


为了安全起见,一般生产上都会使用https证书。那么证书我们很多时候使用的阿里云或者腾讯云的免费CA证书或者收费证书。如果觉得免费证书比较麻烦也可以使用openssl命令生成证书,这里采用openssl自谦证书来演示。
1、生成自签证书
#创建一个临时证书目录
mkdir /root/traefik-ssl/ && cd "$_"
#创建证书,时间为10年
openssl req -newkey rsa:2048 -nodes -keyout tls.key -x509 -days 3650 -out tls.crt
#这里直接一路回车
#当前目录下会产生一个crt文件和一个key文件
[root@k8s-master traefik-ssl]# ll
total 12
-rw-r--r-- 1 root root 1220 Mar 5 13:29 tls.crt
-rw-r--r-- 1 root root 1704 Mar 5 13:29 tls.key
2、创建secret对象,将证书储存到secret中
kubectl create secret generic traefik-cert --from-file=tls.crt --from-file=tls.key -n kube-system
#如果有现成的证书文件,修改个名称就可以使用了,步骤不变
3、检查生成的secret
[root@k8s-master traefik-ssl]# kubectl get secret -n kube-system|grep traefik
traefik-cert Opaque 2 44h
traefik-ingress-controller-token-kf4qs kubernetes.io/service-account-token 3 114m
[root@k8s-master traefik-ssl]# kubectl describe secret -n kube-system traefik-cert
Name: traefik-cert
Namespace: kube-system
Labels: <none>
Annotations: <none>
Type: Opaque
Data
====
ca-cert.pem: 1103 bytes
rsa_private_key.pem: 1679 bytes
给traefik创建一个配置文件 (这里配置文件的后缀为toml)
vim /root/traefik-ssl/traefik.toml
defaultEntryPoints = ['http', 'https']
[entryPoints] #指定一个入口
[entryPoints.http] #配置一个http的入口
address = ":80" #http的端口 (根据svc自行修改)
[entryPoints.http.redirect] #强制将http协议跳转到https,相当于nginx 301跳转。不添加也可以
entryPoint = 'https'
#因为强制跳转到https上,接下来需要配置https
[entryPoints.https]
address = ":443"
[entryPoints.https.tls] #https需要指定2个证书
[[entryPoints.https.tls.certificates]]
CertFile = "/ssl/tls.crt" #证书文件目录
KeyFile = "/ssl/tls.key"
创建一个configmap,使用configmap的方式挂载到traefik中
kubectl create configmap traefik-conf --from-file=/root/traefik-ssl/traefik.toml -n kube-system
[root@k8s-master traefik-ssl]# kubectl get cm -n kube-system | grep traefik
traefik-conf 1 44h
修改traefik的Deployment文件,将configmap和secret挂载到traefik容器中,并且修改traefik启动参数、添加443端口
kind: Deployment
apiVersion: extensions/v1beta1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
replicas: 1
selector:
matchLabels:
k8s-app: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
terminationGracePeriodSeconds: 60
volumes: #这里的Mount相当于声明
- name: ssl
secret: #引用之前创建的secret
secretName: traefik-cert
- name: config
configMap: #这里引用configmap资源对象
name: traefik-conf
#tolerations:
#- operator: "Exists"
#nodeSelector:
# kubernetes.io/hostname: k8s-04
containers:
- image: traefik:v1.7.20
name: traefik-ingress-lb
volumeMounts: #将声明的文件挂载到Pod中的路径
- mountPath: "/ssl"
name: ssl #将secret资源对象挂载到/ssl目录中
- mountPath: "/config" #将configmap声明的对象挂载到/config下
name: config
ports:
- name: http
containerPort: 80
hostPort: 80
- name: https #为pod添加一个443端口
containerPort: 443
hostPort: 443
- name: admin
containerPort: 8080
args:
- --configfile=/config/traefik.toml #设置启动参数,指定配置文件
- --api
- --kubernetes
- --logLevel=INFO
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
type: NodePort
#创建更新
[root@k8s-master ingress]# kubectl apply -f traefik-deployment.yaml
