前言
为OKE集群开启OIDC身份验证后,集群使用 OIDC 身份验证器插件通过指定的 OIDC 身份提供商对用户进行身份验证。身份验证流程如下:
用户登录到 OIDC 身份提供商以获取 id_token。
用户向集群发出 kubectl 命令,将 id_token 作为参数传递。
Kubernetes API 使用来自 OIDC 身份提供商的信息验证 id_token。
Kubernetes API 服务执行 Kubernetes RBAC 授权。
如果用户获得授权,Kubernetes API 服务将执行请求的作,并且 kubectl 会向用户返回响应。
实施步骤
一、获取GCP clientId和clientSecret
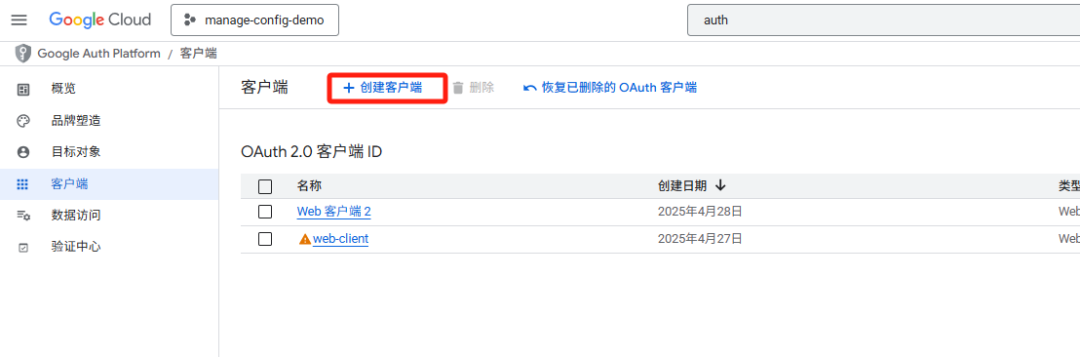
登录GCP Console创建一个客户端,如下图所示:
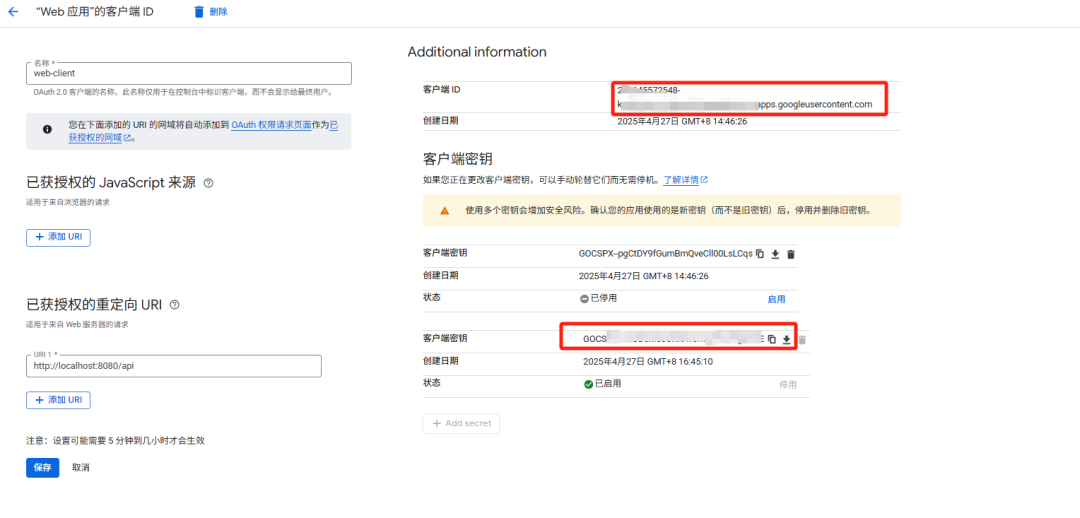
如图所示获取其clientId和clientSecret
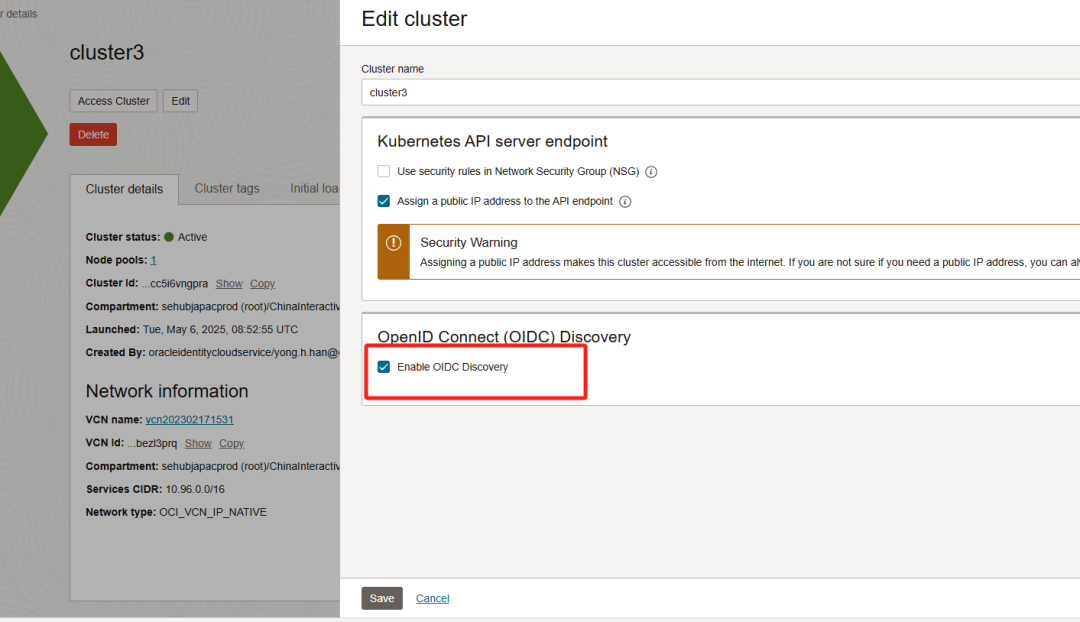
二、更新集群并指定单个外部 OpenID Connect (OIDC)身份提供商
在OKE控制台上打开OIDC选项
创建一个json文件oidc.json,更新下面的clientId
{
"options": {
"openIdConnectTokenAuthenticationConfig": {
"isOpenIdConnectAuthEnabled": true,
"issuerUrl": "https://accounts.google.com",
"clientId": "<client-id>"
}
}
} |
执行下面的命令,更新集群。cluster-id可以在OKE控制台查看
oci ce cluster update --cluster-id ocid1.cluster.oc1.i************* --from-json file://oidc.json
|
三、创建RBAC
yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: view-nodes-only
rules:
- apiGroups: [""]
resources: ["nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: oidc-admin-binding
subjects:
- kind: User
name: oidc-token-generator@manage-config-demo.iam.gserviceaccount.com
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io |
四、配置用户credentials
我们需要获取下面这些参数
kubectl config set-credentials oidc-admin-user \
--auth-provider=oidc \
--auth-provider-arg=idp-issuer-url=https://accounts.google.com \
--auth-provider-arg=client-id=267645572548-ka0l9r3uo1vhi8us \
--auth-provider-arg=client-secret=1db158______c5 \
