grep agentroot 1055 885 0 09:08 ? 00:00:01 /opt/amphora-agent-venv/bin/python3 /usr/local/bin/amphora-agent --config-file /etc/octavia/amphora-agent.conf
2.2 amphora-agent服务配置文件
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# cat /etc/octavia/amphora-agent.conf[DEFAULT]debug = False[haproxy_amphora]base_cert_dir = /var/lib/octavia/certsbase_path = /var/lib/octaviabind_host = ::bind_port = 9443haproxy_cmd = /usr/sbin/haproxyrespawn_count = 2respawn_interval = 2use_upstart = True[health_manager]controller_ip_port_list = 172.16.0.2:5555heartbeat_interval = 10heartbeat_key = None[amphora_agent]agent_server_ca = /etc/octavia/certs/client_ca.pemagent_server_cert = /etc/octavia/certs/server.pemagent_request_read_timeout = 180amphora_id = a4b92c63-1819-4cfa-a177-3aa94b4733c8amphora_udp_driver = keepalived_lvs[controller_worker]
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy cat /etc/network/interfaces.d/eth1.cfg# Generated by Octavia agentauto eth1iface eth1 inet staticaddress 10.10.10.53broadcast 10.10.10.255netmask 255.255.255.0gateway 10.10.10.1mtu 1450# Add a source routing table to allow members to access the VIPpost-up /sbin/ip route add default via 10.10.10.1 dev eth1 onlink table 1post-down /sbin/ip route del default via 10.10.10.1 dev eth1 onlink table 1post-up /sbin/iptables -t nat -A POSTROUTING -p udp -o eth1 -j MASQUERADEpost-down /sbin/iptables -t nat -D POSTROUTING -p udp -o eth1 -j MASQUERADEr
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy ps -ef | grep haproxyroot 876 1 0 09:07 ? 00:00:01 /usr/sbin/haproxy -Ws -f /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea/haproxy.cfg -f /var/lib/octavia/haproxy-default-user-group.conf -p /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea/5bdd8160-2217-47b1-9a6d-91db5cfa15ea.pid -L D7Zb3aIHaBtpilTdpYmeQlsG43Mnobody 888 876 0 09:07 ? 00:00:03 /usr/sbin/haproxy -Ws -f /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea/haproxy.cfg -f /var/lib/octavia/haproxy-default-user-group.conf -p /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea/5bdd8160-2217-47b1-9a6d-91db5cfa15ea.pid -L D7Zb3aIHaBtpilTdpYmeQlsG43M
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# cat /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea/haproxy.cfg# Configuration for loadbalancer 5bdd8160-2217-47b1-9a6d-91db5cfa15eaglobaldaemonuser nobodylog /dev/log local0log /dev/log local1 noticestats socket /var/lib/octavia/5bdd8160-2217-47b1-9a6d-91db5cfa15ea.sock mode 0666 level usermaxconn 1000000defaultslog globalretries 3option redispatchoption splice-requestoption splice-responseoption http-keep-alivepeers 5bdd8160221747b19a6d91db5cfa15ea_peerspeer D7Zb3aIHaBtpilTdpYmeQlsG43M 10.10.10.53:1025peer Trkzl9Yy82h2pRzpLnulpBCb0WM 10.10.10.33:1025frontend 460eccd0-2014-4c6c-b50c-80152b73fd56option tcplogmaxconn 1000000bind 10.10.10.184:22mode tcpdefault_backend 331026f7-1e79-4642-af9d-94c189f24c29:460eccd0-2014-4c6c-b50c-80152b73fd56timeout client 50000backend 331026f7-1e79-4642-af9d-94c189f24c29:460eccd0-2014-4c6c-b50c-80152b73fd56mode tcpbalance roundrobintimeout check 5sfullconn 1000000option allbackupstimeout connect 5000timeout server 50000server 2705c383-1f93-4947-b09d-5c052d484f5f 192.1.0.13:22 weight 1 check inter 5s fall 3 rise 3server 515ed29e-eda4-42c4-8b27-0d5c6add1a91 192.1.0.144:22 weight 1 check inter 5s fall 3 rise 3
