公众号关注「WeiyiGeek」
设为「特别关注」,每天带你玩转网络安全运维、应用开发、物联网IOT学习!

本章目录:
0x01 使用 nerdctl 工具配合 Containerd 替代 Docker
1.使用懒加载加速图像拉取(eStargz)
2.配置高速的 rootless 模式
介绍 nerdctl 工具
安装 nerdctl 工具
使用 nerdctl 工具
工具 nerdctl 命令
有趣的实验功能
实践.使用 containerd & nerdctl 工具快速部署 redis 数据库服务容器
入坑出坑
原文地址: https://blog.weiyigeek.top/2021/6-30-581.html
0x01 使用 nerdctl 工具配合 Containerd 替代 Docker
描述: Containerd 是一个工业级标准的容器运行时,它强调简单性、健壮性和可移植性。Containerd 可以在宿主机中管理完整的容器生命周期:容器镜像的传输和存储、容器的执行和管理、存储和网络等
学过Docker的童鞋都知道, 我们利用docker-cli与docker-compose工具能帮助快速的进行镜像和容器的相关操作。自从 Containerd 发布 1.5 以后,Kubernetes 的CRI接口使用 Containerd 来替代 dockershim 时, 我们便可以使用 nerdctl 工具(替代 docker cli) 配合 Containerd 的情况下基本已经可以替换掉 Docker 和 Docker Compose;
介绍 nerdctl 工具
什么是nerdctl?nerdctl 是 与 Docker 兼容的CLI for Containerd,其支持Compose、Rootless、eStargz、OCIcrypt和IPFS,与docker命令行语法类似,所以其上手使用非常简单😊。
nerdctl 官方发布包包含两个安装版本:
Minimal: 仅包含 nerdctl 二进制文件以及 rootless 模式下的辅助安装脚本Full: 看名字就能知道是个全量包,其包含了 Containerd、CNI、runc、BuildKit 等完整组件
项目地址:GitHub - containerd/nerdctl: Docker-compatible CLI for containerd, with support for Compose ( https://github.com/containerd/nerdctl )
安装 nerdctl 工具
最新nerdctl版本releases下载地址: https://github.com/containerd/nerdctl/releases
Step 1.从Github Release页面中下载适用于你系统的 Full 包,当前最新版本【2022年4月25日 11:22:59】为v.0.19.0。
# 断点与后台下载# 全量包wget -c -b https://github.com/containerd/nerdctl/releases/download/v0.19.0/nerdctl-full-0.19.0-linux-amd64.tar.gz# 仅包含 nerdctl 二进制wget -c -b https://github.com/containerd/nerdctl/releases/download/v0.19.0/nerdctl-0.19.0-linux-amd64.tar.gz
Step 2.下载完成后解压然后进行相应的安装操作。
# 1.安装仅包含 nerdctl 二进制文件包 (Minimal - 不推荐)tar Cxzvvf usr/local/bin nerdctl-0.19.0-linux-amd64.tar.gz # -rwxr-xr-x root/root 27578368 2022-04-22 12:03 nerdctl # -rwxr-xr-x root/root 21562 2022-04-22 12:02 containerd-rootless-setuptool.sh # -rwxr-xr-x root/root 7032 2022-04-22 12:02 containerd-rootless.shcd usr/local/bin && ./containerd-rootless-setuptool.sh install # 注意不能以root用户运行# 2.安装 nerdctl 全量包 (Full - 推荐)tar Cxzvvf usr/local nerdctl-full-0.19.0-linux-amd64.tar.gz # drwxr-xr-x 0/0 0 2022-04-22 12:16 bin/ # -rwxr-xr-x 0/0 25371420 2015-10-21 08:00 bin/buildctl # -rwxr-xr-x 0/0 39651613 2015-10-21 08:00 bin/buildkitd # drwxr-xr-x 0/0 0 2022-04-22 12:16 share/doc/nerdctl-full/ # -rw-r--r-- 0/0 1135 2022-04-22 12:16 share/doc/nerdctl-full/README.md # -rw-r--r-- 0/0 5425 2022-04-22 12:16 share/doc/nerdctl-full/SHA256SUMS# 3.初始化安装以全量包为例,如出现如下命令表示安装成功。/usr/local/bin$ ./containerd-rootless-setuptool.sh install # + systemctl --user enable containerd.service # Created symlink home/weiyigeek/.config/systemd/user/default.target.wants/containerd.service → home/weiyigeek/.config/systemd/user/containerd.service. # [INFO] Installed "containerd.service" successfully. # [INFO] To control "containerd.service", run: `systemctl --user (start|stop|restart) containerd.service` # [INFO] To run "containerd.service" on system startup automatically, run: `sudo loginctl enable-linger weiyigeek` # [INFO] ------------------------------------------------------------------------------------------ # [INFO] Use `nerdctl` to connect to the rootless containerd. # [INFO] You do NOT need to specify $CONTAINERD_ADDRESS explicitly.
