htpasswd是openshift默认的一种简单的用户密码管理工具,本文将介绍在openshift上常用htpasswd命令参数;openshift引用的htpasswd文件路径为:/etc/origin/master/htpasswd。
参数介绍
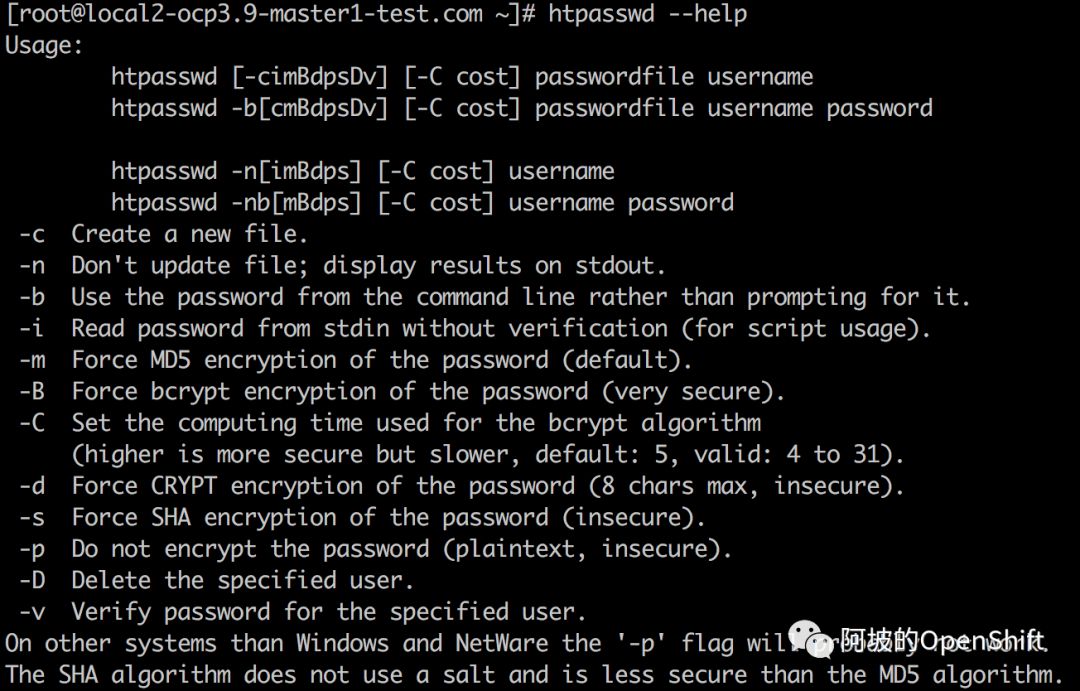
-c:创建htpasswd文件
当部署完openshift后,默认是没有/etc/origin/master/htpasswd文件的,当需要向该文件添加用户名和密码时,需先创建该文件,否则报:htpasswd: cannot modify file etc/origin/master/htpasswd; use '-c' to create it;通过-c参数即可创建,该命令通常结合-b参数使用;需要注意的,当有了该文件后,并且文件内有内容,再次添加用户时不能再使用-c参数,否则会将原文件给删除然后创建新文件。-n:类似dry run测试,不对文件进行更新,将运行结果输出至窗口
# htpasswd -nb user-test2 123456
user-test2:$apr1$8cPMzSyO$UIMM5PYPFIzdwnbeKWP1x/
-b:从命令行中读取密码
-i:测试了一下,不大明白该参数具体如何使用
-m:对密码使用的加密算法,默认是md5
-B:bcrypt加密方式
-C:设置bcrypt加密算法的长度
-d: CRYPT加密算法
-s:sha加密算法
-p:明文,不加密,如果使用该参数创建用户,则会提示如下信息,并且openshift无法登陆
# htpasswd -bp etc/origin/master/htpasswd user-test3 123456
Warning: storing passwords as plain text might just not work on this platform.
