
前篇文章Traefik 2.0 Now GA! Traefik V2真正来了!作者主要介绍traefik v2.0相较于v1.0版本的一些新功能特性,此篇文章主要介绍在K8S集群中,traefik v1.0升级至v2.0的流程介绍和在线上的一些功能使用。
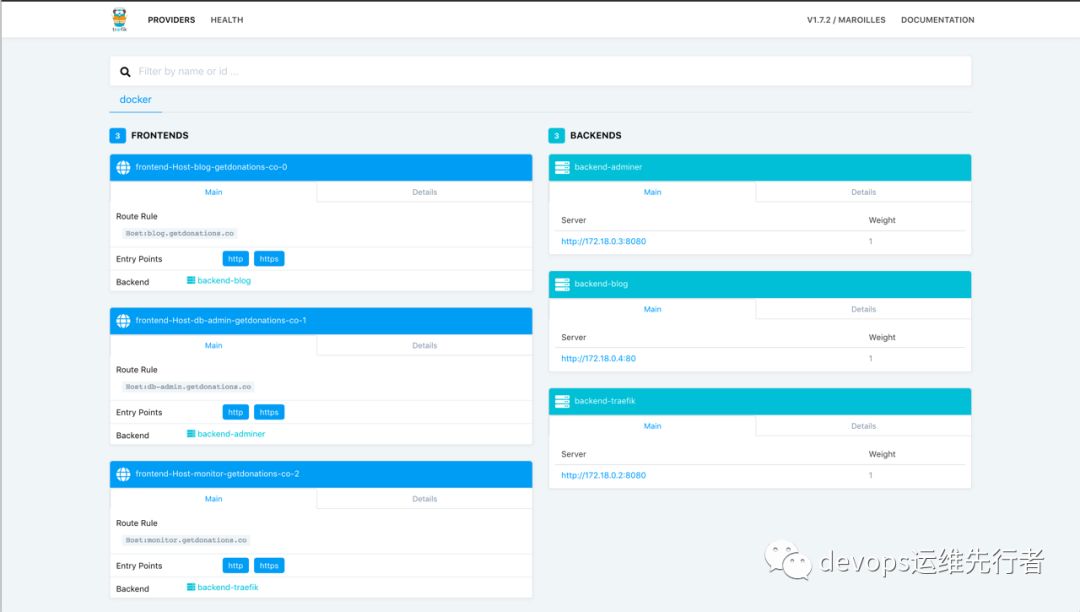
V1配置清单
#ingress-rbac.yamlapiVersion: v1kind: ServiceAccountmetadata:name: ingressnamespace: kube-system---kind: ClusterRoleBindingapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: ingresssubjects:- kind: ServiceAccountname: ingressnamespace: kube-systemroleRef:kind: ClusterRolename: cluster-adminapiGroup: rbac.authorization.k8s.io
#traefik-ingress.yamlapiVersion: extensions/v1beta1kind: Deploymentmetadata:name: traefik-ingress-lbnamespace: kube-systemlabels:k8s-app: traefik-ingress-lbspec:replicas: 4template:metadata:labels:k8s-app: traefik-ingress-lbname: traefik-ingress-lbspec:terminationGracePeriodSeconds: 60hostNetwork: truerestartPolicy: AlwaysserviceAccountName: ingressvolumes:- name: sslhostPath:path: etc/kubernetes/cert- name: configconfigMap:name: traefik-confcontainers:- image: traefik:v1.7.17-alpinename: traefik-ingress-lbvolumeMounts:- mountPath: "/ssl"name: "ssl"- mountPath: "/config"name: "config"resources:limits:cpu: 200mmemory: 1Girequests:cpu: 100mmemory: 20Miports:- containerPort: 80- containerPort: 443- containerPort: 8580args:- --web.address=:8580- --web- --kubernetes- --configfile=/config/traefik.toml---kind: ServiceapiVersion: v1metadata:name: traefiknamespace: kube-systemspec:type: NodePortports:- protocol: TCPport: 80nodePort: 30201name: http- protocol: TCPport: 443nodePort: 30202name: httpsselector:k8s-app: traefik-ingress-lb
#traefik-map.yamlkind: ConfigMapapiVersion: v1metadata:name: traefik-confnamespace: kube-systemdata:traefik.toml: |MaxIdleConnsPerHost = 5000graceTimeOut = 60insecureSkipVerify = truedefaultEntryPoints = ["http"][entryPoints][entryPoints.http]address = ":80"compress = true
#traefik_ui.yamlapiVersion: v1kind: Servicemetadata:name: traefik-web-uinamespace: kube-systemspec:type: NodePortselector:k8s-app: traefik-ingress-lbports:- name: webport: 801targetPort: 8580---apiVersion: extensions/v1beta1kind: Ingressmetadata:name: traefik-web-uinamespace: kube-systemannotations:kubernetes.io/ingress.class: traefikingress.kubernetes.io/auth-type: basicingress.kubernetes.io/auth-secret: basic-authspec:rules:- host: www.traefik-v1.comhttp:paths:- path:backend:serviceName: traefik-web-uiservicePort: web
V2配置清单