--auth-provider-arg=id-token=eyJr______4knw \
--auth-provider-arg=extra-scopes=groups |
gcloud登录,需要首先在gcp控制台导出密钥文件
gcloud auth activate-service-account --key-file=/home/opc/key/gcp.json |
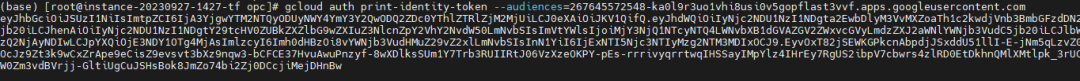
获取id-token命令,audiences为clintId:
gcloud auth print-identity-token --audiences=267645572548-ka0l9r3uo1vhi8usi0v5gopflast3vvf.apps.googleusercontent.com |
最终配置为
kubectl config set-credentials oidc-admin-user \
--auth-provider=oidc \
--auth-provider-arg=idp-issuer-url=https://accounts.google.com \
--auth-provider-arg=client-id=267645572*******.apps.googleusercontent.com \
--auth-provider-arg=client-secret=GOCSBzjz***** \
--auth-provider-arg=id-token=eyJhbGciOiJSUzI1NiIsImtpZCI6IjA3YjgwYTM2NTQyODUyNWY4YmY3Y2QwODQ2ZDc0YThlZTRlZjM2MjUiLCJ0eXAiOiJKV1QifQ*******ZUBkZXZlbG9wZXIuZ3NlcnZpY2VhY2NvdW50LmNvbSIsImVtYWlsIjoiMjY3NjQ1NTJpYXQiOjE3NDY2MDUyMjAsImlzcyI6Imh0dHBzOi8vYWNjb3VudHMuZ29vZ2xlLmNvbSIsInN1YiI6IjExNTI5Njc3NTIyMzg2NTM3MDIxOCJ9.y7wD3xxNZXyYmcZ1Kbbjxktsj6xcEqrfN-UZhFXXtcCQakoR1lzcNzXcbCzBmTTOg3uw216nD93Vhsx-I43ZyBMv1OfjIpsjVKXJ3L8U0LU8CFLo4QbAuQ3LOEdDa7qCdPEIVSy4veeKq-wjxHjBzRHmzDDNFCxLBgr4A8g25KjmtB0hDBQQlZSaEmVic9ZcYa0h5xIoMJYJF9HOgi7i35c7UnB-KhF3JT1MjHJPVKhE5cExzaca6W6HoXo4Q6F-yrZvawMo6v_BZJ4ulMhXyF3XnPBhjsjI16B4sxSJ4VlIe81YkSA22fAlfCZ1WwucEbT85Dx_3MBmeNwrOxhKeA \
--auth-provider-arg=extra-scopes=groups |
创建oidc-admin-user
(base) [root@instance-20230927-1427-tf tmp]# kubectl config set-credentials oidc-admin-user \
--auth-provider=oidc \