deployment.extensions/traefik-ingress-controller configured
service/traefik-ingress-service unchanged
注意:特别查看yaml中的注释部分
检查traefik-ingress-controller运行状态
[root@k8s-master ingress]# kubectl get pod -n kube-system | grep traefik
traefik-ingress-controller-dd45949b-4xzcn 1/1 Running 0 37s
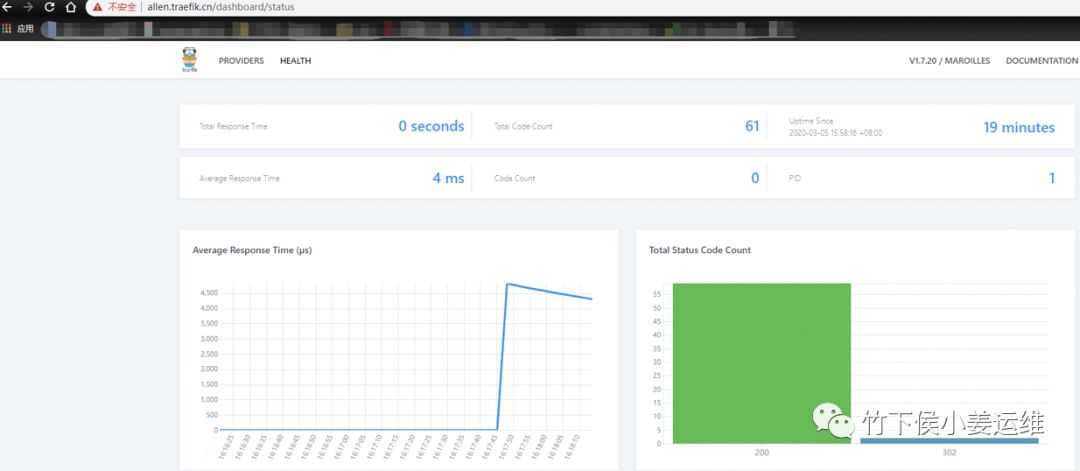
打开配置的域名,ctrl+f5强制刷新。或者Google浏览器打开无痕浏览就可以看到traefik已经强制将80跳转到443。因为证书没有CA机构签署,所以会提示我们不安全
点高级--继续前往。然后就能看到UI界面了。
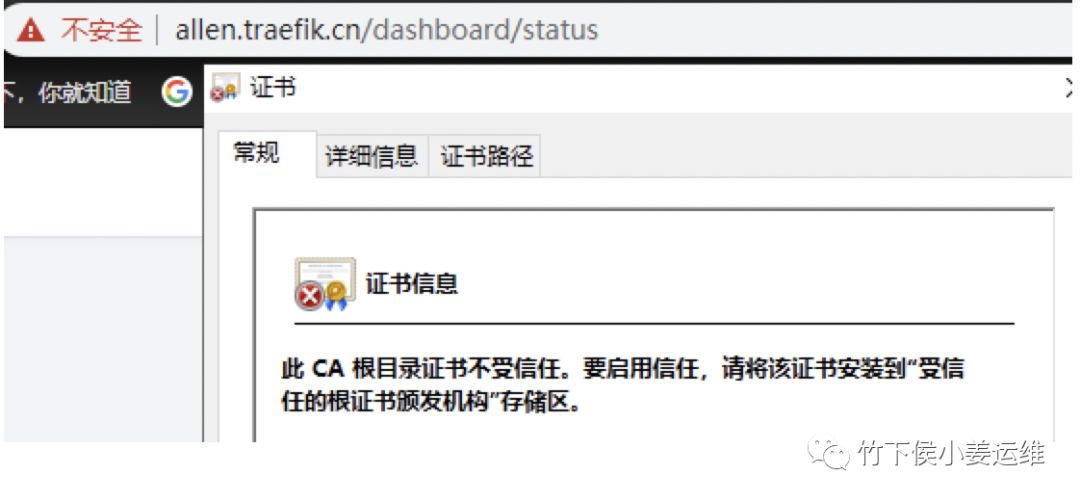
但是查看证书会发现是无效的。这是因为咱们是openssl自建x509证书。没设置浏览器信任。如果是云厂商的CA机构颁发的证书创建的就没这个问题了
四、配置traefik path
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: tomcat1
spec:
replicas: 1
template:
metadata:
labels:
app: tomcat1
spec:
containers:
- name: tomcat1
image: allen_jol/tomcat:v1.1
ports:
- containerPort: 8080
protocol: TCP
---
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: tomcat2
spec:
replicas: 1
template:
metadata:
labels:
app: tomcat2
spec:
containers:
- name: tomcat2
image: allen_jol/tomcat:v1.2
ports:
- containerPort: 8080
protocol: TCP
---
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: tomcat3
spec:
replicas: 1
template:
metadata:
labels:
app: tomcat3
spec:
containers:
- name: tomcat3
image: allen_jol/tomcat:v1.3
ports:
- containerPort: 8080
protocol: TCP
---
apiVersion: v1
kind: Service
metadata:
labels:
app: tomcat1
name: tomcat1
spec:
type: ClusterIP
ports:
- name: http
port: 8080
selector:
app: tomcat1
---
apiVersion: v1
kind: Service
metadata:
labels:
app: tomcat2
name: tomcat2
spec:
type: ClusterIP
ports:
- name: http
port: 8080
selector:
app: tomcat2
---
apiVersion: v1
kind: Service
metadata:
labels:
app: tomcat3
name: tomcat3
spec:
type: ClusterIP
ports:
- name: http
port: 8080
selector:
app: tomcat3
#这里主要创建了3个deployment,镜像为tomcat,并且设置了svc
[root@k8s-master ingress]# kubectl apply -f tomcat-deployment.yaml
deployment.extensions/tomcat1 created
deployment.extensions/tomcat2 created
deployment.extensions/tomcat3 created
service/tomcat1 created
service/tomcat2 created
service/tomcat3 created
查看pod和svc状态
[root@k8s-master ingress]# kubectl get po,svc
NAME READY STATUS RESTARTS AGE
pod/tomcat1-6548659b58-bc8kq 1/1 Running 0 5s
pod/tomcat2-7d68d5cfc9-s8gk6 1/1 Running 0 5s
pod/tomcat3-554b58468-tz9kh 1/1 Running 0 5s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.68.0.1 <none> 443/TCP 6d19h
service/tomcat1 ClusterIP 10.68.103.114 <none> 8080/TCP 5s
service/tomcat2 ClusterIP 10.68.170.78 <none> 8080/TCP 5s
service/tomcat3 ClusterIP 10.68.34.152 <none> 8080/TCP 5s
测试访问:
[root@k8s-master ingress]# curl 10.68.103.114:8080
ayunw.com_1
[root@k8s-master ingress]# curl 10.68.170.78:8080
ayunw.com_2
[root@k8s-master ingress]# curl 10.68.34.152:8080
ayunw.com_3
创建ingress对象:
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: tomcat-web #ingress名称
annotations: #指定ingress类型为traefik
kubernetes.io/ingress.class: traefik