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy cat /lib/systemd/system/haproxy.service[Unit]Description=HAProxy Load BalancerDocumentation=man:haproxy(1)Documentation=file:/usr/share/doc/haproxy/configuration.txt.gzAfter=network.target rsyslog.service[Service]EnvironmentFile=-/etc/default/haproxyEnvironment="CONFIG=/etc/haproxy/haproxy.cfg" "PIDFILE=/run/haproxy.pid"ExecStartPre=/usr/sbin/haproxy -f $CONFIG -c -q $EXTRAOPTSExecStart=/usr/sbin/haproxy -Ws -f $CONFIG -p $PIDFILE $EXTRAOPTSExecReload=/usr/sbin/haproxy -f $CONFIG -c -q $EXTRAOPTSExecReload=/bin/kill -USR2 $MAINPIDKillMode=mixedRestart=alwaysSuccessExitStatus=143Type=notify# The following lines leverage SystemD's sandboxing options to provide# defense in depth protection at the expense of restricting some flexibility# in your setup (e.g. placement of your configuration files) or possibly# reduced performance. See systemd.service(5) and systemd.exec(5) for further# information.# NoNewPrivileges=true# ProtectHome=true# If you want to use 'ProtectSystem=strict' you should whitelist the PIDFILE,# any state files and any other files written using 'ReadWritePaths' or# 'RuntimeDirectory'.# ProtectSystem=true# ProtectKernelTunables=true# ProtectKernelModules=true# ProtectControlGroups=true# If your SystemD version supports them, you can add: @reboot, @swap, @sync# SystemCallFilter=~@cpu-emulation @keyring @module @obsolete @raw-io[Install]WantedBy=multi-user.target
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy ps -ef | grep keepalivedroot 892 1 0 09:07 ? 00:00:00 /usr/sbin/keepalived --log-facility=1 -f /var/lib/octavia/vrrp/octavia-keepalived.conf -p /var/lib/octavia/vrrp/octavia-keepalived.pidroot 893 892 0 09:07 ? 00:00:00 /usr/sbin/keepalived --log-facility=1 -f /var/lib/octavia/vrrp/octavia-keepalived.conf -p /var/lib/octavia/vrrp/octavia-keepalived.pid
master
root@amphora-bace39b5-9ca6-4e84-96ca-fbd5f1a7831c:~# ip netns exec amphora-haproxy cat /var/lib/octavia/vrrp/octavia-keepalived.confvrrp_script check_script {script /var/lib/octavia/vrrp/check_script.shinterval 5fall 2rise 2}vrrp_instance 5bdd8160221747b19a6d91db5cfa15ea {state MASTERinterface eth1virtual_router_id 1priority 100nopreemptacceptgarp_master_refresh 5garp_master_refresh_repeat 2advert_int 1authentication {auth_type PASSauth_pass ec74379}unicast_src_ip 10.10.10.33unicast_peer {10.10.10.53}virtual_ipaddress {10.10.10.184}virtual_routes {10.10.10.0/24 dev eth1 src 10.10.10.184 scope link table 1}virtual_rules {from 10.10.10.184/32 table 1 priority 100}track_script {check_script}}
backup
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy cat /var/lib/octavia/vrrp/octavia-keepalived.confvrrp_script check_script {script /var/lib/octavia/vrrp/check_script.shinterval 5fall 2rise 2}vrrp_instance 5bdd8160221747b19a6d91db5cfa15ea {state BACKUPinterface eth1virtual_router_id 1priority 90nopreemptacceptgarp_master_refresh 5garp_master_refresh_repeat 2advert_int 1authentication {auth_type PASSauth_pass ec74379}unicast_src_ip 10.10.10.53unicast_peer {10.10.10.33}virtual_ipaddress {10.10.10.184}virtual_routes {10.10.10.0/24 dev eth1 src 10.10.10.184 scope link table 1}virtual_rules {from 10.10.10.184/32 table 1 priority 100}track_script {check_script}}
root@amphora-a4b92c63-1819-4cfa-a177-3aa94b4733c8:~# ip netns exec amphora-haproxy cat /lib/systemd/system/keepalived.service[Unit]Description=Keepalive Daemon (LVS and VRRP)After=syslog.target network-online.targetWants=network-online.target# Only start if there is a configuration fileConditionFileNotEmpty=/etc/keepalived/keepalived.conf[Service]Type=forkingKillMode=process# Read configuration variable file if it is presentEnvironmentFile=-/etc/default/keepalivedExecStart=/usr/sbin/keepalived $DAEMON_ARGSExecReload=/bin/kill -HUP $MAINPID[Install]WantedBy=multi-user.target
root@amphora-bace39b5-9ca6-4e84-96ca-fbd5f1a7831c:~# ip netns exec amphora-haproxy cat /var/lib/octavia/vrrp/check_script.sh#!/bin/bash# Don't try to run the directory when it is emptyshopt -s nullglobstatus=0for file in /var/lib/octavia/vrrp/check_scripts/*doecho "Running check script: " $filesh $filestatus=$(( $status + $? ))doneexit $status






