
5G的兴起带动IT互联网技术的变革和走向,带来泛在接入,为解决当前边缘领域面临的挑战,边缘计算由此而生。
KubeEdge是一个开源的边缘计算平台,基于Kubernetes实现了云边协同、计算下沉、海量边缘设备管理、边缘自治等能力,最近也晋升为CNCF孵化级托管项目。笔者也是它的忠实粉丝,之前也有介绍过,实际上在我们物联网业务的应用场景中一直有试用和探索。
在物联网生态中,还有扮演着重要角色的边缘端操作系统。Canonical公司推出物联网生态系统和嵌入式设备的Ubuntu Core 操作系统,Ubuntu Core使用了革命性的Snap通用软件包格式,旨在降低安全维护成本和软件开发风险,事实上ubuntu core也是一个snap包,默认安装的软件包较少,仅200多M,可最大限度地减少攻击面,它受到戴尔,英特尔,高通,三星,恩智浦和Rigado等各种物联网设备的支持。
如果说KubeEdge把Kubernetes的能力延伸到边缘,那么Ubuntu Core就是Linux在物联网领域的扩展。
KubeEdge 云端安装
使用Keadm进行部署KubeEdge的云和边缘组件,它不负责安装K8s和容器运行时,因此需要具备先决条件,对于云端而言需要正确配置kubeconfig,通常在 ${HOME}/.kube/config
Step 1: 安装Keadm
# wget https://github.com/kubeedge/kubeedge/releases/download/v1.4.0/keadm-v1.4.0-linux-amd64.tar.gz
# tar -zxvf keadm-v1.4.0-linux-amd64.tar.gz
# mv keadm-v1.4.0-linux-amd64/keadm/keadm /usr/local/bin/
Step 2: 初始化cloudcore
# keadm init --advertise-address="47.242.xx.xx"
--advertise-address 参数指定云节点的公共IP,云服务器为公网IP
cloudcore初始化成功后,会在Kubernetes创建4个CRD资源,和kubeedge命名空间,并在该空间下创建了三个secrets
root@k8s-test99:~# kubectl get crd | grep kubeedge.io
clusterobjectsyncs.reliablesyncs.kubeedge.io 2020-11-13T06:53:09Z
devicemodels.devices.kubeedge.io 2020-11-13T06:53:08Z
devices.devices.kubeedge.io 2020-11-13T06:53:08Z
objectsyncs.reliablesyncs.kubeedge.io 2020-11-13T06:53:09Z
root@k8s-test99:~# kubectl -n kubeedge get secrets
NAME TYPE DATA AGE
casecret Opaque 2 31h
cloudcoresecret Opaque 2 31h
default-token-6dzfc kubernetes.io/service-account-token 3 31h
tokensecret Opaque 1 31h
其中tokensecret是KubeEdge边缘端接入token,可以使用keadm 或 kubectl 命令获取
root@k8s-test99:~# keadm gettoken
3385553490654fb476eae55a1819a3dfeec44b76bddc563b15a3c0580107a25a.eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2MDUzMzc3NzR9.OCvedXKDJfCBfT_jAtDOnI8_7KZebYa05EQ_G27xGb4
root@k8s-test99:~# kubectl get secret -nkubeedge tokensecret -o=jsonpath='{.data.tokendata}' | base64 -d
3385553490654fb476eae55a1819a3dfeec44b76bddc563b15a3c0580107a25a.eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2MDUzMzc3NzR9.OCvedXKDJfCBfT_jAtDOnI8_7KZebYa05EQ_G27xGb4
root@k8s-test99:~#
Step 3: 使用systemd管理cloudcore(可选)
cloudcore的默认的配置文件在 /etc/kubeedge/config/cloudcore.yaml
# vim /usr/lib/systemd/system/cloudcore.service
[Unit]
Description=cloudcore.service
[Service]
Type=simple
ExecStart=/usr/local/bin/cloudcore > /var/log/kubeedge/cloudcore.log 2>&1
Restart=always
RestartSec=10
[Install]
WantedBy=multi-user.target
# systemctl daemon-reload
# systemctl enable cloudcore
# systemctl start cloudcore
# systemctl status cloudcore
Step 4: 启用kubectl logs功能(可选)
从仓库复制证书生成脚本
root@k8s-test99:~# git clone https://github.com/kubeedge/kubeedge
root@k8s-test99:~# cp /tmp/kubeedge/build/tools/certgen.sh /etc/kubeedge/
确保/etc/kubernetes/pki/目录有ca.crt和ca.key
root@k8s-test99:~# ls /etc/kubernetes/pki/ca*
/etc/kubernetes/pki/ca.crt /etc/kubernetes/pki/ca.key /etc/kubernetes/pki/ca.srl
指定cloudcore的地址,云服务器指定公网IP
export CLOUDCOREIPS="47.242.xx.xx"
生成证书
root@k8s-test99:~# cd /etc/kubeedge/
root@k8s-test99:/etc/kubeedge# ./certgen.sh stream
root@k8s-test99:/etc/kubeedge# tree
.
