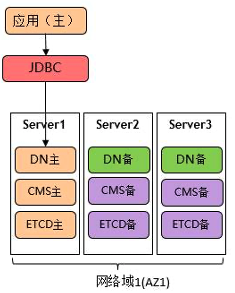
本次安装演示以单AZ3副本集群架构为例,单AZ3副本即一主两备,只有主库可以提供数据读写,两个备库是quorum的同步级别,即any 1(xxx,xxx),保证至少有一个备库的数据与主库保持一致,保证RPO=0;任何一个备库故障,不影响主库数据写入;如果主库故障会自动进行主备切换。
环境准备
硬件信息
(16GB8C100GB / Kylin v10 on x86) * 3
-
操作系统要求:
x86服务器支持Kylin V10 SP1(intel、hygon)
ARM服务器支持Kylin V10 SP1(kunpeng、phytium) -
Python3:
Kylin(X86):仅支持Python 3.7.9
Kylin(arm):仅支持Python 3.7.4
关闭防火墙和SELinux
systemctl stop firewalld
systemctl disable firewalld
systemctl status firewalld
--关闭SELinux
vim /etc/selinux/config
SELINUX=disable
--重启主机
reboot
系统内核参数
--/etc/sysctl.conf
vm.overcommit_memory = 0
vm.overcommit_ratio = 90
kernel.sem = 250 6400000 1000 25600
kernel.shmall = 1152921504606846720
kernel.shmmax = 18446744073709551615
--limits.conf配置文件
echo "* soft nofile 1000000" >>/etc/security/limits.conf
echo "* hard nofile 1000000" >>/etc/security/limits.conf
其他设置
--字符集
建议设置为LANG=zh_CN.UTF-8
--时区时间
各节点间的时间和时区要保持一致,可以自定义同步时钟策略
--关闭swap
swapoff -a
--设置umask
vim /etc/profile
umask 0077
--设置usr的软连接(必做且不可更改)
mkdir -p /opt/rh/python27/root && ln -s /usr /opt/rh/python27/root/usr
--将python路径添加到/etc/sudoers中的secure_path
Defaults secure_path = /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
[root@gaussdb1 usr]# which python
/usr/bin/python
创建用户
groupadd dbgrp
useradd -g dbgrp omm
passwd omm
创建目录
mkdir -p /opt/software/
mkdir -p /home/omm/log/om_agent
mkdir -p /gaussdb/om-agent
mkdir -p /home/omm/CA
mkdir -p /home/omm/sslcrt
mkdir -p /home/omm/demoCA/newcerts
mkdir -p /gaussdb/log /gaussdb/CA /gaussdb/usr/local/package /gaussdb/usr/local/core /gaussdb/usr/local/tool /gaussdb/usr/local/temp /gaussdb/usr/local/cm /gaussdb/usr/local/etcd /gaussdb/usr/local/gtm /gaussdb/usr/local/cn /gaussdb/engine/data1/data
chown -R omm: /opt/software/
chown -R omm: /home/omm
chown -R omm: /gaussdb
安装包处理(所有节点)
解压agent 和 adaptor
注意:对agent压缩包需要进行二次解压
[root@gaussdb1 X86]# ls -l
总用量 513124
-rw-r--r-- 1 root root 193800 12月 13 17:15 'DBS-GaussDBforOpenGauss-Adaptor_1.0.0.1651894270 (1).tar.gz'
-rw-r--r-- 1 root root 13676 12月 13 17:15 'GaussDBInstaller_V1.0.3.2 (1).tar.gz'
-rw-r--r-- 1 root root 5016702 12月 13 17:16 GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_AGENT_PACKAGE.tar.gz
-rw-r--r-- 1 root root 520206672 12月 14 09:32 GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_SERVER_PACKAGE.tar.gz
[root@gaussdb1 X86]#
[root@gaussdb1 X86]# tar -zxvf 'DBS-GaussDBforOpenGauss-Adaptor_1.0.0.1651894270 (1).tar.gz'
[root@gaussdb1 X86]# tar -zxvf GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_AGENT_PACKAGE.tar.gz
GaussDB-Kernel-V500R002C10-KYLIN-64bit-AGENT.tar.gz
[root@gaussdb1 X86]# tar -zxvf GaussDB-Kernel-V500R002C10-KYLIN-64bit-AGENT.tar.gz
[root@gaussdb1 X86]#
[root@gaussdb1 X86]# ll
总用量 518096
drwx------ 7 root root 169 5月 7 2022 adaptor
drwx------ 12 20001 20001 242 9月 24 21:19 agent
-rwx------ 1 20001 20001 7024 9月 24 21:19 cluster_default_agent.xml
-rw-r--r-- 1 root root 193800 12月 13 17:15 'DBS-GaussDBforOpenGauss-Adaptor_1.0.0.1651894270 (1).tar.gz'
-rw-r--r-- 1 root root 13676 12月 13 17:15 'GaussDBInstaller_V1.0.3.2 (1).tar.gz'
