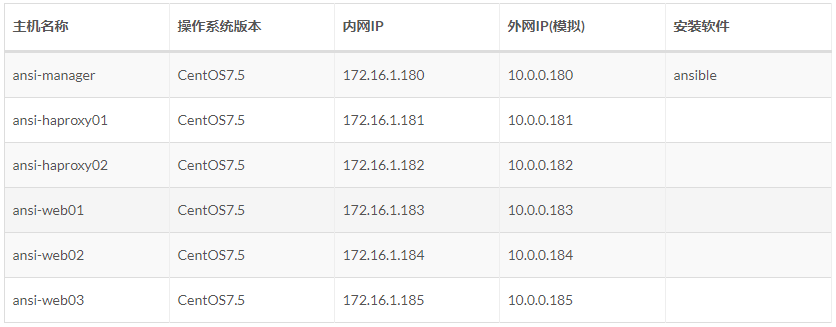
主机规划
添加用户账号
说明:
1、 运维人员使用的登录账号;
2、 所有的业务都放在 app/ 下「yun用户的家目录」,避免业务数据乱放;
3、 该用户也被 ansible 使用,因为几乎所有的生产环境都是禁止 root 远程登录的(因此该 yun 用户也进行了 sudo 提权)。
# 使用一个专门的用户,避免直接使用root用户# 添加用户、指定家目录并指定用户密码# sudo提权# 让其它普通用户可以进入该目录查看信息useradd -u 1050 -d app yun && echo '123456' | usr/bin/passwd --stdin yunecho "yun ALL=(ALL) NOPASSWD: ALL" >> etc/sudoerschmod 755 app/
Ansible 配置清单Inventory
之后文章都是如下主机配置清单
[yun@ansi-manager ansible_info]$ pwd/app/ansible_info[yun@ansi-manager ansible_info]$ cat hosts_key# 方式1、主机 + 端口 + 密钥[manageservers]172.16.1.180:22[proxyservers]172.16.1.18[1:2]:22# 方式2:别名 + 主机 + 端口 + 密码[webservers]web01 ansible_ssh_host=172.16.1.183 ansible_ssh_port=22web02 ansible_ssh_host=172.16.1.184 ansible_ssh_port=22web03 ansible_ssh_host=172.16.1.185 ansible_ssh_port=22
Ansible Vault 概述
当我们写的 playbook 中涉及敏感信息,如:数据库账号密码;MQ账号密码;主机账号密码。这时为了防止这些敏感信息泄露,就可以使用 vault 进行加密。
[yun@ansi-manager ~]$ ansible-vault -hUsage: ansible-vault [create|decrypt|edit|encrypt|encrypt_string|rekey|view] [options] [vaultfile.yml]Options:--ask-vault-pass ask for vault password-h, --help show this help message and exit--new-vault-id=NEW_VAULT_IDthe new vault identity to use for rekey--new-vault-password-file=NEW_VAULT_PASSWORD_FILEnew vault password file for rekey--vault-id=VAULT_IDS the vault identity to use--vault-password-file=VAULT_PASSWORD_FILESvault password file-v, --verbose verbose mode (-vvv for more, -vvvv to enableconnection debugging)--version show program's version number, config file location,configured module search path, module location,executable location and exitSee 'ansible-vault <command> --help' for more information on a specificcommand.
参数说明
create:创建一个加密文件,在创建时会首先要求输入 Vault 密码,之后才能进入文件中编辑。
decrypt:对 vault 加密的文件进行解密。
edit:对 vault 加密文件进行编辑。
encrypt:对提供的文件,进行 vault 加密。
encrypt_string:对提供的字符串进行 vault 加密。
rekey:对已 vault 加密的文件进行免密更改,需要提供之前的密码。
view:查看已加密的文件,需要提供密码。
Ansible Vault 交互式
创建加密文件
[yun@ansi-manager object06]$ pwd/app/ansible_info/object06[yun@ansi-manager object06]$ ansible-vault create test_vault.ymlNew Vault password: # 输入密码Confirm New Vault password: # 确认密码---# vault test- hosts: proxyserverstasks:- name: "touch file"file:path: tmp/with_itemstestfilestate: touch[yun@ansi-manager object06]$ cat test_vault.yml # 加密后查看$ANSIBLE_VAULT;1.1;AES256336632396365303535643937313631616234623862666131653262353537623434656532353966396138353833366637383066366662666236666338333237610a303263336234303866623834663361393436336464343533343961626430636139643333373433363732326532666132646265643465666262633334353036620a63313631336438353632353137316434643666373966363135316666343438663962363032643163333266633662376538383134333862373961313166656536353734363537306262613661383838646538343366373932303634663366623061383230323733616565666632316536303939373632626631626138306536373963386164646437373364396633323334343630373137366130363064366337393837396664356335363738663130333436656238666233396466393137333064343432623139613936613135363863383832333032306139626637323236306636383135313236636438646166643937613761396564373033623637636166
对已加密的文件进行解密
[yun@ansi-manager object06]$ ansible-vault decrypt test_vault.ymlVault password:Decryption successful[yun@ansi-manager object06]$[yun@ansi-manager object06]$ cat test_vault.yml # 解密后查看---# vault test- hosts: proxyserverstasks:- name: "touch file"file:path: tmp/with_itemstestfilestate: touch
对已存在文件进行加密
[yun@ansi-manager object06]$ ansible-vault encrypt test_vault.ymlNew Vault password:Confirm New Vault password:Encryption successful[yun@ansi-manager object06]$ cat test_vault.yml$ANSIBLE_VAULT;1.1;AES256373139646631646134346566663232653764653034336334386130323037333631363162356230663930343836396537343333336432363732343936323937370a363239356233333634303464633539616132643630373138333637386238666437626666626461656465613436316464343838643733386334333162616332320a35303332353864356666656264633462363034393864626466356131656635633939653166326631303635363533613338326561666663623238396464383363613738323464373061636639333238363161656665323366643530383030363835643464366332353731666638346238346437363237383932356230616366636631373866323465613934613037303162626561383038373135616261616137326337633566306633343338306264646139396230613665356264353134373766366462666262363236633762303139643230346231333335393931313330653239643030303139366661353732333961323764613332316535323334343939
对已加密的文件进行编辑