├── ca
│ └── streamCA.crt
├── certgen.sh
├── certs
│ ├── stream.crt
│ ├── stream.csr
│ └── stream.key
├── config
│ └── cloudcore.yaml
在kube-apiserver的服务器上设置iptables转发规则
root@k8s-test99:~# iptables -t nat -A OUTPUT -p tcp --dport 10350 -j DNAT --to $CLOUDCOREIPS:10003
开启cloudcore cloudStream功能,并重启cloudcore
root@k8s-test99:~# vi /etc/kubeedge/config/cloudcore.yaml
cloudStream:
enable: true
root@k8s-test99:~# systemctl restart cloudcore
Step 5: 启用Metrics server功能(可选)
该功能点的实现重用了cloudstream和edgestream模块,需要执行开启kubectl logs功能的步骤。
克隆 metrics server 仓库
root@k8s-test99:~# git clone https://github.com/kubernetes-sigs/metrics-server.git
root@k8s-test99:~# cd metrics-server/manifests/base/
可以选择build镜像,本文没有选择
cd metrics-server
make container
编辑deployment.yaml文件
1、metrics server 需要运行在kube-apiserver节点;
2、metrics server 需要使用hostnetwork网络模式;
3、metrics server 需要开启kubelet-use-node-status-port功能;
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: metrics-server
namespace: kube-system
spec:
replicas: 1
selector:
matchLabels:
k8s-app: metrics-server
strategy:
rollingUpdate:
maxUnavailable: 0
template:
metadata:
labels:
k8s-app: metrics-server
spec:
affinity:
nodeAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
nodeSelectorTerms:
- matchExpressions:
- key: node-role.kubernetes.io/master
operator: In
values:
- k8s-test99
serviceAccountName: metrics-server
volumes:
# mount in tmp so we can safely use from-scratch images and/or read-only containers
- name: tmp-dir
emptyDir: {}
priorityClassName: system-cluster-critical
hostNetwork: true
containers:
- name: metrics-server
image: gcr.io/k8s-staging-metrics-server/metrics-server:master
imagePullPolicy: IfNotPresent
args:
- --cert-dir=/tmp
- --secure-port=4443
- --v=2
- --kubelet-insecure-tls
- --kubelet-preferred-address-types=InternalDNS,InternalIP,ExternalIP,Hostname
- --kubelet-use-node-status-port
ports:
- name: https
containerPort: 4443
protocol: TCP
readinessProbe:
httpGet:
path: /readyz
port: https
scheme: HTTPS
periodSeconds: 10
failureThreshold: 3
livenessProbe:
httpGet:
path: /livez
port: https
scheme: HTTPS
periodSeconds: 10
failureThreshold: 3
securityContext:
readOnlyRootFilesystem: true
runAsNonRoot: true
runAsUser: 1000
volumeMounts:
- name: tmp-dir
mountPath: /tmp
nodeSelector:
kubernetes.io/os: linux
---
apiVersion: v1
kind: Service
metadata:
name: metrics-server
namespace: kube-system
spec:
ports:
- name: https
port: 443
protocol: TCP
targetPort: https
selector:
k8s-app: metrics-server
创建metrics server
root@k8s-test99:~/metrics-server/manifests/base#
root@k8s-test99:~/metrics-server/manifests/base# tree
.
