oracle linux7.9+oracle rac 19.18由于安全审计的要求,需要启用主机防火墙策略
基本步骤参考如下:
1.内部网段RAC之间访问:
1.1物理IP段的网段(根据ip a|grep inet)
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.0.0/24" port protocol="tcp" port="1-65535" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.0.0/24" port protocol="udp" port="1-65535" accept'
1.2私有IP的网段,其中涉及到tcp和udp的区别(ip a|grep inet)
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="1.1.1.0/24" port protocol="tcp" port="1-65535" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="1.1.1.0/24" port protocol="udp" port="1-65535" accept'
1.3服务器分配给自己的网段(ip a|grep inet)
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="169.254.0.0/16" port protocol="tcp" port="1-65535" accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="169.254.0.0/16" port protocol="udp" port="1-65535" accept'
2.外部网段访问系统和数据库端口:(根据last和listener.log)
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.26.19.0/24" port protocol=tcp port=1521 accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.0.0/24" port protocol=tcp port=1521 accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.75.87.0/24" port protocol=tcp port=1521 accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.26.19.0/24" port protocol=tcp port=22 accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.2.40.0/24" port protocol=tcp port=22 accept'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="10.2.30.0/24" port protocol=tcp port=22 accept'
3.堡垒机映射:(根据last确定ip)
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="50.50.16.0/24" port protocol=tcp port=22 accept'
4.最后保存:firewall-cmd --reload
其它:
firewall-cmd --permanent --add-rich-rule='rule priority="-100" family=ipv4 source address="192.168.207.0/24" accept'
firewall-cmd --permanent --add-rich-rule='rule priority="-100" family=ipv4 source address="192.168.207.0/24" reject'
firewall-cmd --permanent --remove-rich-rule='rule family=ipv4 source address="192.168.205.0/24" reject'
firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="192.168.254.135/24" port protocol="tcp" port="22" reject'
firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address="192.168.205.0/24" reject'
常用命令:
停止防火墙
systemctl stop firewalld
禁止防火墙自启动
systemctl disable firewalld
开启防火墙启动
systemctl enable firewalld
查看服务是否开机启动:
systemctl is-enabled firewalld
查看防火墙状态
systemctl status firewalld
启动防火墙
systemctl start firewalld
重启用服务强策略
firewall-cmd --reload
查看防火墙策略
firewall-cmd --list-all
查看已开放端口:
firewall-cmd --zone=public --list-ports
查看firewalld服务当前所使用的区域,设置区域为public
firewall-cmd --get-default-zone
firewall-cmd --set-default-zone=public
firewall-cmd --zone=public --list-rich-rules
查看是否阻断:
firewall-cmd --query-panic
放开所有网络:
firewall-cmd --panic-off
查看开放白名单IP参考用到的脚本:
两个节点都需要核查
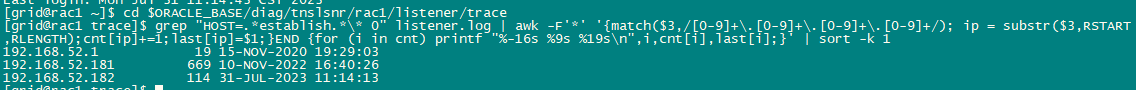
[grid@rac1 ~]$ cd $ORACLE_BASE/diag/tnslsnr/rac1/listener/trace
[grid@rac1 trace]$ pwd
/oracle/app/grid/diag/tnslsnr/rac1/listener/trace
[grid@rac1 trace]$ grep "HOST=.*establish.*\* 0" listener.log | awk -F'*' '{match($3,/[0-9]+\.[0-9]+\.[0-9]+\.[0-9]+/); ip = substr($3,RSTART,RLENGTH);cnt[ip]+=1;last[ip]=$1;}END {for (i in cnt) printf "%-16s %9s %19s\n",i,cnt[i],last[i];}' | sort -k 1
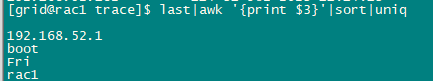
[grid@rac1 trace]$ last|awk '{print $3}'|sort|uniq
netstat -tunlp|grep LISTEN
ip a|grep net
ifconfig -a
测试方式:(通过mcasttest.pl工具测试多播是否正常)
Grid Infrastructure Startup During Patching, Install or Upgrade May Fail Due to Multicasting Requirement (Doc ID 1212703.1)
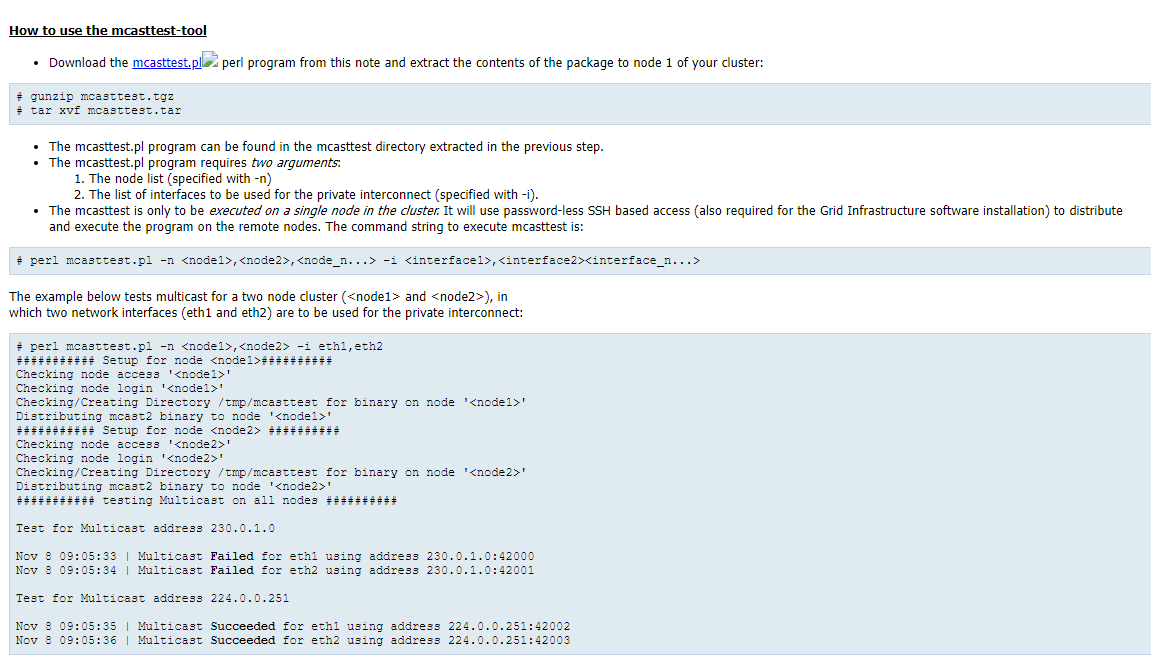
mcasttest下载https://www.modb.pro/doc/113830
[root@rac2 ~]# systemctl status firewalld
鈼[0m firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2023-07-31 10:42:25 CST; 2min 37s ago
Docs: man:firewalld(1)
Main PID: 1313 (firewalld)
CGroup: /system.slice/firewalld.service
鈹斺攢1313 /usr/bin/python2 -Es /usr/sbin/firewalld --nofork --nopid
Jul 31 10:42:25 rac2 systemd[1]: Starting firewalld - dynamic firewall daemon...
Jul 31 10:42:25 rac2 systemd[1]: Started firewalld - dynamic firewall daemon.
