
学习 探索 分享数据库前沿知识和技术 共建数据库技术交流圈
4 审计追踪
4.1 传统审计
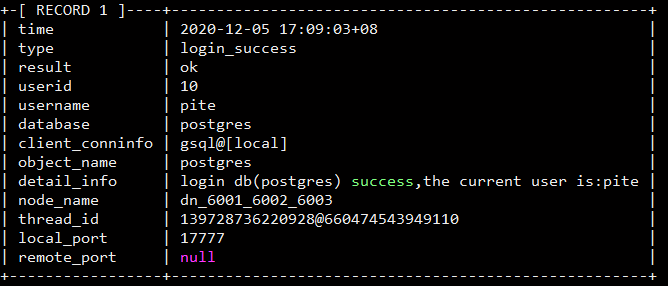
typedef struct AuditData {AuditMsgHdr header; // 记录文件头,存储记录的标识、大小等信息AuditType type; // 审计类型AuditResult result; // 执行结果char varstr[1]; // 二进制格式存储的具体审计信息} AuditData;
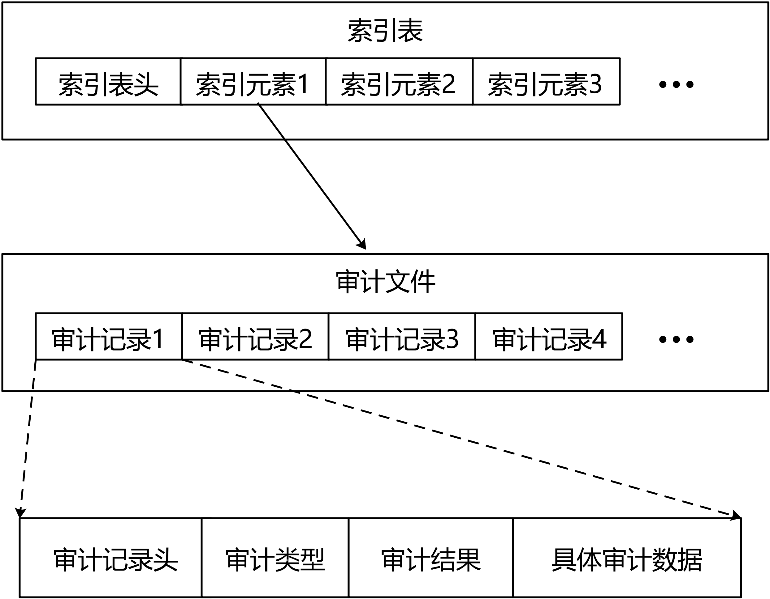
typedef struct AuditMsgHdr {char signature[2]; // 审计记录标识,目前固定为AUDIT前两个字符’A’和’U’uint16 version; // 版本信息,目前固定为0uint16 fields; // 审计记录字段数,目前为13uint16 flags; // 记录有效性标识,如果被删除则标记为DEADpg_time_t time; // 审计记录创建时间uint32 size; // 审计信息占字节长度} AuditMsgHdr;
typedef struct AuditIndexTable {uint32 maxnum; // 审计目录下审计文件个数的最大值uint32 begidx; // 审计文件开始编号uint32 curidx; // 当前使用的审计文件编号uint32 count; // 当前审计文件的总数pg_time_t last_audit_time; // 最后一次写入审计记录的时间AuditIndexItem data[1]; // 审计文件指针} AuditIndexTable;
typedef struct AuditIndexItem {pg_time_t ctime; // 审计文件创建时间uint32 filenum; // 审计文件编号uint32 filesize; // 审计文件占空间大小} AuditIndexItem;
void audit_report(AuditType type, AuditResult result, const char* object_name, const char* detail_info);
SELECT * FROM pg_query_audit (timestamptz startime,timestamptz endtime, audit_log);
SELECT * FROM pg_delete_audit (timestamptz startime,timestamptz endtime);
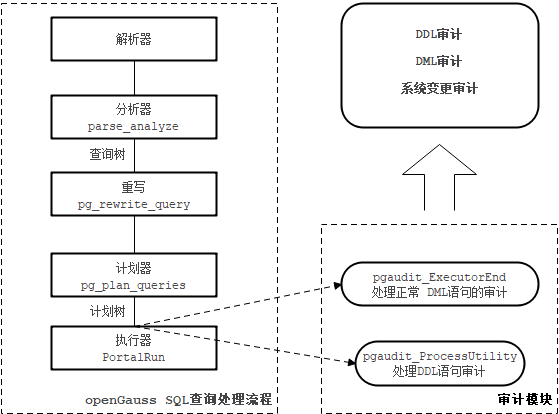
void pgaudit_agent_init(void) {…// DDL、DML语句审计hook赋值, 赋值结束后标识审计模块已在此线程加载prev_ExecutorEnd = ExecutorEnd_hook;ExecutorEnd_hook = pgaudit_ExecutorEnd;prev_ProcessUtility = ProcessUtility_hook;ProcessUtility_hook = (ProcessUtility_hook_type)pgaudit_ProcessUtility;u_sess->exec_cxt.g_pgaudit_agent_attached = true;}