├── apiservice.yaml
├── deployment.yaml
├── kustomization.yaml
├── rbac.yaml
└── service.yaml
0 directories, 5 files
root@k8s-test99:~/metrics-server/manifests/base# kubectl create -f .
root@k8s-test99:~/metrics-server/manifests/base# kubectl -n kube-system get po --selector=k8s-app=metrics-server
NAME READY STATUS RESTARTS AGE
metrics-server-8cf664b9b-5xwpv 1/1 Running 0 15m
KubeEdge 边缘端安装
使用Keadm进行部署,需要先安装容器运行时,默认为docker。
Step 1: 安装Keadm
[root@edge-test001 ~]# wget https://github.com/kubeedge/kubeedge/releases/download/v1.4.0/keadm-v1.4.0-linux-amd64.tar.gz
[root@edge-test001 ~]# tar -zxvf keadm-v1.4.0-linux-amd64.tar.gz
[root@edge-test001 ~]# mv keadm-v1.4.0-linux-amd64/keadm/keadm /usr/local/bin/
Step 2: 加入边缘节点
[root@edge-test001 ~]# keadm join --cloudcore-ipport=47.242.xx.xx:10000 --token=3385553490654fb476eae55a1819a3dfeec44b76bddc563b15a3c0580107a25a.eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2MDUzMzc3NzR9.OCvedXKDJfCBfT_jAtDOnI8_7KZebYa05EQ_G27xGb4
1.3版本后,无需再从云端拷贝证书文件到边缘端,亦无需手动创建node节点,都会自动完成。在拥有大量边缘终端的时候,这功能很实用。
Step 3: 在云端检查该边缘端是否加入
root@k8s-test99:~# kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
edge-test001 Ready agent,edge 32h v1.18.6-kubeedge-v1.4.0 172.31.250.219 <none> CentOS Linux 8 (Core) 4.18.0-193.14.2.el8_2.x86_64 docker://19.3.13
edge-test002 NotReady agent,edge 31h v1.18.6-kubeedge-v1.4.0 172.20.61.119 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
edge-test003 NotReady agent,edge 30h v1.18.6-kubeedge-v1.4.0 172.18.46.55 <none> CentOS Linux 7 (Core) 3.10.0-693.2.2.el7.x86_64 docker://18.6.1
k8s-test99 Ready master 32h v1.19.4 172.31.250.218 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
可以看到edge-test001已成功加入。(笔者写文章时候与操作有时间间隔)
Step 4: 在边缘端启用kubectl logs功能(可选)
开启edgecore cloudStream功能,并重启edgecore。
root@edge-test001 ~]# cd /etc/kubeedge/
[root@edge-test001 kubeedge]# vi config/edgecore.yaml
edgeStream:
enable: true
handshakeTimeout: 30
readDeadline: 15
server: 47.242.xx.xx:10004
tlsTunnelCAFile: /etc/kubeedge/ca/rootCA.crt
tlsTunnelCertFile: /etc/kubeedge/certs/server.crt
tlsTunnelPrivateKeyFile: /etc/kubeedge/certs/server.key
writeDeadline: 15[root@edge-test001 kubeedge]# systemctl restart edgecore.service
Step 5: 在云端创建pod验证
创建测试的deploy,定义反亲和性,pod调度到edge节点
root@k8s-test99:~# cat demo.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx
labels:
app: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
affinity:
nodeAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
nodeSelectorTerms:
- matchExpressions:
- key: node-role.kubernetes.io/master
operator: DoesNotExist
containers:
- name: nginx
image: nginx:1.19.4-alpine
ports:
- containerPort: 80
hostPort: 80
root@k8s-test99:~# kubectl create -f demo.yaml
deployment.apps/nginx created
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 0/1 Pending 0 4s <none> edge-test001 <none> <none>
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 9s 172.17.0.2 edge-test001 <none> <none>
root@k8s-test99:~#
到边缘端查看容器
[root@edge-test001 ~]# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
4087353ee74c e5dcd7aa4b5e "/docker-entrypoint.…" About a minute ago Up About a minute k8s_nginx_nginx-6bc4cff87d-c6ln7_default_626a0d86-1752-4fb2-9d7d-da91bd61f759_0