[root@rac2 ~]# su - grid
Last login: Mon Jul 31 10:44:39 CST 2023
[grid@rac2 ~]$ cd mcasttest/
[grid@rac2 mcasttest]$ perl mcasttest.pl -n rac1,rac2 -i ens33,ens34
########### Setup for node rac1 ##########
Checking node access 'rac1'
Checking node login 'rac1'
Checking/Creating Directory /tmp/mcasttest for binary on node 'rac1'
Distributing mcast2 binary to node 'rac1'
########### Setup for node rac2 ##########
Checking node access 'rac2'
Checking node login 'rac2'
Checking/Creating Directory /tmp/mcasttest for binary on node 'rac2'
Distributing mcast2 binary to node 'rac2'
########### testing Multicast on all nodes ##########
Test for Multicast address 230.0.1.0
Jul 31 10:45:24 | Multicast Succeeded for ens33 using address 230.0.1.0:42000
Jul 31 10:45:25 | Multicast Succeeded for ens34 using address 230.0.1.0:42001
Test for Multicast address 224.0.0.251
Jul 31 10:45:26 | Multicast Succeeded for ens33 using address 224.0.0.251:42002
Jul 31 10:45:27 | Multicast Succeeded for ens34 using address 224.0.0.251:42003
[grid@rac2 mcasttest]$ crsctl stat res -t
--------------------------------------------------------------------------------
Name Target State Server State details
--------------------------------------------------------------------------------
Local Resources
--------------------------------------------------------------------------------
ora.DGLISTENER.lsnr
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.LISTENER.lsnr
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.chad
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.net1.network
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
ora.ons
ONLINE ONLINE rac1 STABLE
ONLINE ONLINE rac2 STABLE
--------------------------------------------------------------------------------
Cluster Resources
--------------------------------------------------------------------------------
ora.ASMNET1LSNR_ASM.lsnr(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
3 ONLINE OFFLINE STABLE
ora.DATA.dg(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
3 OFFLINE OFFLINE STABLE
ora.LISTENER_SCAN1.lsnr
1 ONLINE ONLINE rac1 STABLE
ora.LISTENER_SCAN2.lsnr
1 ONLINE ONLINE rac2 STABLE
ora.asm(ora.asmgroup)
1 ONLINE ONLINE rac1 Started,STABLE
2 ONLINE ONLINE rac2 Started,STABLE
3 OFFLINE OFFLINE STABLE
ora.asmnet1.asmnetwork(ora.asmgroup)
1 ONLINE ONLINE rac1 STABLE
2 ONLINE ONLINE rac2 STABLE
3 OFFLINE OFFLINE STABLE
ora.cvu
1 ONLINE ONLINE rac2 STABLE
ora.dgorcl.db
1 OFFLINE OFFLINE STABLE
2 OFFLINE OFFLINE STABLE
ora.dw.db
1 ONLINE ONLINE rac1 Open,HOME=/oracle/ap
p/oracle/product/19c
/dbhome_1,STABLE
2 ONLINE ONLINE rac2 Open,HOME=/oracle/ap
p/oracle/product/19c
/dbhome_1,STABLE
ora.integrated_office.db
1 OFFLINE OFFLINE STABLE
ora.orcl.db
1 OFFLINE OFFLINE STABLE
2 OFFLINE OFFLINE STABLE
ora.qosmserver
1 ONLINE ONLINE rac2 STABLE
ora.rac1.vip
1 ONLINE ONLINE rac1 STABLE
ora.rac2.vip
1 ONLINE ONLINE rac2 STABLE
ora.scan1.vip
1 ONLINE ONLINE rac1 STABLE
ora.scan2.vip
1 ONLINE ONLINE rac2 STABLE
--------------------------------------------------------------------------------
[grid@rac2 mcasttest]$ ip a|grep net
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
inet 192.168.52.182/24 brd 192.168.52.255 scope global noprefixroute ens33
inet 192.168.52.184/24 brd 192.168.52.255 scope global secondary ens33:2
inet 192.168.52.186/24 brd 192.168.52.255 scope global secondary ens33:3
inet6 fe80::59f1:28bc:2c87:431f/64 scope link noprefixroute
inet 192.168.161.182/24 brd 192.168.161.255 scope global noprefixroute ens34
inet 169.254.14.134/19 brd 169.254.31.255 scope global ens34:1
inet6 fe80::4c5:492:8ee1:5688/64 scope link noprefixroute
[grid@rac2 mcasttest]$ cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
#public
192.168.52.181 rac1
192.168.52.182 rac2
#vip
192.168.52.183 rac1-vip
192.168.52.184 rac2-vip
#priv
192.168.161.181 rac1-priv
192.168.161.182 rac2-priv
#scan
192.168.52.185 rac-scan
192.168.52.186 rac-scan
「喜欢这篇文章,您的关注和赞赏是给作者最好的鼓励」
关注作者
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文章的来源(墨天轮),文章链接,文章作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






