在web渗透测试中,信息侦察与收集相当重要,每个经验丰富的黑客都有自己独特的信息收集妙招,信息搜集是渗透的第一步,也是至关重要的一步,信息的多少决定攻击的范围有多少。Recon-ng是用Python编写的功能齐全的Web侦察框架。具有独立模块,数据库交互功能和内置的便捷功能,最主要的recon-ng是一个被动信息搜集框架,主要利用第三方API进行信息收集。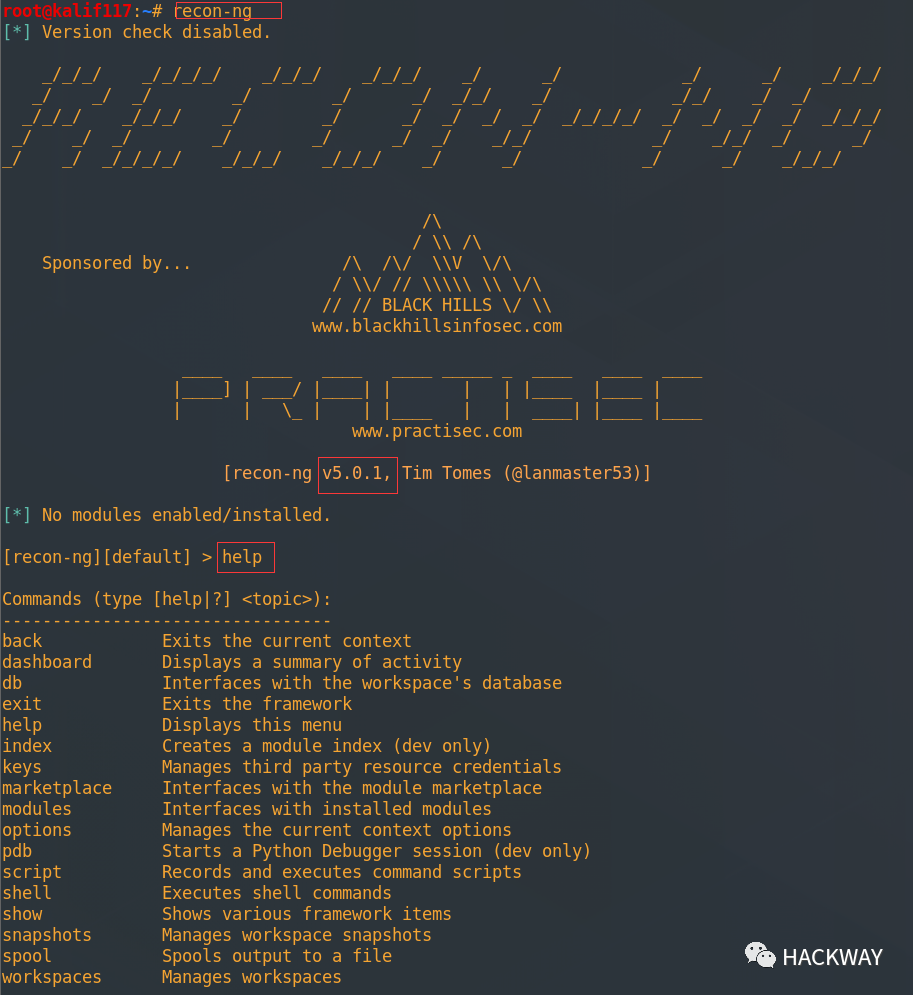 信息收集分为三步:
信息收集分为三步:侦察Reconnaissance
、发现Discovery
与汇报reporting
。这也对应了该工具的三个模块,现在就记录一下Recon-ng 这款较新的信息侦察收集工具的使用。具体详细可参阅官方文档[1],针对自定义编写recon-ng模块可前往Github项目[2]查看
模块安装
Recon-ng 5 最大的改变是没有模块,需要下载。且命令变化很大。刚启动的时候,会提示“No modules enabled/installed.(未启用/未安装任何模块。)
官方给出的答案是,此框架本身默认不包含任何模块。必须从 marketplace 模块市场中安装模块。
可以用命令来安装所有的模块:
[recon-ng][default] > marketplace install all
下面再介绍下载特定模块,以hackertarget为例,
1.输入 marketplace refresh 更新模块列表
[recon-ng][default] marketplace refresh[*] Marketplace index refreshed.[recon-ng][default]
2.输入 marketplace search hackertarget 搜索模块索引
[recon-ng][sina] marketplace search hackertarget[*] Searching module index for 'hackertarget'...|Path| Version | Status | Updated | D | K || recon/domains-hosts/hackertarget | 1.0| installed | 2019-06-24 |D = Has dependencies. See info for details.K = Requires keys. See info for details.[recon-ng][sina]
3.输入 marketplace install recon/domains-hosts/hackertarget ,安装hackertarget模块
[recon-ng][default] marketplace install recon/domains-hosts/hackertarget[*] Module installed: recon/domains-hosts/hackertarget[*] Reloading modules...[recon-ng][default]
快速上手
以hackertarget模块为例子
第一步 加载模块
[recon-ng][default] modules load recon/domains-hosts/hackertarget[recon-ng][default][hackertarget]
第二步 查看参数信息
[recon-ng][default][hackertarget] infoName: HackerTarget LookupAuthor: Michael Henriksen (@michenriksen)Version: 1.0Description:Uses the HackerTarget.com API to find host names. Updates the 'hosts' table with the results.Options:Name Current Value Required Description------ ------------- -------- -----------SOURCE default yes source of input (see 'show info' for details)Source Options:default SELECT DISTINCT domain FROM domains WHERE domain IS NOT NULL<string string representing a single input<path path to a file containing a list of inputsquery <sql database query returning one column of inputs[recon-ng][sina][hackertarget]
第三步 设置目标参数并运行
[recon-ng][default][hackertarget] options set SOURCE rapid7.comSOURCE = rapid7.com[recon-ng][default][hackertarget] run----------RAPID7.COM----------[*] [host] rapid7.com (13.249.47.238)[*] [host] scanner1.labs.rapid7.com (71.6.233.2)[*] [host] scanner2.labs.rapid7.com (71.6.233.129)[*] [host] scanner3.labs.rapid7.com (31.24.231.211)[*] [host] scanner4.labs.rapid7.com (31.24.231.223)[*] [host] sonar.labs.rapid7.com (34.236.82.205)...