bd59aa68fa63 kubeedge/pause:3.1 "/pause" About a minute ago Up About a minute 0.0.0.0:80->80/tcp k8s_POD_nginx-6bc4cff87d-c6ln7_default_626a0d86-1752-4fb2-9d7d-da91bd61f759_0
验证kubectl logs功能
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 2m59s 172.17.0.2 edge-test001 <none> <none>
root@k8s-test99:~# kubectl logs -f nginx-6bc4cff87d-c6ln7
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
10-listen-on-ipv6-by-default.sh: Getting the checksum of /etc/nginx/conf.d/default.conf
10-listen-on-ipv6-by-default.sh: Enabled listen on IPv6 in /etc/nginx/conf.d/default.conf
/docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh
/docker-entrypoint.sh: Configuration complete; ready for start up
验证metrics server功能
root@k8s-test99:~# kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
edge-test001 Ready agent,edge 34h v1.18.6-kubeedge-v1.4.0 172.31.250.219 <none> CentOS Linux 8 (Core) 4.18.0-193.14.2.el8_2.x86_64 docker://19.3.13
edge-test002 NotReady agent,edge 33h v1.18.6-kubeedge-v1.4.0 172.20.61.119 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
edge-test003 NotReady agent,edge 32h v1.18.6-kubeedge-v1.4.0 172.18.46.55 <none> CentOS Linux 7 (Core) 3.10.0-693.2.2.el7.x86_64 docker://18.6.1
k8s-test99 Ready master 34h v1.19.4 172.31.250.218 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
root@k8s-test99:~# kubectl top nodes
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
edge-test001 27m 0% 1364Mi 17%
k8s-test99 241m 6% 2555Mi 32%
edge-test003 <unknown> <unknown> <unknown> <unknown>
edge-test002 <unknown> <unknown> <unknown> <unknown>
root@k8s-test99:~#
在线的节点都可以获取到系统的资源
在Ubuntu Core安装KubeEdge
在KVM上安装Ubuntu Core用于测试,需要一个Ubuntu SSO账号,用于安装和ssh登陆。

Step 1: 安装Ubuntu Core
安装KVM,需要cpu开启虚拟化
prodan@ubuntu:~$ egrep 'vmx|svm' /proc/cpuinfo | wc -l
4
prodan@ubuntu:~$ sudo apt install qemu-kvm
正在读取软件包列表... 完成
正在分析软件包的依赖关系树
正在读取状态信息... 完成
qemu-kvm 已经是最新版 (1:4.2-3ubuntu6.8)。
升级了 0 个软件包,新安装了 0 个软件包,要卸载 0 个软件包,有 0 个软件包未被升级。
prodan@ubuntu:~$ kvm-ok
INFO: /dev/kvm exists
KVM acceleration can be used
prodan@ubuntu:~$
创建并启动kvm虚拟机
prodan@ubuntu:~$ wget https://cdimage.ubuntu.com/ubuntu-core/18/stable/current/ubuntu-core-18-amd64.img.xz
prodan@ubuntu:~$ unxz ubuntu-core-18-amd64.img.xz
prodan@ubuntu:~$ kvm -smp 2 -m 1500 -netdev user,id=mynet0,hostfwd=tcp::8022-:22,hostfwd=tcp::8090-:80 -device virtio-net-pci,netdev=mynet0 -vga qxl -drive file=ubuntu-core-18-amd64.img,format=raw
虚拟机22端口映射到本地8022端口;
虚拟机80端口映射到本地8090端口;
-vga qxl 设置半虚拟图形驱动程序qxl;
安装比较简单,输入Ubuntu SSO账号即可
Step 2: 在Ubuntu Core安装docker
通过ssh -p 8022 <Ubuntu SSO user name>@localhost登陆
prodan@ubuntu:~/kvm$ ssh -p 8022 test@localhost
Welcome to Ubuntu Core 18 (GNU/Linux 4.15.0-112-generic x86_64)
* Ubuntu Core: https://www.ubuntu.com/core
* Community: https://forum.snapcraft.io
* Snaps: https://snapcraft.io
This Ubuntu Core 18 machine is a tiny, transactional edition of Ubuntu,
designed for appliances, firmware and fixed-function VMs.
If all the software you care about is available as snaps, you are in
the right place. If not, you will be more comfortable with classic
deb-based Ubuntu Server or Desktop, where you can mix snaps with
traditional debs. It's a brave new world here in Ubuntu Core!
Please see 'snap --help' for app installation and updates.