-rw-r--r-- 1 20001 20001 5067771 9月 24 21:19 GaussDB-Kernel-V500R002C10-KYLIN-64bit-AGENT.tar.gz
-rw-r--r-- 1 root root 5016702 12月 13 17:16 GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_AGENT_PACKAGE.tar.gz
-rw-r--r-- 1 root root 520206672 12月 14 09:32 GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_SERVER_PACKAGE.tar.gz
-rw------- 1 root root 0 5月 7 2022 __init__.py
drwxr-xr-x 19 20001 20001 4096 9月 24 21:19 lib
-rw-r--r-- 1 20001 20001 43 9月 24 21:19 version.cfg
-rw------- 1 root root 115 5月 7 2022 version.json
对server包进行压缩
这里不是对server包进行解压,相反,是将压缩包放到server目录下,并进行压缩,在后续安装会用到
[root@gaussdb1 X86]# mkdir -p server
[root@gaussdb1 X86]# mv GaussDB_Kernel_V500R002C10SPC510B016_X86_Centralized_SERVER_PACKAGE.tar.gz server/
[root@gaussdb1 X86]# tar -zcvf server.tar.gz server/
[root@gaussdb1 X86]#
证书准备(所有节点)
依赖准备
vim /etc/pki/tls/openssl.cnf
[ CA_default ]
dir = /home/omm/demoCA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
---
su - omm
touch demoCA/index.txt && echo '01' > demoCA/serial
CA证书准备
--生成CA私钥(.key)
# openssl genrsa -aes256 -out ca.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
.......................................+++++
...........................+++++
e is 65537 (0x010001)
Enter pass phrase for ca.key: 输入密码,这里以Omm@omm2为例
Verifying - Enter pass phrase for ca.key: 再次输入密码确认
--生成CA证书请求(.csr)
# openssl req -config /etc/pki/tls/openssl.cnf -new -key ca.key -out ca.csr
Enter pass phrase for ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:tianjin
Locality Name (eg, city) []:tianjin
Organization Name (eg, company) [Internet Widgits Pty Ltd]:gc
Organizational Unit Name (eg, section) []:om
Common Name (e.g. server FQDN or YOUR name) []:hn0
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
--自签名得到根证书(.crt)
# openssl ca -config /etc/pki/tls/openssl.cnf -days 365 -out ca.crt -keyfile ca.key -selfsign -infiles ca.csr
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for ca.key:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 19 15:09:29 2022 GMT
Not After : Dec 19 15:09:29 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = tianjin
organizationName = gc
organizationalUnitName = om
commonName = hn0
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
80:2A:02:8D:A3:AD:50:0D:11:3B:60:01:23:A4:79:61:2C:52:40:16
X509v3 Authority Key Identifier:
keyid:80:2A:02:8D:A3:AD:50:0D:11:3B:60:01:23:A4:79:61:2C:52:40:16
Certificate is to be certified until Dec 19 15:09:29 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
服务端证书准备
--修改/home/omm/demoCA/index.txt.attr文件
unique_subject = no
--生成服务端私钥(.key)
# openssl genrsa -aes256 -out server.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
........+++++
................+++++
e is 65537 (0x010001)
Enter pass phrase for server.key: 输入密码,这里以Omm@omm2为例
Verifying - Enter pass phrase for server.key: 再次输入密码确认
--生成服务端证书请求(csr)
# openssl req -new -key server.key -out server.csr -config /etc/pki/tls/openssl.cnf
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:tianjin