第四步 查看结果列表
[recon-ng][default] show hosts| rowid | host | ip_address | region | country | latitude | longitude | module |+---------------------------------------------------------------------------------------------------------------------------------+| 1 | rapid7.com | 99.84.219.205 | | | | | hackertarget || 2 | hostedconsole-pso-01.rapid7.com |..........................................................| 137 | community.rapid7.com | 34.210.186.136 | | | | | hackertarget |[*] 137 rows returned[recon-ng][default]
模块枚举
Recon-ng约有80个recon模块,2个发现模块,2个exp利用模块,7个报告模块和2个导入模块
cache_snoop – DNS缓存录制interesting_files – 敏感文件探测command_injector – 远程命令注入shell接口xpath_bruter – Xpath注入爆破csv_file – 高级csv文件导入list – List文件导入point_usage – Jigsaw – 统计信息提取用法purchase_contact – Jigsaw – 简单的联系查询search_contacts – Jigsaw联系枚举jigsaw_auth – Jigsaw认证联系枚举linkedin_auth – LinkedIn认证联系枚举github_miner – Github资源挖掘whois_miner – Whois数据挖掘bing_linkedin – Bing Linkedin信息采集email_validator – SalesMaple邮箱验证mailtester – MailTester邮箱验证mangle – 联系分离unmangle –联系反分离hibp_breach –Breach搜索hibp_paste – Paste搜索pwnedlist – PwnedList验证migrate_contacts – 域名数据迁移联系facebook_directory – Facebook目录爬行fullcontact – FullContact联系枚举adobe – Adobe Hash破解bozocrack – PyBozoCrack Hash 查询hashes_org – Hashes.org Hash查询leakdb – leakdb Hash查询metacrawler – 元数据提取pgp_search – PGP Key Owner查询salesmaple – SalesMaple联系获取whois_pocs – Whois POC获取account_creds – PwnedList – 账户认证信息获取api_usage – PwnedList – API使用信息domain_creds – PwnedList – Pwned域名认证获取domain_ispwned – PwnedList – Pwned域名统计获取leak_lookup – PwnedList – 泄露信息查询leaks_dump – PwnedList –泄露信息获取brute_suffix – DNS公共后缀爆破baidu_site – Baidu主机名枚举bing_domain_api – Bing API主机名枚举bing_domain_web – Bing主机名枚举brute_hosts – DNS主机名爆破builtwith – BuiltWith枚举google_site_api – Google CSE主机名枚举google_site_web – Google主机名枚举netcraft – Netcraft主机名枚举shodan_hostname – Shodan主机名枚举ssl_san – SSL SAN查询vpnhunter – VPNHunter查询yahoo_domain – Yahoo主机名枚举zone_transfer – DNS域文件收集ghdb – Google Hacking数据库punkspider – PunkSPIDER漏洞探测xssed – XSSed域名查询xssposed – XSSposed域名查询migrate_hosts – 域名数据迁移hostbing_ip – Bing API旁站查询freegeoip –FreeGeoIP ip定位查询ip_neighbor – My-IP-Neighbors.com查询ipinfodb – IPInfoDB GeoIP查询resolve – 主机名解析器reverse_resolve – 反解析ssltools – SSLTools.com主机名查询geocode – 地理位置编码reverse_geocode – 反地理位置编码flickr – Flickr地理位置查询instagram – Instagram地理位置查询picasa – Picasa地理位置查询shodan – Shodan地理位置查询twitter – Twitter地理位置查询whois_orgs – Whois公司信息收集reverse_resolve – 反解析shodan_net – Shodan网络枚举census_2012 – Internet Census 2012 查询sonar_cio – Project Sonar查询migrate_ports – 主机端口数据迁移dev_diver – Dev Diver Repository检查linkedin – Linkedin联系获取linkedin_crawl – Linkedin信息抓取namechk – NameChk.com用户名验证profiler – OSINT HUMINT信息收集twitter – Twitter操作github_repos – Github代码枚举gists_search – Github Gist搜索github_dorks – Github Dork分析csv – CSV文件生成html – HTML报告生成json – JSON报告生成list – List生成pushpin – PushPin报告生成xlsx – XLSX文件创建xml – XML报告生成
常用模块
Domin-Hosts
# 通过domin获取更多的子域名recon/domains-hosts/hackertargetrecon/domains-hosts/brute_hostsrecon/domains-hosts/findsubdomainsrecon/domains-hosts/google_site_web
Hosts-Hosts
# 通过子域名获取真实的ip地址及地理位置recon/hosts-hosts/resolverecon/hosts-hosts/ipinfodb
Hosts-Ports
# 通过ip地址被动获取开启端口信息,需要shodan的api keyrecon/hosts-ports/shodan_ip
Report
# 导出模块,支持多种格式reporting/htmlreporting/listreporting/xlsxreporting/csv
Import
# 导入模块import/nmap # 需要oX导出格式import/listimport/masscanimport/csv_file
参考资料
官方文档: https://bitbucket.org/LaNMaSteR53/recon-ng
[2]模块编写: https://github.com/scumsec/Recon-ng-modules