#CRD-rbac.yamlapiVersion: apiextensions.k8s.io/v1beta1kind: CustomResourceDefinitionmetadata:name: ingressroutes.traefik.containo.usspec:group: traefik.containo.usversion: v1alpha1names:kind: IngressRouteplural: ingressroutessingular: ingressroutescope: Namespaced---apiVersion: apiextensions.k8s.io/v1beta1kind: CustomResourceDefinitionmetadata:name: ingressroutetcps.traefik.containo.usspec:group: traefik.containo.usversion: v1alpha1names:kind: IngressRouteTCPplural: ingressroutetcpssingular: ingressroutetcpscope: Namespaced---apiVersion: apiextensions.k8s.io/v1beta1kind: CustomResourceDefinitionmetadata:name: middlewares.traefik.containo.usspec:group: traefik.containo.usversion: v1alpha1names:kind: Middlewareplural: middlewaressingular: middlewarescope: Namespaced---apiVersion: apiextensions.k8s.io/v1beta1kind: CustomResourceDefinitionmetadata:name: tlsoptions.traefik.containo.usspec:group: traefik.containo.usversion: v1alpha1names:kind: TLSOptionplural: tlsoptionssingular: tlsoptionscope: Namespaced---kind: ClusterRoleapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: traefik-ingress-controllerrules:- apiGroups:- ""resources:- services- endpoints- secretsverbs:- get- list- watch- apiGroups:- extensionsresources:- ingressesverbs:- get- list- watch- apiGroups:- extensionsresources:- ingresses/statusverbs:- update- apiGroups:- traefik.containo.usresources:- middlewaresverbs:- get- list- watch- apiGroups:- traefik.containo.usresources:- ingressroutesverbs:- get- list- watch- apiGroups:- traefik.containo.usresources:- ingressroutetcpsverbs:- get- list- watch- apiGroups:- traefik.containo.usresources:- tlsoptionsverbs:- get- list- watch---kind: ClusterRoleBindingapiVersion: rbac.authorization.k8s.io/v1beta1metadata:name: traefik-ingress-controllerroleRef:apiGroup: rbac.authorization.k8s.iokind: ClusterRolename: traefik-ingress-controllersubjects:- kind: ServiceAccountname: traefik-ingress-controllernamespace: default---apiVersion: v1kind: ServiceAccountmetadata:namespace: defaultname: traefik-ingress-controller
#traefik-deployment.yamlkind: DeploymentapiVersion: extensions/v1beta1metadata:namespace: defaultname: traefiklabels:app: traefikspec:replicas: 4selector:matchLabels:app: traefiktemplate:metadata:labels:app: traefikspec:serviceAccountName: traefik-ingress-controllerterminationGracePeriodSeconds: 60hostNetwork: truerestartPolicy: Alwayscontainers:- name: traefikimage: traefik:v2.0args:- --api- --api.insecure- --entrypoints.http.Address=:80- --entrypoints.https.Address=:443- --providers.kubernetescrd- --ping- --accesslog=true- --log.level=ERROR- --serversTransport.insecureSkipVerify- --serversTransport.maxIdleConnsPerHost=5000- --global.checkNewVersion- --global.sendAnonymousUsageports:- name: httpcontainerPort: 80- name: httpscontainerPort: 443- name: admincontainerPort: 8080resources:limits:cpu: 500mmemory: 1Girequests:cpu: 100mmemory: 20Mi---apiVersion: v1kind: Servicemetadata:name: traefikspec:type: NodePortports:- protocol: TCPname: httpport: 80- protocol: TCPname: httpsport: 443- protocol: TCPname: adminport: 8080selector:app: traefik
#traefik-middleware.yamlapiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: admin-authnamespace: defaultspec:basicAuth:secret: basic-auth---apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: redirectnamespace: defaultspec:redirectScheme:scheme: https---# Enable gzip compressionapiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: compressnamespace: defaultspec:compress: {}---apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: headernamespace: defaultspec:headers:customResponseHeaders:Access-Control-Allow-Headers: content-type,x-token,x-request-id,authorization,token---apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: ipwhitelistnamespace: defaultspec:ipWhiteList:sourceRange:- 127.0.0.1- 172.16.0.0/16- 10.42.0.0/16ipStrategy:depth: 2---apiVersion: traefik.containo.us/v1alpha1kind: Middlewaremetadata:name: allowallnamespace: defaultspec:ipWhiteList:sourceRange:- 0.0.0.0/0
# traefik-admin.yamlapiVersion: v1kind: Servicemetadata:name: traefik-adminnamespace: defaultspec:type: ClusterIPports:- protocol: TCPname: adminport: 8080selector:app: traefik---apiVersion: traefik.containo.us/v1alpha1kind: IngressRoutemetadata:name: traefik-adminnamespace: defaultspec:# entryPoints:# - traefikentryPoints: []routes:- match: Host(`www.traefik-v2.com`) && PathPrefix(`/`)kind: Rulepriority: 1middlewares:- name: admin-authnamespace: default- name: compressnamespace: default- name: headernamespace: defaultservices:- name: traefik-adminnamespace: defaultport: 8080
从V1跟V2的配置上不难发现,V2使用了K8S CRD,采用IngressRoute来解析代理后端服务。
k8s traefik采用hostNetwork网络模式,所以阿里云SLB只要指向后端work node的80端口就可以访问目标域名,如traefik admin界面www.traefik-v2.com,
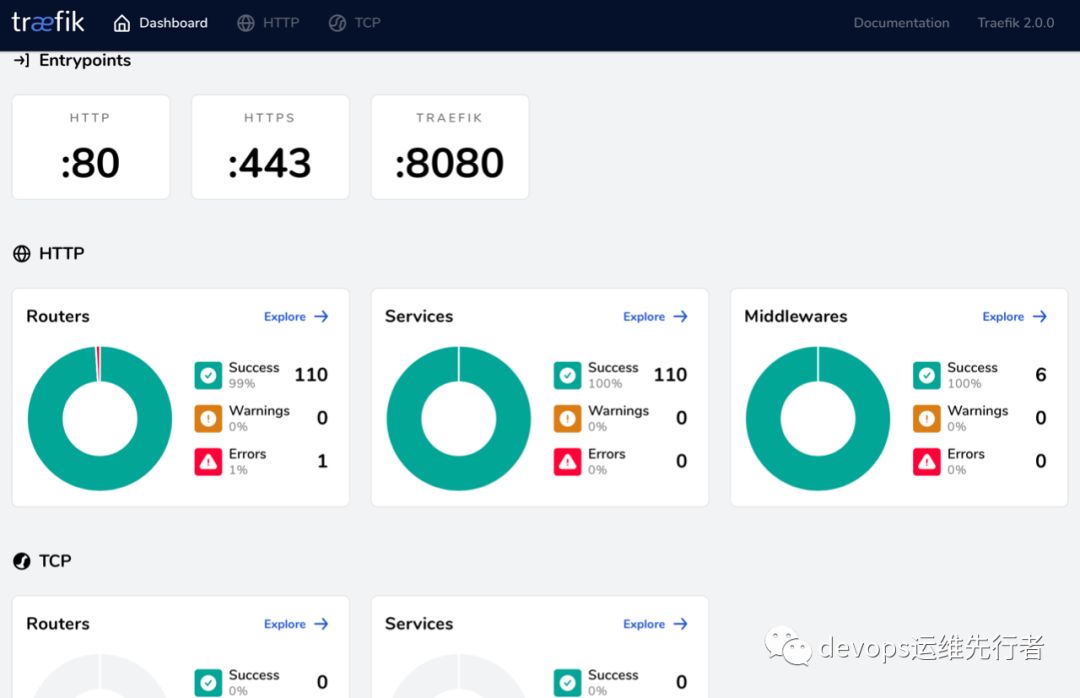
traefik线上使用
假设我们有一个Java 微服务需要上线,K8S配置文件为:
apiVersion: apps/v1kind: Deploymentmetadata:name: server-namenamespace: ENVlabels:jenkinsname: jenkins-namespec:replicas: 1selector:matchLabels:app: server-nametemplate:metadata:labels:app: server-namespec:containers:- name: server-nameimage: 172.16.10.13/test-server/server-name:<BUILD_TAG>imagePullPolicy: AlwayssecurityContext:allowPrivilegeEscalation: falsereadinessProbe:tcpSocket:port: 80initialDelaySeconds: 5periodSeconds: 5livenessProbe:tcpSocket:port: 80initialDelaySeconds: 600periodSeconds: 20ports:- name: webprotocol: TCPcontainerPort: 80resources:requests:#cpu: "100m"memory: "128Mi"limits:#cpu: "300m"memory: "MAXMEM"volumeMounts:- name: zonemountPath: /etc/localtimereadOnly: true- name: app-logsmountPath: /var/log/nginx- name: filebeatimage: 172.16.10.13/library/filebeat:v6.5.4args: ["-c", "/etc/filebeat.yml","-e",]securityContext:runAsUser: 0resources:limits:memory: 200Mirequests:cpu: 50mmemory: 100Mienv:- name: servernamevalue: "server-name"volumeMounts:- name: app-logsmountPath: /var/log/nginx- name: filebeatconfigmountPath: /etc/filebeat.ymlreadOnly: truesubPath: filebeat.yml- name: zonemountPath: /etc/localtimereadOnly: truevolumes:- name: zonehostPath:path: /etc/localtime- name: filebeatconfigconfigMap:defaultMode: 0600name: filebeat-template- name: app-logsemptyDir: {}---apiVersion: v1kind: Servicemetadata:name: server-name-svcnamespace: ENVspec:template:metadata:labels:name: server-name-svcnamespace: ENVspec:selector:app: server-nameports:- name: webport: 80targetPort: 80
按traefik v1的使用习惯,我们将使用ingress来代理:
apiVersion: extensions/v1beta1kind: Ingressmetadata:name: server-name-ingnamespace: ENVannotations:kubernetes.io/ingress.class: traefikingress.kubernetes.io/custom-response-headers: Access-Control-Allow-Headers:content-type,x-token,x-request-id,authorization,tokenspec:rules:- host: ENV-k8s-server-name.comhttp:paths:- path:backend:serviceName: server-name-svcservicePort: 80- host: ENV-server-name.comhttp:paths:- path:backend:serviceName: server-name-svcservicePort: 80- host: domainhttp:paths:- path:backend:serviceName: server-name-svcservicePort: 80
Traefik v2将使用k8s CRD,ingressroute来代理:
apiVersion: traefik.containo.us/v1alpha1kind: IngressRoutemetadata:name: server-namenamespace: ENVspec:entryPoints:- httproutes:- match: Host(`ENV-k8s-server-name.com`,`ENV-server-name.k8s.com`,`domain`) && PathPrefix(`/`)kind: Rulepriority: 10middlewares:- name: compressnamespace: default- name: headernamespace: defaultservices:- name: server-name-svcnamespace: ENVport: 80
注解:
entryPoints:后端使用的端口服务;
match:匹配规则;
priority:权重;
middlewares:中间件;
middlewares中间件可以查看traefik-middleware.yaml,配合match和middlewares字段,我们可以对域名路径做许多访问规则,类似于Nginx。
好了,今天的文章先讲一部分内容,后面继续更新ing···

文章转载自devops运维先行者,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