Last login: Fri Nov 13 09:51:39 2020 from 10.0.2.2
通过snap安装docker,snap目前没有国内源,可以设置自己的代理。
$ sudo su -
root@localhost:~# cat /etc/systemd/system/snapd.service
[Service]
Environment=http_proxy=http://192.168.1.6:8880
Environment=https_proxy=http://192.168.1.6:8880
安装docker
root@localhost:~# snap install docker
Step 3: 使用docker安装mosquitto
root@localhost:~# docker run -d --net host --restart=always --name=mosquitto eclipse-mosquitto:1.6.12
7f3859fb0063a1be51edeed156b89f7dcfe230851be4a98a9f38da09d83ffb63
root@localhost:~# docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
7f3859fb0063 eclipse-mosquitto:1.6.12 "/docker-entrypoint.…" 3 seconds ago Up 3 seconds mosquitto
root@localhost:~#
Step 4: 使用docker安装edgecore
Ubuntu Core因为安全原因文件系统的权限控制很严格,重要的目录如/etc,/var等只有只读权限。edgecore默认存储pods信息的目录是/var/lib/edged,但是该目录是只读的,所以需要改下源码,重新编译成二进制包
修改edge/pkg/edged/edged.go源码
DefaultRootDir = "/var/lib/snapd/edged"
构建edgecore镜像
[root@edge-test001 kubeedge]# cat Dockerfile
FROM debian:stretch-slim
RUN apt-get update && apt-get install apt-transport-https ca-certificates curl gnupg-agent iptables software-properties-common -y \
&& curl -fsSL https://download.docker.com/linux/debian/gpg | apt-key add - \
&& add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/debian $(lsb_release -cs) stable" \
&& apt-get update \
&& apt-get install docker-ce-cli -y \
&& apt-get remove apt-transport-https curl gnupg-agent software-properties-common -y \
&& apt-get clean
ADD edgecore /usr/local/bin/edgecore
ENTRYPOINT ["edgecore"]
[root@edge-test001 kubeedge]# docker build -t kubeedge/edgecore:v1.4.0 .
初始化配置文件
root@localhost:~# mkdir -p /mnt/kubeedge/config/
root@localhost:~# docker run -it --net host --rm --name=edgecore-init --privileged=true --hostname=ubuntu-core-test01 \
> -v /var/run/docker.sock:/var/run/docker.sock \
> kubeedge/edgecore:v1.4.0 --defaultconfig >/mnt/kubeedge/config/edgecore.yaml
root@localhost:~#
编辑配置文件,设置server|httpServer|token并开启edgeStream
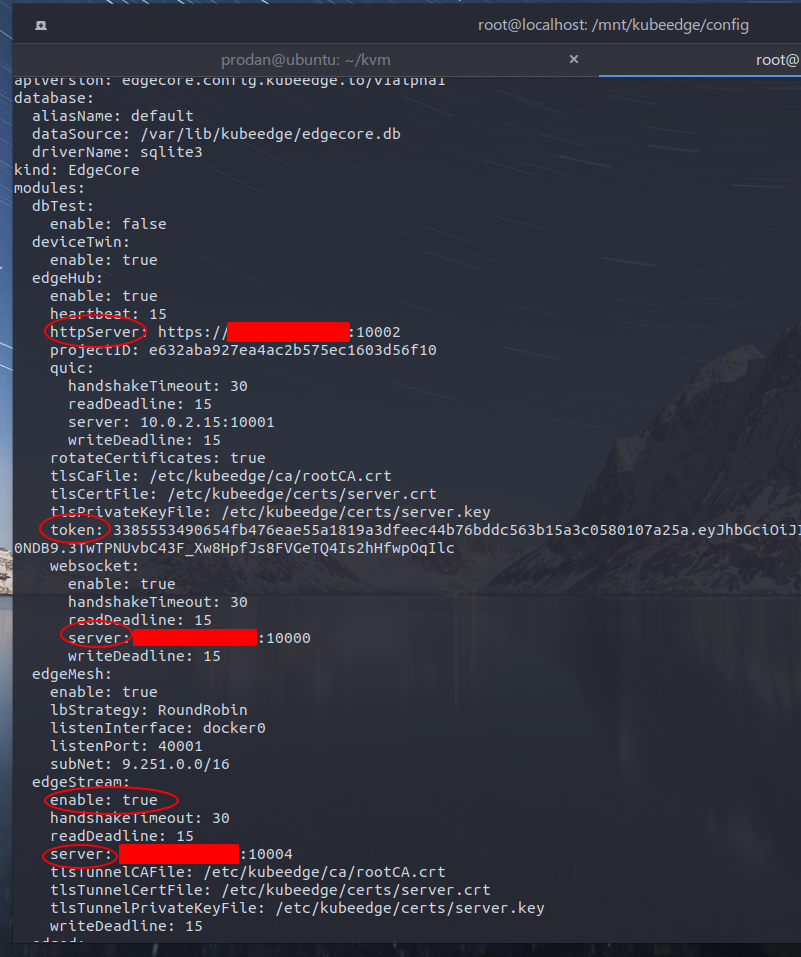
创建edgecore容器
docker run -it -d --restart=always \
--net host --name=edgecore \
--privileged=true --hostname=ubuntu-core-test01 \
-v /var/run/docker.sock:/var/run/docker.sock \
-v /mnt/kubeedge/:/etc/kubeedge/ \
-v /var/lib/snapd/edged:/var/lib/snapd/edged \
-v /var/snap/docker/:/var/snap/docker/ \
kubeedge/edgecore:v1.4.0
Step 5: 到云端验证
查看边缘节点是否加入
root@k8s-test99:~# kubectl get nodes -o wide
NAME STATUS ROLES AGE VERSION INTERNAL-IP EXTERNAL-IP OS-IMAGE KERNEL-VERSION CONTAINER-RUNTIME
edge-test001 Ready agent,edge 2d v1.18.6-kubeedge-v1.4.0 172.31.250.219 <none> CentOS Linux 8 (Core) 4.18.0-193.14.2.el8_2.x86_64 docker://19.3.13