Step 3.启动 containerd 和 buildkitd 服务。
# 启动 containerd && 验证服务状态systemctl enable --now containerd && systemctl restart containerd && systemctl status containerd# 启用 BuildKit 为了构建 Dockerfile,您需要使用以下命令启用 BuildKit。/usr/local/bin$ CONTAINERD_NAMESPACE=default containerd-rootless-setuptool.sh install-buildkit-containerd # [INFO] Creating "/home/weiyigeek/.config/systemd/user/default-buildkit.service" # [INFO] Starting systemd unit "default-buildkit.service" # + systemctl --user start default-buildkit.service # + sleep 3 # + systemctl --user --no-pager --full status default-buildkit.service # ● default-buildkit.service - BuildKit (Rootless) # Loaded: loaded (/home/weiyigeek/.config/systemd/user/default-buildkit.service; disabled; vendor preset: enabled) # Active: active (running) since Mon 2022-04-25 13:05:25 CST; 3s ago # Main PID: 329750 (buildkitd) # CGroup: user.slice/user-1000.slice/user@1000.service/default-buildkit.service # └─329750 buildkitd --addr=unix:///run/user/1000/buildkit-default/buildkitd.sock --root=/home/weiyigeek/.local/share/buildkit-default --containerd-worker-namespace=default # Apr 25 13:05:25 node-2 systemd[327840]: Started BuildKit (Rootless). # Apr 25 13:05:26 node-2 containerd-rootless-setuptool.sh[329750]: time="2022-04-25T13:05:26+08:00" level=info msg="found worker \"ffl4pd8j6x7fh6t9o85a70l11\", labels=map[org.mobyproject.buildkit.worker.containerd.namespace:default org.mobyproject.buildkit.worker.containerd.uuid:4f029882-9edc-4c20-ab49-0363abe0d40e org.mobyproject.buildkit.worker.executor:containerd org.mobyproject.buildkit.worker.hostname:node-2 org.mobyproject.buildkit.worker.network:host org.mobyproject.buildkit.worker.snapshotter:overlayfs], platforms=[linux/amd64 linux/amd64/v2 linux/amd64/v3 linux/386]" # Apr 25 13:05:26 node-2 containerd-rootless-setuptool.sh[329750]: time="2022-04-25T13:05:26+08:00" level=info msg="found 1 workers, default=\"ffl4pd8j6x7fh6t9o85a70l11\"" # Apr 25 13:05:26 node-2 containerd-rootless-setuptool.sh[329750]: time="2022-04-25T13:05:26+08:00" level=warning msg="currently, only the default worker can be used." # Apr 25 13:05:26 node-2 containerd-rootless-setuptool.sh[329750]: time="2022-04-25T13:05:26+08:00" level=info msg="running server on run/user/1000/buildkit-default/buildkitd.sock" # + systemctl --user enable default-buildkit.service # Created symlink home/weiyigeek/.config/systemd/user/default.target.wants/default-buildkit.service → home/weiyigeek/.config/systemd/user/default-buildkit.service. # [INFO] Installed "default-buildkit.service" successfully. # [INFO] To control "default-buildkit.service", run: `systemctl --user (start|stop|restart) default-buildkit.service`
Step 4.查看nerdctl工具执行结果及其版本,至此安装完毕
~$ nerdctl --versionnerdctl version 0.19.0使用 nerdctl 工具
描述: 在某一个用户执行时nerdctl命令时,我们可以其家目录中创建一个如下路径文件/home/weiyigeek/.config/nerdctl/nerdctl.toml
,该文件可配置包含nerdctl相关配置项目。
简述尝试
Step 1.镜像拉取与查看
