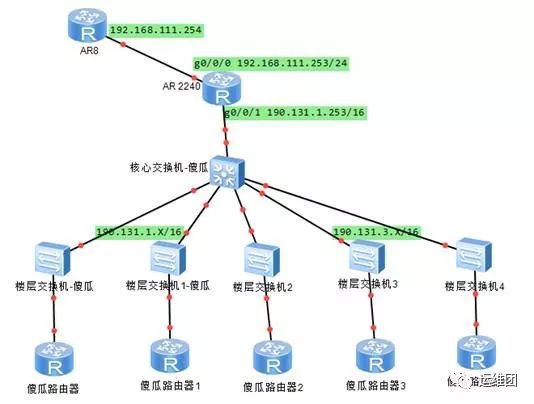
注意:核心和楼层交换机都是傻瓜型的,不能配置。网关在AR路由器上,用户均通过傻瓜路由器接入,傻瓜路由器分为两个网段,分别为190.131.1.0/16和190.131.3.0/16
AR2240 3网段有时不能正常访问外网
查看cpu-defend,发现有丢包
display cpu-defend statistic
-----------------------------------------------------------------------
Packet Type Pass Packets Drop Packets
-----------------------------------------------------------------------
8021X 0 0
arp-miss 5744 0
arp-reply 3903 0
arp-request 448252 1390
bfd 0 0
查看trapbuffer,发现有ARP冲突
#Dec 9 2014 10:09:34+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.131, Local interface=GigabitEthernet0/0/1, Local MAC=0017-59de-b688, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=78a1-067c-7dc1, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
#Dec 9 2014 10:01:44+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.130, Local interface=GigabitEthernet0/0/1, Local MAC=0017-59de-b688, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=78a1-067c-7dbb, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
#Dec 9 2014 09:49:28+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.131, Local interface=GigabitEthernet0/0/1, Local MAC=0017-59de-b688, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=78a1-067c-7dc1, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
#Dec 9 2014 09:34:04+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.133, Local interface=GigabitEthernet0/0/1, Local MAC=7427-eae4-275b, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=0017-59de-b688, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
#Dec 9 2014 09:29:27+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.131, Local interface=GigabitEthernet0/0/1, Local MAC=78a1-067c-7dc1, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=0017-59de-b688, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
#Dec 9 2014 09:21:53+00:00 253_HW_AR2240 ARP/4/ARP_IPCONFLICT_TRAP:OID 1.3.6.1.4.1.2011.5.25.123.2.6 ARP detects IP conflict. (IP address=190.131.3.6, Local interface=GigabitEthernet0/0/1, Local MAC=0021-272e-eb43, Local vlan=0, Local CE vlan=0, Receive interface=GigabitEthernet0/0/1, Receive MAC=0017-59de-b688, Receive vlan=0, Receive CE vlan=0, IP conflict type=Remote IP conflict).
查看AR路由器arp表:见附件“ARP表1”
<253_HW_AR2240>
IP ADDRESS MAC ADDRESS EXPIRE(M) TYPE INTERFACE VPN-INSTANCE
VLAN/CEVLAN PVC
------------------------------------------------------------------------------
192.168.111.253 200b-c723-8910 I - GE0/0/0
192.168.111.254 0019-c600-18ed 18 D-0 GE0/0/0
192.168.111.239 0014-5edc-d306 14 D-0 GE0/0/0
190.131.1.253 200b-c723-8911 I - GE0/0/1
190.131.1.78 5c63-bfd1-7231 20 D-0 GE0/0/1
190.131.1.132 8c21-0a37-ca3d 20 D-0 GE0/0/1
190.131.1.11 78a1-067c-7dc7 9 D-0 GE0/0/1
190.131.1.103 001a-6468-72d9 16 D-0 GE0/0/1
190.131.1.10 78a1-067d-3d4f 9 D-0 GE0/0/1
190.131.1.217 eca8-6b64-e390 20 D-0 GE0/0/1
190.131.1.107 0014-5e7a-75b4 20 D-0 GE0/0/1
190.131.3.121 0017-59de-b688 2 D-0 GE0/0/1
190.131.1.112 cc34-2999-9bbf 17 D-0 GE0/0/1
190.131.3.120 7427-eae4-275b 20 D-0 GE0/0/1
190.131.1.109 0014-5e19-a483 13 D-0 GE0/0/1
190.131.1.199 d815-0d38-3d3d 3 D-0 GE0/0/1