--auth-provider-arg=idp-issuer-url=https://accounts.google.com \
--auth-provider-arg=client-id=267645572*******.apps.googleusercontent.com \
--auth-provider-arg=client-secret=GOCSBzjz***** \
--auth-provider-arg=id-token=eyJhbGciOiJSUzI1NiIsImtpZCI6IjA3YjgwYTM2NTQyODUyNWY4YmY3Y2QwODQ2ZDc0YThlZTRlZjM2MjUiLCJ0eXAiOiJKV1QifQ*******ZUBkZXZlbG9wZXIuZ3NlcnZpY2VhY2NvdW50LmNvbSIsImVtYWlsIjoiMjY3NjQ1NTJpYXQiOjE3NDY2MDUyMjAsImlzcyI6Imh0dHBzOi8vYWNjb3VudHMuZ29vZ2xlLmNvbSIsInN1YiI6IjExNTI5Njc3NTIyMzg2NTM3MDIxOCJ9.y7wD3xxNZXyYmcZ1Kbbjxktsj6xcEqrfN-UZhFXXtcCQakoR1lzcNzXcbCzBmTTOg3uw216nD93Vhsx-I43ZyBMv1OfjIpsjVKXJ3L8U0LU8CFLo4QbAuQ3LOEdDa7qCdPEIVSy4veeKq-wjxHjBzRHmzDDNFCxLBgr4A8g25KjmtB0hDBQQlZSaEmVic9ZcYa0h5xIoMJYJF9HOgi7i35c7UnB-KhF3JT1MjHJPVKhE5cExzaca6W6HoXo4Q6F-yrZvawMo6v_BZJ4ulMhXyF3XnPBhjsjI16B4sxSJ4VlIe81YkSA22fAlfCZ1WwucEbT85Dx_3MBmeNwrOxhKeA \
--auth-provider-arg=extra-scopes=groups
User "oidc-admin-user" set. |
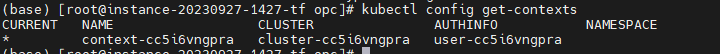
获取cluster名称并记录
创建context OIDC-auth,使用上面获取的cluster名称
(base) [root@instance-20230927-1427-tf tmp]# kubectl config set-context OIDC-auth --cluster=cluster-cc5i6vngpra --user=oidc-admin-user
Context "OIDC-auth" created. |
切换至 OIDC-auth 上下文后,执行kubectl命令并成功返回结果,表明配置已生效。此时,集群访问采用的是 GCP 的身份验证流程,而非 OCI 的认证机制。
(base) [root@instance-20230927-1427-tf tmp]# kubectl config use-context OIDC-auth
Switched to context "OIDC-auth".
(base) [root@instance-20230927-1427-tf tmp]#
(base) [root@instance-20230927-1427-tf tmp]# k get nodes
NAME STATUS ROLES AGE VERSION
10.0.0.35 Ready node 23h v1.32.1
|
编辑:赵靖宇