$ nerdctl pull hello-world:latest # docker.io/library/hello-world:latest: resolved |++++++++++++++++++++++++++++++++++++++| # index-sha256:10d7d58d5ebd2a652f4d93fdd86da8f265f5318c6a73cc5b6a9798ff6d2b2e67: done |++++++++++++++++++++++++++++++++++++++| # manifest-sha256:f54a58bc1aac5ea1a25d796ae155dc228b3f0e11d046ae276b39c4bf2f13d8c4: done |++++++++++++++++++++++++++++++++++++++| # config-sha256:feb5d9fea6a5e9606aa995e879d862b825965ba48de054caab5ef356dc6b3412: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:2db29710123e3e53a794f2694094b9b4338aa9ee5c40b930cb8063a1be392c54: done |++++++++++++++++++++++++++++++++++++++| # elapsed: 34.3s total: 6.9 Ki (205.0 B/s)$ nerdctl image ls # REPOSITORY TAG IMAGE ID CREATED PLATFORM SIZE BLOB SIZE # hello-world latest 10d7d58d5ebd 31 seconds ago linux/amd64 20.0 KiB 6.9 KiB
Step 2.运行拉取的 hello-world 镜像
# 创建并后台运行一个名为 hello-containerd 的容器$ nerdctl run -d --privileged --name hello-containerd hello-world:latest # 17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d# 查看 hello-containerd 容器日志$ nerdctl logs hello-containerd # Hello from Docker! # This message shows that your installation appears to be working correctly. # ....... # Share images, automate workflows, and more with a free Docker ID: https://hub.docker.com/ # For more examples and ideas, visit:https://docs.docker.com/get-started/
Step 3.查看创建的容器相关信息以及删除容器。
# 容器查看$ nerdctl ps -a # CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES # 17cc212e69b2 docker.io/library/hello-world:latest "/hello" 2 minutes ago Exited (0) 2 minutes ago hello-containerd# 容器详细信息$ nerdctl inspect 17cc212e69b2[ { "Id": "17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d", "Created": "2022-04-25T05:13:16.690822727Z", "Path": "/hello", "Args": null, "State": { "Status": "exited", "Running": false, "Paused": false,"Pid": 330226, "ExitCode": 0,"FinishedAt": "2022-04-25T05:13:17.251972898Z"}, "Image": "docker.io/library/hello-world:latest", "ResolvConfPath": "/home/weiyigeek/.local/share/nerdctl/1935db59/containers/default/17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d/resolv.conf", "HostnamePath": "/home/weiyigeek/.local/share/nerdctl/1935db59/containers/default/17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d/hostname", "LogPath": "/home/weiyigeek/.local/share/nerdctl/1935db59/containers/default/17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d/17cc212e69b2387b0aa1e4c4e679e41072eeeb14f909fff2acdb24d3c1033c0d-json.log", "Name": "hello-containerd", "Driver": "overlayfs", "Platform": "linux", "AppArmorProfile": "", "Mounts": null, "NetworkSettings": null }]# 移除 hello-containerd 容器$ nerdctl rm hello-containerdhello-containerd
Step 4.删除指定 hello-world 镜像
$ nerdctl rmi hello-worldUntagged: docker.io/library/hello-world:latest@sha256:10d7d58d5ebd2a652f4d93fdd86da8f265f5318c6a73cc5b6a9798ff6d2b2e67Deleted: sha256:e07ee1baac5fae6a26f30cabfe54a36d3402f96afda318fe0a96cec4ca393359
Step 5.我们也可以拉取 nginx:alpine 镜像并创建、后台运行nginx容器、进入容器内部。
$ sudo nerdctl run -d --name nginx -p 80:80 nginx:alpine # docker.io/library/nginx:alpine: resolved |++++++++++++++++++++++++++++++++++++++| # index-sha256:5a0df7fb7c8c03e4158ae9974bfbd6a15da2bdfdeded4fb694367ec812325d31: done |++++++++++++++++++++++++++++++++++++++| # manifest-sha256:efc09388b15fb423c402f0b8b28ca70c7fd20fe31f8d7531ae1896bbb4944999: done |++++++++++++++++++++++++++++++++++++++| # config-sha256:51696c87e77e4ff7a53af9be837f35d4eacdb47b4ca83ba5fd5e4b5101d98502: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:4071be97c256d6f5ab0e05ebdebcfec3d0779a5e199ad0d71a5fccba4b3e2ce4: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:df9b9388f04ad6279a7410b85cedfdcb2208c0a003da7ab5613af71079148139: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:5867cba5fcbd3ae827c5801e76d20e7dc91cbb626ac5c871ec6c4d04eb818b16: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:4b639e65cb3ba47e77db93f93c6625a62ba1b9eec99160b254db380115ae009d: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:061ed9e2b9762825b9869a899a696ce8b56e7e0ec1e1892b980969bf7bcda56a: done |++++++++++++++++++++++++++++++++++++++| # layer-sha256:bc19f3e8eeb1bb75268787f8689edec9a42deda5cdecdf2f95b3c6df8eb57a48: done |++++++++++++++++++++++++++++++++++++++| # elapsed: 33.7s total: 9.7 Mi (294.8 KiB/s) # 98eb2f1d4639b173dc21c30e40be5f3e2c410e4ca325b6bd6bafcaab46ab6c11# 查看创建的nginx容器$ sudo nerdctl ps # CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES # 98eb2f1d4639 docker.io/library/nginx:alpine "/docker-entrypoint.…" About an hour ago Up 0.0.0.0:80->80/tcp nginx# 进入nginx容器内部$ nerdctl exec -it nginx -- sh/ # whoamiroot/ # ip addr1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever2: eth0@if4: <BROADCAST,MULTICAST,UP,LOWER_UP,M-DOWN> mtu 1500 qdisc noqueue state UP link/ether ee:e6:a6:9a:07:48 brd ff:ff:ff:ff:ff:ff inet 10.4.0.2/24 brd 10.4.0.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::ece6:a6ff:fe9a:748/64 scope link valid_lft forever preferred_lft forever/usr/share/nginx/html # hostname > index.html/usr/share/nginx/html # ip addr >> index.html# 访问创建的nginx容器 或者 浏览器访问 10.10.107.227 宿主机$ curl -I localhost
Step 6.nginx 容器详细信息查看与容器停止、删除。
$ nerdctl inspect --format "{{ .Name }} {{ .Id }}" nginx # nginx 98eb2f1d4639b173dc21c30e40be5f3e2c410e4ca325b6bd6bafcaab46ab6c11$ nerdctl stop nginx # nginx$ nerdctl ps -a # CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES # 98eb2f1d4639 docker.io/library/nginx:alpine "/docker-entrypoint.…" 2 hours ago Exited (0) 4 seconds ago 0.0.0.0:80->80/tcp nginx$ nerdctl rm nginxnginx

温馨提示: 不知读者是否发现, 其子命令及其使用方法与docker客户端工具基本是类似的,所以前面说到其学习成本较低, 熟悉docker的朋友可以快速上手
工具 nerdctl 命令
描述 : nerdctl 是 containerd 的命令行界面的工具。
命令参数:
# Usage: nerdctl [flags] nerdctl [command]# Management commands: apparmor Manage AppArmor profiles builder Manage builds container Manage containers image Manage images ipfs Distributing images on IPFS namespace Manage containerd namespaces network Manage networks system Manage containerd volume Manage volumesCommands: build Build an image from a Dockerfile. Needs buildkitd to be running. commit Create a new image from a container changes completion Generate the autocompletion script for the specified shell compose Compose cp Copy files/folders between a running container and the local filesystem. create Create a new container. Optionally specify "ipfs://" or "ipns://" scheme to pull image from IPFS. events Get real time events from the server exec Run a command in a running container help Help about any command history Show the history of an image images List images info Display system-wide information inspect Return low-level information on objects. kill Kill one or more running containers load Load an image from a tar archive or STDIN login Log in to a Docker registry logout Log out from a Docker registry logs Fetch the logs of a container. Currently, only containers created with `nerdctl run -d` are supported. pause Pause all processes within one or more containers port List port mappings or a specific mapping for the container ps List containers