Adding password for user user-test3
-D:删除用户
常用命令
创建用户(第一次创建,从命令行显式传入密码)
# htpasswd -cb etc/origin/master/htpasswd user-test1 123456
Adding password for user user-test1
# cat etc/origin/master/htpasswd
user-test1:$apr1$Mq4mRqKC$pIuIZqUeGwr/SJYLd3IlZ0
创建用户(交互式输入密码,比较安全,不会通过history发现密码)
# htpasswd etc/origin/master/htpasswd user-test2
New password:
Re-type new password:
Adding password for user user-test2
更新密码:使用的是创建用户命令,当检测到有相同的用户名时,就会更新密码
# htpasswd -b etc/origin/master/htpasswd user-test1 111111
Updating password for user user-test1
# htpasswd etc/origin/master/htpasswd user-test2
New password:
Re-type new password:
Updating password for user user-test2
删除用户
# htpasswd -D etc/origin/master/htpasswd user-test2
Deleting password for user user-test2
修改用户名:htpasswd命令不支持修改用户名,我直接编辑htpasswd密码文件,测试了一下可以登录,修改完用户名后,要记得相应的修改新用户名对应的openshift权限。
用户权限分配
在创建好用户的情况下登录openshift,没有任何项目属于该项目,并且默认是允许用户创建项目的
不让普通用户组创建项目
# oc adm policy remove-cluster-role-from-group self-provisioner system:authenticated:oauth
cluster role "self-provisioner" removed: "system:authenticated:oauth"
恢复让普通用户组创建项目
# oc adm policy add-cluster-role-to-group self-provisioner system:authenticated:oauth
cluster role "self-provisioner" added: "system:authenticated:oauth"
指定某个用户可以或者不可以创建项目
# oc adm policy add-cluster-role-to-user self-provisioner xxx
# oc adm policy remove-cluster-role-from-user self-provisioner xxx
openshift的用户角色分为项目内级别和集群级别,刚刚创建的user-test1不属于任何项目,且没有角色。
当该用户创建一个项目时,就会分配给该项目admin的角色
# oc login -u user-test1 -p 111111
You don't have any projects. You can try to create a new project, by running
oc new-project <projectname>
# oc new-project p1
Now using project "p1" on server "https://cluster.test.com:8443".
You can add applications to this project with the 'new-app' command. For example, try:
oc new-app centos/ruby-22-centos7~https://github.com/openshift/ruby-ex.git
to build a new example application in Ruby.
# oc get project
NAME DISPLAY NAME STATUS
p1 Active
# oc project
Using project "p1" on server "https://cluster.test.com:8443".
# oc get rolebinding
NAME ROLE USERS GROUPS SERVICE ACCOUNTS SUBJECTS
admin admin user-test1
system:deployers /system:deployer deployer
system:image-builders system:image-builder builder
system:image-pullers /system:image-puller system:serviceaccounts:p1
user-test2也是没有任何项目,这时候在p1项目里,通过user-test1分配一个view角色给user-test2
# oc project
Using project "p1" on server "https://cluster.test.com:8443".
# oc adm policy add-role-to-user view user-test2
role "view" added: "user-test2"
切换至user-test2用户,发现能看到user-test1的项目p1,但是因为只有该项目的view权限,所以不能创建和查看一些特殊权限的东西。
# oc login -u user-test2 -p 1111
Login successful.
You have one project on this server: "p1"
Using project "p1".
# oc get project
NAME DISPLAY NAME STATUS
p1 Active
为user-test2用户分配集群管理员权限,就可以看到所有的项目了。
# oc adm policy add-cluster-role-to-user cluster-admin user-test2
cluster role "cluster-admin" added: "user-test2"
[root@local2-ocp3.9-master1-test.com ~]# oc login -u user-test2 -p 1111
Login successful.
You have access to the following projects and can switch between them with 'oc project <projectname>':
bdk-dev
default
jenkins
kube-public
kube-system
logging
management-infra
openshift
openshift-infra
openshift-node
openshift-web-console
* p1
user1-1
user2-2
Using project "p1".