190.131.1.101 0014-5e7a-7574 19 D-0 GE0/0/1
190.131.1.206 0022-3fa5-b237 4 D-0 GE0/0/1
190.131.3.6 0017-59de-b688 18 D-0 GE0/0/1
190.131.1.6 90fb-a61e-13e5 16 D-0 GE0/0/1 //这个应该是正常的傻瓜路由器的MAC
190.131.1.219 001f-c699-aa3f 20 D-0 GE0/0/1
190.131.1.22 001f-c699-aa14 2 D-0 GE0/0/1
190.131.1.248 0200-4c69-9f8c 20 D-0 GE0/0/1
190.131.1.25 000f-1f56-87a8 2 D-0 GE0/0/1
190.131.1.43 4437-e60b-9090 2 D-0 GE0/0/1
190.131.1.65 eca8-6b68-1ba1 20 D-0 GE0/0/1
190.131.1.187 0000-74d6-bea6 4 D-0 GE0/0/1
190.131.1.165 4437-e60b-9108 19 D-0 GE0/0/1
190.131.1.58 001a-6b4e-bf52 4 D-0 GE0/0/1
190.131.1.42 4437-e60b-90d8 20 D-0 GE0/0/1
190.131.1.18 4437-e676-949c 17 D-0 GE0/0/1
190.131.1.212 f8bc-129d-0a50 18 D-0 GE0/0/1
190.131.1.131 001a-4dd5-a389 9 D-0 GE0/0/1
190.131.1.24 b083-fe51-6dbc 20 D-0 GE0/0/1
190.131.1.215 eca8-6b64-e35e 20 D-0 GE0/0/1
190.131.1.62 4437-e60b-364c 2 D-0 GE0/0/1
190.131.1.72 001c-25c5-500d 20 D-0 GE0/0/1
190.131.1.167 4487-fc97-bb47 2 D-0 GE0/0/1
190.131.1.162 4487-fc97-bb68 4 D-0 GE0/0/1
190.131.1.74 4437-e676-6b02 9 D-0 GE0/0/1
190.131.1.44 0001-6c8f-2b9b 8 D-0 GE0/0/1
190.131.1.53 001f-c699-aa1e 20 D-0 GE0/0/1
190.131.1.15 7427-ea61-658d 20 D-0 GE0/0/1
190.131.1.36 4437-e676-bb4c 19 D-0 GE0/0/1
190.131.1.95 4437-e60b-90ae 2 D-0 GE0/0/1
190.131.1.98 001f-c699-aa83 19 D-0 GE0/0/1
190.131.1.56 001f-c699-aa11 2 D-0 GE0/0/1
190.131.1.216 4437-e645-b5b5 18 D-0 GE0/0/1
190.131.1.233 7427-ea3d-e4ef 20 D-0 GE0/0/1
190.131.1.130 0060-6e9a-0d23 2 D-0 GE0/0/1 //这个应该是正常的傻瓜路由器的MAC
190.131.1.45 4437-e649-2aa0 2 D-0 GE0/0/1
190.131.1.85 4437-e645-b506 2 D-0 GE0/0/1
190.131.1.147 4437-e676-8f19 20 D-0 GE0/0/1
190.131.1.52 1234-5612-3456 4 D-0 GE0/0/1
190.131.1.55 001f-c699-7a0c 10 D-0 GE0/0/1
190.131.1.49 90fb-a61e-143d 2 D-0 GE0/0/1
190.131.1.35 eca8-6b6a-62d5 7 D-0 GE0/0/1
190.131.1.1 b083-fe50-9203 17 D-0 GE0/0/1
190.131.1.97 4437-e648-57c8 2 D-0 GE0/0/1
190.131.1.185 0014-2ac3-d9fe 14 D-0 GE0/0/1
190.131.1.126 90fb-a61e-0e10 19 D-0 GE0/0/1
190.131.1.28 b083-fe50-9228 1 D-0 GE0/0/1
190.131.1.31 7427-eae3-7186 19 D-0 GE0/0/1
190.131.1.50 4437-e676-91aa 2 D-0 GE0/0/1
190.131.3.130 0017-59de-b688 17 D-0 GE0/0/1
190.131.3.132 0021-272e-eb43 14 D-0 GE0/0/1
190.131.3.131 0017-59de-b688 5 D-0 GE0/0/1
190.131.3.133 0017-59de-b688 10 D-0 GE0/0/1
190.131.1.20 7427-ea61-660d 20 D-0 GE0/0/1
190.131.1.23 001f-c699-aa45 19 D-0 GE0/0/1
190.131.1.73 7427-ea61-65cf 2 D-0 GE0/0/1
这个包是从镜像抓包里面过滤出来的:
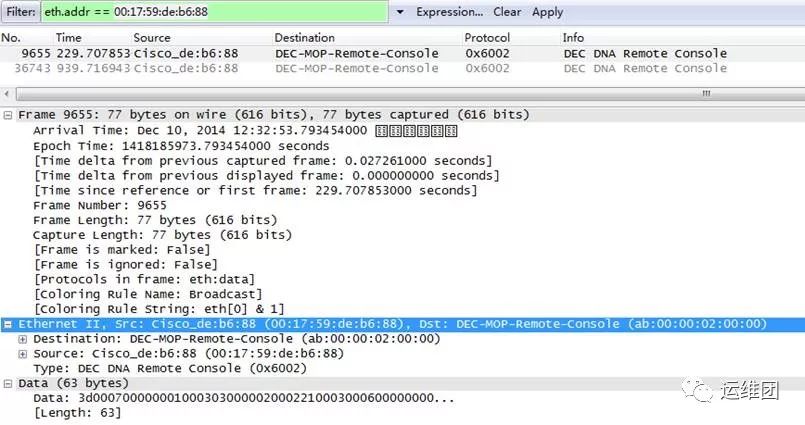
0017-59de-b688处理这种问题的最好方法就是根据冲突的mac地址找到设备,当然这个mac也可能是伪造的
但是现网并没有找到这个mac是哪台设备
当然我们可以采用第二种方案
在AR上 禁止掉这个MAC
如下配置方法
[Huawei]acl number 4444
[Huawei-acl-L2-4444]rule 5 deny l2-protocol arp
source-mac 0017-59de-b688
[Huawei]int g0/0/1
[Huawei-GigabitEthernet0/0/1]traffic-filter
inbound acl 4000
根因ip 冲突导致网络异常
解决方案:在AR路由器上把这个异常mac通过acl 过滤掉
配置方法如下:
[Huawei]acl number 4444
[Huawei-acl-L2-4444]rule 5 deny l2-protocol arp
source-mac 0017-59de-b688
[Huawei]int g0/0/1
[Huawei-GigabitEthernet0/0/1]traffic-filter
inbound acl 4000
测试网络恢复正常
现网中我们经常会遇到这种攻击行为,但是客户并不一定能找的到攻击的设备
然后我们在ar上将其过滤掉,也是一种解决问题的方法