pull Pull an image from a registry. Optionally specify "ipfs://" or "ipns://" scheme to pull image from IPFS. push Push an image or a repository to a registry. Optionally specify "ipfs://" or "ipns://" scheme to push image to IPFS. restart Restart one or more running containers rm Remove one or more containers rmi Remove one or more images run Run a command in a new container. Optionally specify "ipfs://" or "ipns://" scheme to pull image from IPFS. save Save one or more images to a tar archive (streamed to STDOUT by default) start Start one or more running containers stats Display a live stream of container(s) resource usage statistics. stop Stop one or more running containers tag Create a tag TARGET_IMAGE that refers to SOURCE_IMAGE top Display the running processes of a container unpause Unpause all processes within one or more containers update Update one or more running containers version Show the nerdctl version information wait Block until one or more containers stop, then print their exit codes.# Flags: -H, --H string Alias of --address (default "/run/containerd/containerd.sock") -a, --a string Alias of --address (default "/run/containerd/containerd.sock") --address string containerd address, optionally with "unix://" prefix [$CONTAINERD_ADDRESS] (default "/run/containerd/containerd.sock") --cgroup-manager string Cgroup manager to use ("cgroupfs"|"systemd") (default "none") --cni-netconfpath string cni config directory [$NETCONFPATH] (default "/home/weiyigeek/.config/cni/net.d") --cni-path string cni plugins binary directory [$CNI_PATH] (default "/usr/local/libexec/cni") --data-root string Root directory of persistent nerdctl state (managed by nerdctl, not by containerd) (default "/home/weiyigeek/.local/share/nerdctl") --debug debug mode --debug-full debug mode (with full output) -h, --help help for nerdctl --host string Alias of --address (default "/run/containerd/containerd.sock") --hosts-dir strings A directory that contains <HOST:PORT>/hosts.toml (containerd style) or <HOST:PORT>/{ca.cert, cert.pem, key.pem} (docker style) (default [/home/weiyigeek/.config/containerd/certs.d,/home/weiyigeek/.config/docker/certs.d]) --insecure-registry skips verifying HTTPS certs, and allows falling back to plain HTTP -n, --n string Alias of --namespace (default "default") , 支持名称空间。 --namespace string containerd namespace, such as "moby" for Docker, "k8s.io" for Kubernetes [$CONTAINERD_NAMESPACE] (default "default") --snapshotter string containerd snapshotter [$CONTAINERD_SNAPSHOTTER] (default "overlayfs") --storage-driver string Alias of --snapshotter (default "overlayfs") -v, --version version for nerdctl
nerdctl 使用示例
仓库认证
$ nerdctl login -u weiyigeek index.docker.io # Enter Password: # WARNING: Your password will be stored unencrypted in root/.docker/config.json. Configure a credential helper to remove this warning. See # https://docs.docker.com/engine/reference/commandline/login/#credentials-store # Login Succeeded$ nerdctl logout # Removing login credentials for https://index.docker.io/v1/
镜像操作
# 拉取nerdctl pull docker.io/library/nginx:alpinenerdctl -n k8s.io pull docker.io/library/nginx:alpine# 查看nerdctl -n default image lsnerdctl -n default inspect nginx:alpine# 删除nerdctl -n default rmi nginx:alpine
容器操作