pgaudit_system_recovery_okpgaudit_system_start_okpgaudit_system_stop_okpgaudit_user_loginpgaudit_user_logoutpgaudit_system_switchover_okpgaudit_user_no_privilegespgaudit_lock_or_unlock_user
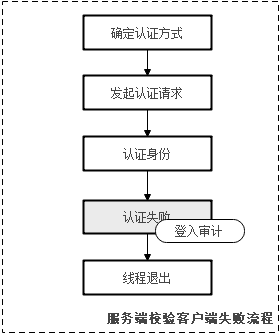
/* 拼装登入口失败时候的详细信息,包括数据库名称和用户名 */rc = snprintf_s(details,PGAUDIT_MAXLENGTH,PGAUDIT_MAXLENGTH - 1,"login db(%s)failed,authentication for user(%s)failed",port->database_name,port->user_name);securec_check_ss(rc, "\0", "\0");// 调用登入审计函数,记录审计日志pgaudit_user_login(FALSE, port->database_name, details);// 退出当前线程ereport(FATAL, (errcode(errcode_return), errmsg(errstr, port->user_name)))
void pgaudit_user_login(bool login_ok, const char* object_name, const char* detaisinfo){AuditType audit_type;AuditResult audit_result;Assert(detaisinfo);// 审计类型和审计结果拼装if (login_ok) {audit_type = AUDIT_LOGIN_SUCCESS;audit_result = AUDIT_OK;} else {audit_type = AUDIT_LOGIN_FAILED;audit_result = AUDIT_FAILED;}// 直接调用审计日志记录接口audit_report(audit_type, audit_result, object_name, detaisinfo);}
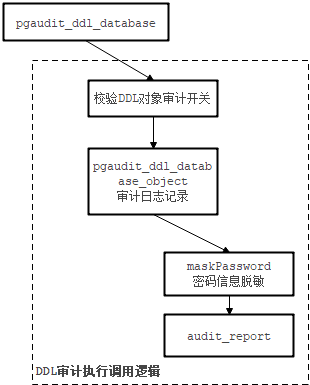
typedef enum {DDL_DATABASE = 0,DDL_SCHEMA,DDL_USER,DDL_TABLE,DDL_INDEX,DDL_VIEW,DDL_TRIGGER,DDL_FUNCTION,DDL_TABLESPACE,DDL_RESOURCEPOOL,DDL_WORKLOAD,DDL_SERVERFORHADOOP,DDL_DATASOURCE,DDL_NODEGROUP,DDL_ROWLEVELSECURITY,DDL_TYPE,DDL_TEXTSEARCH,DDL_DIRECTORY,DDL_SYNONYM} DDLType;
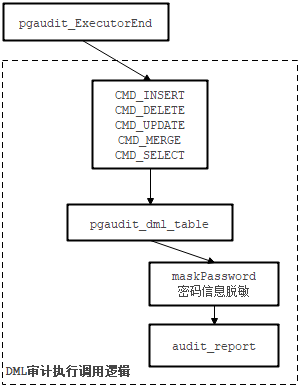
case CMD_SELECT:object_name = pgaudit_get_relation_name(queryDesc->estate->es_range_table);pgaudit_dml_table_select(object_name, queryDesc->sourceText);
以上内容从传统审计和统一审计两方面对高斯数据库的审计追踪技术进行解读,下篇将从数据动态脱敏方面对高斯数据库的数据保护技术进行解读,敬请期待~
文章转载自Gauss松鼠会,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。