traefik.frontend.rule.type: PathPrefixStrip ##跳转后端时忽略 path (如果不添加这个参数,我们请求到v1的时候,在v1访问依旧会带有v1)
spec:
rules: #配置规则
- host: tomcat.allenjol.com
http:
paths: #通过path来区分不同的环境
- path: /v1
backend:
serviceName: tomcat1 #指定svc 名称
servicePort: 8080 #svc 端口
- path: /v2
backend:
serviceName: tomcat2
servicePort: 8080
- path: / #这里代表默认/,不加任何参数访问的的svc
backend:
serviceName: tomcat3
servicePort: 8080
#这里需要将我们的path /放到最后,这里的path也是优先级的,如果将/放到最上面,很有可能无法匹配到下面的v1和v2
[root@k8s-master ingress]# kubectl apply -f test-ingress.yaml
ingress.extensions/tomcat-web created
查看ingress:
[root@k8s-master ingress]# kubectl get ing
NAME HOSTS ADDRESS PORTS AGE
tomcat-web tomcat.allenjol.com 80 35s
[root@k8s-master ingress]# kubectl describe ingress tomcat-web
Name: tomcat-web
Namespace: default
Address:
Default backend: default-http-backend:80 (<none>)
Rules:
Host Path Backends
---- ---- --------
tomcat.allenjol.com
/v1 tomcat1:8080 (172.20.1.38:8080)
/v2 tomcat2:8080 (172.20.2.39:8080)
/ tomcat3:8080 (172.20.1.39:8080)
Annotations:
kubectl.kubernetes.io/last-applied-configuration: {"apiVersion":"extensions/v1beta1","kind":"Ingress","metadata":{"annotations":{"kubernetes.io/ingress.class":"traefik","traefik.frontend.rule.type":"PathPrefixStrip"},"name":"tomcat-web","namespace":"default"},"spec":{"rules":[{"host":"tomcat.allenjol.com","http":{"paths":[{"backend":{"serviceName":"tomcat1","servicePort":8080},"path":"/v1"},{"backend":{"serviceName":"tomcat2","servicePort":8080},"path":"/v2"},{"backend":{"serviceName":"tomcat3","servicePort":8080},"path":"/"}]}}]}}
kubernetes.io/ingress.class: traefik
traefik.frontend.rule.type: PathPrefixStrip
Events: <none>
上面可以看到我们的域名已经有对应的Path,以及svc名称和端口,括号里面的是pod ip
更改本地hosts文件,添加tomcat.allenjol.com解析就能访问了192.168.2.220 tomcat.allenjol.com
五、访问成功后配置https
这次取名叫traefik-ssl 命名空间和tomcat-web在同一个下面:用前面的证书也是可以的。
kubectl create secret generic traefik-ssl --from-file=tls.crt --from-file=tls.key
修改tomcat-ingress文件
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: tomcat-web
annotations:
kubernetes.io/ingress.class: traefik
traefik.frontend.rule.type: PathPrefixStrip
spec:
tls: #这里添加我们的secret证书,但是这里我们还是用之前的证书
- secretName: traefik-cert #这里是secret的名称,也就是我们挂载证书的地方,我这里使用之前创建的,如果新的只需要从新挂载一下设置一下名称就可以
rules:
- host: tomcat.i4t.com
http:
paths:
- path: /v1
backend:
serviceName: tomcat1 #指定svc 名称
servicePort: 8080 #svc 端口
- path: /v2
backend:
serviceName: tomcat2
servicePort: 8080
- path: /
backend:
serviceName: tomcat3
servicePort: 8080
更改后应用访问:
kubectl apply -f test-ingress.yaml
会发现有提示https的证书不安全。这里实际上就会和咱们上面的截图一样了。只不过我这里证书就是为traefik生成的,这里也直接引用了。所以上面访问就看到是不安全证书提醒了
完
------------------------------------------------------
公众号:竹下侯小姜运维
个人博客:https://www.ayunw.cn
重要的事情认真做,普通的事情规范做!
------------------------------------------------------
不定期更新优质内容,技术干货!如果觉得对你有帮助,请扫描下方二维码关注!

温馨提示
如果你喜欢本文,请分享到朋友圈,想要获得更多信息,请关注我!