# 创建运行容器sudo nerdctl -n default run -d --name nginx -p 80:80 nginx:alpinesudo nerdctl -n k8s.io run -d --privileged --restart=always --name rancher -p 80:80 -p 443:443 docker.io/cnrancher/rancher:v2.4.17-ent# 查看容器sudo nerdctl -n k8s.io ps -asudo nerdctl -n k8s.io inpsect rancher# 进入容器内部sudo nerdctl -n k8s.io exec rancher -- sh# 停止容器sudo nerdctl -n k8s.io stop rancher# 删除容器sudo nerdctl -n k8s.io rm rancher
有趣的实验功能
描述: 我在验证环境中使用时发现特别吸引人的最新功能一个是图像快速拉取(eStargz), 另外一个是高速 rootless 模式。
1.使用懒加载加速图像拉取(eStargz)
描述: 在过去的一年中,可以在容器相关的工具(包括Kubernetes,contained,nerdctl,CRI-O,Podman,BuildKit,Kaniko
等)上使用eStargz镜像的懒拉取功能, 在2021年懒拉取将成为越来越普遍的镜像分发技术,并且正在把eStargz增加到OCI容器镜像规范当中。
从 1.4 版开始 Containered 支持懒拉取, Stargz Snapshotter 是使 containerd 能够处理eStargz的插件。这是一种用于懒拉取的镜像分发技术。这使容器运行时无需等待整个镜像内容即可启动容器。取而代之的是,按需获取必要的内容块(例如单个文件)。这样可以将容器启动延迟从数十秒缩短到最佳的几秒。
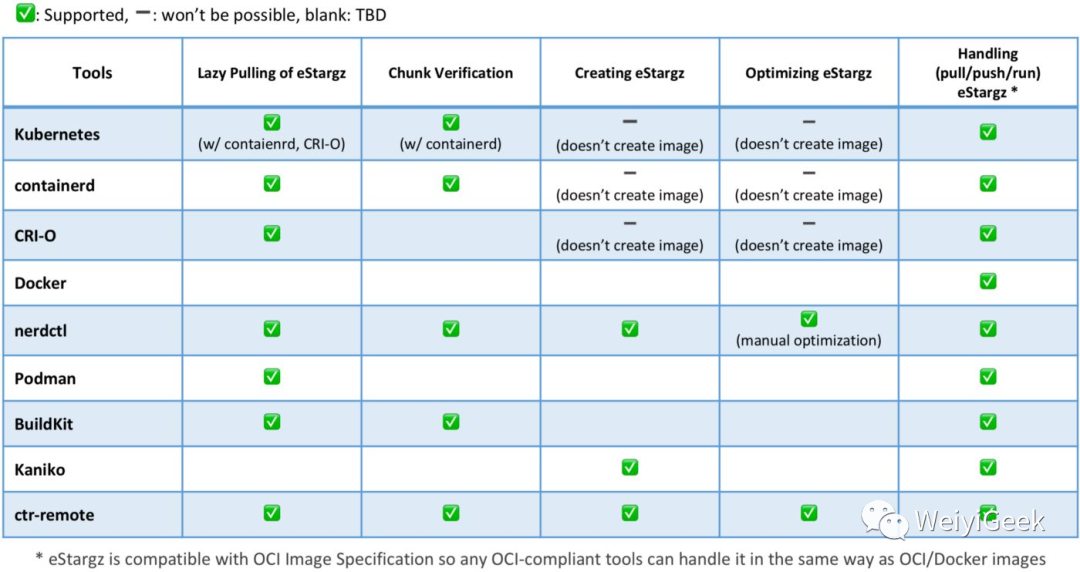
配置参考地址: https://github.com/containerd/nerdctl/blob/master/docs/rootless.md#stargz-snapshotter
我们将继续执行如下步骤, 以启用图像拉取的加速(延迟拉取), 即加速镜像拉取。
实践操作
1.安装与启用 Stargz 快照程序。
/usr/local/bin$ containerd-rootless-setuptool.sh install-stargz[INFO] Creating "/home/cqzk/.config/systemd/user/stargz-snapshotter.service"[INFO] Starting systemd unit "stargz-snapshotter.service"+ systemctl --user start stargz-snapshotter.service+ sleep 3+ systemctl --user --no-pager --full status stargz-snapshotter.service...........[INFO] Installed "stargz-snapshotter.service" successfully.[INFO] To control "stargz-snapshotter.service", run: `systemctl --user (start|stop|restart) stargz-snapshotter.service`[INFO] Add the following lines to "/home/cqzk/.config/containerd/config.toml" manually, and then run `systemctl --user restart containerd.service`:### BEGIN ###[proxy_plugins] [proxy_plugins."stargz"] type = "snapshot" address = "/run/user/1000/containerd-stargz-grpc/containerd-stargz-grpc.sock"### END ###[INFO] Set `export CONTAINERD_SNAPSHOTTER="stargz"` to use the stargz snapshotter.
2.准备一个包含以下 containerd 内容的配置, 为了安全我们可以指定一个用户, 例如使用 nerdctl 的用户的 UID 为 1000 的配置放置位置为/run/user/1000
。
# 确认方法当前用户UID$ echo $UID1000# 在 containerd 配置文件中启用该插件tee ~/.config/containerd/config.toml <<'EOF'# Plug stargz snapshotter into containerd# Containerd recognizes stargz snapshotter through specified socket address.[proxy_plugins] [proxy_plugins."stargz"] type = "snapshot" # NOTE: replace "1000" with your actual UID address = "/run/user/1000/containerd-stargz-grpc/containerd-stargz-grpc.sock"# Use stargz snapshotter through CRIEOF
3.重新启动 restargz-snapshotter 与 containerd 以使配置更改生效。
systemctl daemon-reload systemctl --user start restargz-snapshotter.service && systemctl --user restart containerd.servicesystemctl status stargz-snapshotter.service && systemctl status containerd.service● stargz-snapshotter.service - stargz snapshotter (Rootless) Loaded: loaded (/home/cqzk/.config/systemd/user/stargz-snapshotter.service; enabled; vendor preset: enabled) Active: active (running) since Mon 2022-04-25 16:48:56 CST; 7s ago Main PID: 360664 (containerd-star) CGroup: user.slice/user-1000.slice/user@1000.service/stargz-snapshotter.service └─360664 containerd-stargz-grpc -address run/user/1000/containerd-stargz-grpc/containerd-stargz-grpc.sock -root home/cqzk/.local/share/containerd-stargz-grpc -config home/cqzk/.config/container>Apr 25 16:48:56 node-2 systemd[358295]: Started stargz snapshotter (Rootless).