edge-test002 NotReady agent,edge 47h v1.18.6-kubeedge-v1.4.0 172.20.61.119 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
edge-test003 NotReady agent,edge 47h v1.18.6-kubeedge-v1.4.0 172.18.46.55 <none> CentOS Linux 7 (Core) 3.10.0-693.2.2.el7.x86_64 docker://18.6.1
k8s-test99 Ready master 2d v1.19.4 172.31.250.218 <none> Ubuntu 20.04.1 LTS 5.4.0-47-generic docker://19.3.13
ubuntu-core-test01 Ready agent,edge 101s v1.18.6-kubeedge-v1.4.0 10.0.2.15 <none> Debian GNU/Linux 9 (stretch) 4.15.0-112-generic docker://19.3.11
root@k8s-test99:~#
调度pod验证
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 18h 172.17.0.2 edge-test001 <none> <none>
root@k8s-test99:~# kubectl scale deploy nginx --replicas=2
deployment.apps/nginx scaled
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 18h 172.17.0.2 edge-test001 <none> <none>
nginx-6bc4cff87d-sqr7m 0/1 Pending 0 2s <none> ubuntu-core-test01 <none> <none>
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 18h 172.17.0.2 edge-test001 <none> <none>
nginx-6bc4cff87d-sqr7m 0/1 ContainerCreating 0 6s 172.17.0.2 ubuntu-core-test01 <none> <none>
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 18h 172.17.0.2 edge-test001 <none> <none>
nginx-6bc4cff87d-sqr7m 1/1 Running 0 17s 172.17.0.2 ubuntu-core-test01 <none> <none>
测试kubectl logs功能
root@k8s-test99:~# kubectl get po -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-6bc4cff87d-c6ln7 1/1 Running 0 18h 172.17.0.2 edge-test001 <none> <none>
nginx-6bc4cff87d-sqr7m 1/1 Running 0 17s 172.17.0.2 ubuntu-core-test01 <none> <none>
root@k8s-test99:~#
root@k8s-test99:~# kubectl logs -f nginx-6bc4cff87d-sqr7m
/docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration
/docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/
/docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.sh
10-listen-on-ipv6-by-default.sh: Getting the checksum of /etc/nginx/conf.d/default.conf
10-listen-on-ipv6-by-default.sh: Enabled listen on IPv6 in /etc/nginx/conf.d/default.conf
/docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.sh
/docker-entrypoint.sh: Configuration complete; ready for start up
测试Metrics server功能
root@k8s-test99:~# kubectl top nodes
NAME CPU(cores) CPU% MEMORY(bytes) MEMORY%
edge-test001 34m 0% 2248Mi 29%
k8s-test99 248m 6% 2762Mi 35%
ubuntu-core-test01 31m 1% 20Mi 1%
edge-test002 <unknown> <unknown> <unknown> <unknown>
edge-test003 <unknown> <unknown> <unknown> <unknown>
root@k8s-test99:~#
总结
对于物联网终端设备来说,ubuntu core比linux发行版更适合,在安全方面也有优势。同时使用ubuntu core也会面临的一些问题或挑战。KubeEdge 与 Ubuntu Core探索与试用还在继续.....