[yun@ansi-manager object06]$ ansible-vault edit test_vault.ymlVault password:---# vault test ==- hosts: proxyserverstasks:- name: "touch file"file:path: /tmp/with_itemstestfilestate: touch
对已加密文件更改密码
[yun@ansi-manager object06]$ ansible-vault rekey test_vault.ymlVault password:New Vault password:Confirm New Vault password:Rekey successful
对已加密文件进行查看
[yun@ansi-manager object06]$ ansible-vault view test_vault.ymlVault password:---# vault test ==- hosts: proxyserverstasks:- name: "touch file"file:path: /tmp/with_itemstestfilestate: touch
对提供的字符串进行加密
[yun@ansi-manager object06]$ ansible-vault encrypt_string "111 222 333"New Vault password:Confirm New Vault password:!vault |$ANSIBLE_VAULT;1.1;AES256613433323862373634376239396333346262316135393535663133363065623735386339373635666537336166356466666431663037623835643964366137340a336439313066356265666636383430366136613932326131343339616439366461643961306136636562373938373665663566313530613034326337303932610a3032326434646332393835633938363065653538356664313631323038353635Encryption successful
Ansible Vault 非交互式
创建密码文件
安全使用,记得使用 400 或 600 权限。
[yun@ansi-manager object06]$ echo "111111" > vault_pwd[yun@ansi-manager object06]$ echo "123456" > vault_pwd2[yun@ansi-manager object06]$ ll vault_pwd* # 权限 400-r-------- 1 yun yun 7 Aug 30 10:35 vault_pwd-r-------- 1 yun yun 7 Aug 30 10:39 vault_pwd2
创建加密文件
[yun@ansi-manager object06]$ ansible-vault create test_vault02.yml --vault-password-file=vault_pwd---# vault test 2[yun@ansi-manager object06]$ cat test_vault02.yml$ANSIBLE_VAULT;1.1;AES256343563646138646561366163653833613866353163323638616563346432303661363133333763666638666536306162366263333037323231386365316238390a383139623435363738663832623533346665393930363833653330623330396438326162336237646131323039663965346166333263666131313833383761620a38353436356439383630623866613565613762303638653165393162336230613036333161613235393539633233663136653566366266353232386230383434
对已加密的文件进行解密
[yun@ansi-manager object06]$ ansible-vault decrypt test_vault02.yml --vault-password-file=vault_pwdDecryption successful[yun@ansi-manager object06]$ cat test_vault02.yml---# vault test 2
对已存在文件进行加密
[yun@ansi-manager object06]$ ansible-vault encrypt test_vault02.yml --vault-password-file=vault_pwdEncryption successful[yun@ansi-manager object06]$[yun@ansi-manager object06]$ cat test_vault02.yml$ANSIBLE_VAULT;1.1;AES256656530353932303663653636373431376363376636383464633035326231393531373661623965363533393766313339393665386463613831323366623962650a643365653833636663653938613966393230373966353332366632393164313434613465623937313635373138656235343965336539313638363937626635390a30396265336635313837313962323735663765623038656566336462643831613837383338323065346634323632396339323635323766386236623038616233
对已加密的文件进行编辑
[yun@ansi-manager object06]$ ansible-vault edit test_vault02.yml --vault-password-file=vault_pwd---# vault test 2 ##
对已加密文件更改密码
[yun@ansi-manager object06]$ ansible-vault rekey test_vault02.yml --vault-password-file=vault_pwd --new-vault-password-file=vault_pwd2Rekey successful
对已加密文件进行查看
[yun@ansi-manager object06]$ ansible-vault view test_vault02.yml --vault-password-file=vault_pwd2---# vault test 2 ##
对提供的字符串进行加密
[yun@ansi-manager object06]$ ansible-vault encrypt_string "test info" --vault-password-file=vault_pwd2!vault |$ANSIBLE_VAULT;1.1;AES256303137666132633639633166636236643538626230323233313565636266366462396366663437666633363733303334373831303732326435396566313066630a373562633530333832613335393835343961613138626564663534333138356430306339663830326565613433316162343738316232336636396135306436640a3135313738356636333836653961393434646138613130343863653931376133Encryption successful
Playbook 使用 vault 文件
# 其中 test_vault.yml 的 vault 密码为 vault_pwd 中的信息[yun@ansi-manager object06]$ ansible-vault view test_vault.yml --vault-password-file=vault_pwd---# vault test ==- hosts: proxyserverstasks:- name: "touch file"file:path: /tmp/with_itemstestfilestate: touch[yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key --syntax-check test_vault.yml --vault-password-file=vault_pwd # 语法检测[yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key -C test_vault.yml --vault-password-file=vault_pwd # 预执行,测试执行[yun@ansi-manager object06]$ ansible-playbook -b -i ../hosts_key test_vault.yml --vault-password-file=vault_pwd # 执行
推荐阅读
Ansible Playbook 变量与 register 详解
———END———
如果觉得不错就关注下呗 (-^O^-) !