4.您可以选择执行以下命令,并指定使用--snapshotter=stargz
进行快速图像拉取。
export CONTAINERD_SNAPSHOTTER="stargz"nerdctl run --snapshotter=stargz ghcr.io/stargz-containers/python:3.10-esgz python -c "print('hello')"
2.配置高速的 rootless 模式
描述: Rootless模式允许你在没有特权的情况下运行容器,具有安全优势,但它的缺点是容器外的通信速度比特权 Rootful 模式慢。
但是我们可以通过使用 bypass4netns, 使得 Rootless 的容器外通信速度将比 Rootful 更快, 操作如下所示:
1.安装与启用 bypass4netns
/usr/local/bin$ containerd-rootless-setuptool.sh install-bypass4netnsd
2.您可以选择执行如下命令,使用快速无根功能启动容器和以下--label nerdctl/bypass4netns=true
参数快速图像拉取。
$ nerdctl run --label nerdctl/bypass4netns=true ghcr.io/stargz-containers/python:3.10-esgz python -c "print('hello')"
实践.使用 containerd & nerdctl 工具快速部署 redis 数据库服务容器
Step 1.准备 redis 数据库配置文件极其相关目录
mkdir -vp app/redis/datatee app/redis/redis.conf <<'EOF'# 绑定任意接口、服务端口、后台运行。bind 0.0.0.0port 6379# 容器里必须设置为nodaemonize nosupervised auto# redis服务pid进程文件名pidfile "/var/run/redis.pid"# 关闭保护模式,并配置使用密码访问protected-mode norequirepass "123456"# echo -e "weiyigeek"|sha256sum # requirepass 097575a79efcd7ea7b1efa2bcda78a4fc7cbd0820736b2f2708e72c3d21f8b61# 数据文件保存路径,rdb/AOF文件也保存在这里dir "/data"# 日志文件记录文件(notice verbose)# logfile "/logs/redis.log"# loglevel verbose # 最大客户端连接数maxclients 10000# 客户端连接空闲多久后断开连接,单位秒,0表示禁用timeout 60tcp-keepalive 60 # Redis 数据持久化(rdb/aof)配置# RDB 文件名dbfilename "dump.rdb"# 数据自动保存脚本条件例如300s中有10key发生变化save 300 10save 60 10000# 对RDB文件进行压缩,建议以(磁盘)空间换(CPU)时间。rdbcompression yes# 版本5的RDB有一个CRC64算法的校验和放在了文件的最后。这将使文件格式更加可靠。rdbchecksum yes# RDB自动触发策略是否启用,默认为yesrdb-save-incremental-fsync yes# AOF开启appendonly yes# AOF文件名appendfilename "appendonly.aof"# 可选值 always, everysec,no,建议设置为everysecappendfsync everysec# Redis风险命令重命名# rename-command CONFIG b840fc02d524045429941cc15f59e41cb7be6c52rename-command FLUSHDB b840fc02d524045429941cc15f59e41cb7be6c53rename-command FLUSHALL b840fc02d524045429941cc15f59e41cb7be6c54rename-command EVAL b840fc02d524045429941cc15f59e41cb7be6c55rename-command DEBUG b840fc02d524045429941cc15f59e41cb7be6c56# rename-command SHUTDOWN SHUTDOWNEOF
Step 2.执行如下命令进行快速创建容器并运行redis服务。
$ nerdctl run -d -p 6379:6379 \ -v app/redis/redis.conf:/etc/redis/redis.conf \ -v app/redis/data:/data \ --name redis-server redis:6.2.6-alpine3.15 redis-server etc/redis/redis.conf5e854a58087ae1bba5a661b2941474560cbecc37f54c7f4e7a28afbaed6aebf0Step 3.查看创建的容器并验证redis服务是否正常。
$ nerdctl psCONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES5e854a58087a docker.io/library/redis:6.2.6-alpine3.15 "docker-entrypoint.s…" 42 seconds ago Up 0.0.0.0:6379->6379/tcp redis-server$ nerdctl logs redis-server1:C 25 Apr 2022 13:22:59.597 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo1:C 25 Apr 2022 13:22:59.597 # Redis version=6.2.6, bits=64, commit=00000000, modified=0, pid=1, just started1:C 25 Apr 2022 13:22:59.597 # Configuration loaded# 如下返回,表示 redis 服务状态是正常的$ nerdctl exec -it redis-server redis-cli -a 123456 pingPONG$ nerdctl exec -it redis-server redis-cli -a 123456 info# Serverredis_version:6.2.6redis_git_sha1:00000000redis_git_dirty:0redis_build_id:63421500bb103677redis_mode:standaloneos:Linux 5.4.0-96-generic x86_64arch_bits:64multiplexing_api:epollatomicvar_api:atomic-builtin
Step 4.这里我们直接用telnet工具连接创建的redis容器中的redis数据库服务。
$ telnet 10.10.107.227 6379Trying 10.10.107.227...Connected to 10.10.107.227.Escape character is '^]'.auth 123456 # 认证+OKping # 服务验证+PONG set name weiyigeek # 设置 字符串 类型的key+OKget name # 获取 key 的值$9weiyigeek
入坑出坑
错误1.安装nerdctl(Minimal)时执行containerd-rootless-setuptool.sh脚本安装时报
[ERROR] Refusing to install rootless containerd as the root user
错误解决办法: 请切换到普通用户执行。错误2.安装nerdctl(Minimal)时执行containerd-rootless-setuptool.sh脚本安装时报
containerd-rootless-setuptool.sh: 110: rootlesskit: Permission denied
错误
/usr/local/bin$ containerd-rootless-setuptool.sh install[INFO] Checking RootlessKit functionality/usr/local/bin/containerd-rootless-setuptool.sh: 110: rootlesskit: Permission denied
问题原因: 由于未安装 rootlesskit 相关依赖工具
解决办法: 执行如下命令进行安装操作 apt install -y rootlesskit rootlessctl
错误3.安装nerdctl (full) 时执行containerd-rootless-setuptool.sh脚本安装时报
exec: "newuidmap": executable file not found in $PATH
错误
./containerd-rootless-setuptool.sh install
[INFO] Checking RootlessKit functionality
[rootlesskit:parent] error: failed to setup UID/GID map: newuidmap 328299 [0 1000 1 1 100000 65536] failed: : exec: "newuidmap": executable file not found in $PATH
问题原因: newuidmap 在没有安装的环境下会出现上述错误,所以执行apt命令安装uidmap软件包。
解决版本: sudo apt install uidmap
本文至此完毕,更多技术文章,尽情期待下一章节!
原文地址: https://blog.weiyigeek.top/2021/6-30-581.html
欢迎各位志同道合的朋友一起学习交流,如文章有误请在下方留下您宝贵的经验知识,个人邮箱地址【master#weiyigeek.top】
或者个人公众号【WeiyiGeek】
联系我。
更多文章来源于【WeiyiGeek Blog 个人博客 - 为了能到远方,脚下的每一步都不能少 】
个人主页: 【 https://weiyigeek.top】
博客地址: 【 https://blog.weiyigeek.top 】
专栏书写不易,如果您觉得这个专栏还不错的,请给这篇专栏 【点个赞、投个币、收个藏、关个注,转个发,留个言】(人间六大情),这将对我的肯定,谢谢!。

echo "【点个赞】,动动你那粗壮的拇指或者芊芊玉手,亲!"
printf("%s", "【投个币】,万水千山总是情,投个硬币行不行,亲!")
fmt.Printf("【收个藏】,阅后即焚不吃灰,亲!")
console.info("【转个发】,让更多的志同道合的朋友一起学习交流,亲!")
System.out.println("【关个注】,后续浏览查看不迷路哟,亲!")
cout << "【留个言】,文章写得好不好、有没有错误,一定要留言哟,亲! " << endl;
 往期相关文章
往期相关文章
2.基于Containerd运行时搭建Kubernetes集群实践
【转载】使用 RBAC 模型限制对 Kubernetes 资源的访问原理浅析


更多网络安全、系统运维、应用开发、全栈文章,尽在【个人博客 - https://blog.weiyigeek.top】站点,谢谢支持!
↓↓↓ 更多文章,请点击下方阅读原文。