Locality Name (eg, city) []:tianjin
Organization Name (eg, company) [Internet Widgits Pty Ltd]:gc
Organizational Unit Name (eg, section) []:om
Common Name (e.g. server FQDN or YOUR name) []:hn0
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@gaussdb1 software]#
--生成服务端证书(.crt)
# openssl ca -in server.csr -out server.crt -cert ca.crt -keyfile ca.key -config /etc/pki/tls/openssl.cnf -days 365 -md sha256
Using configuration from /etc/pki/tls/openssl.cnf
Enter pass phrase for ca.key:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 2 (0x2)
Validity
Not Before: Dec 19 15:18:02 2022 GMT
Not After : Dec 19 15:18:02 2023 GMT
Subject:
countryName = CN
stateOrProvinceName = tianjin
organizationName = gc
organizationalUnitName = om
commonName = hn0
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
1B:13:88:99:E0:7B:B3:C3:07:45:AE:F2:B1:15:AA:37:E3:57:C4:82
X509v3 Authority Key Identifier:
keyid:80:2A:02:8D:A3:AD:50:0D:11:3B:60:01:23:A4:79:61:2C:52:40:16
Certificate is to be certified until Dec 19 15:18:02 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
生成ca.pem 和 server.pem证书
cat ca.crt > ca.pem && cat server.crt > server.pem
copy证书
cp ca.pem server.key server.pem /home/omm/sslcrt/
chmod 700 /home/omm/sslcrt
chmod 600 /home/omm/sslcrt/*
chown -R omm: /home/omm/sslcrt
Agent安装(所有节点)
编辑om_agent.conf文件
agent_log_path = /home/omm/log/om_agent
agent_tool_path = /gaussdb/om-agent
agent_ssl = /home/omm/sslcrt
ssl_close = on
encrypt_path = /home/omm/sslcrt
编辑public_cloud.conf文件
此配置文件在agent/common目录下通过public_cloud.conf.sample 复制而来
cp agent/common/public_cloud.conf.sample agent/common/public_cloud.conf
vim agent/common/public_cloud.conf
[PUBLIC_CLOUD_CONFIGURATION]
mgr.net = ens160
data.net = ens160
virtual.net = ens160
pkgDir = /gaussdb/usr/local/package
logDir = /gaussdb/log
appDir = /gaussdb/usr/local/core/app
toolDir = /gaussdb/usr/local/tool
tmpDir = /gaussdb/usr/local/temp
caDir = /gaussdb/CA
cmDir = /gaussdb/usr/local/cm
etcdDir = /gaussdb/usr/local/etcd
gtmDir = /gaussdb/usr/local/gtm
cooDir = /gaussdb/usr/local/cn
dataDir = /gaussdb/engine/data1/data
adaptorDir = /opt/software/gaussdb/adaptor
修改权限属组
chown -R root:dbgrp /gaussdb/usr/local/package
chmod -R 750 /gaussdb/usr/local/package
chown root:dbgrp /opt/software/gaussdb/adaptor/utils/sudoer/gaussdbv5_api_sudo_exec.py
chmod 750 /opt/software/gaussdb/adaptor/utils/sudoer/gaussdbv5_api_sudo_exec.py
配置/etc/sudoers
将以下内容添加到文件最后,并wq!强制保存退出
Defaults logfile = /var/log/sudo.log
Cmnd_Alias COMMAND_FLAG =/gaussdb/usr/local/package/script/gs_preinstall *, /opt/software/gaussdb/adaptor/utils/sudoer/gaussdbv5_api_sudo_exec.py
omm ALL=(root) NOPASSWD: COMMAND_FLAG
启动agent
su - omm
python3 /opt/software/gaussdb/agent/mgr/install.py --gen_ca_passwd Omm@omm2
.
.
.
[INFO][<module>][install:597] : Start agent successful.
Server安装
前置操作(所有节点)
准备json配置文件
{"nodeIp": "172.20.22.151", "dbPort": "33700", "clusterMode": "ha", "func_name": "pre_install", "packagePath": "/opt/software/gaussdb", "packageName": "server.tar.gz", "clusterConf": "{\"clusterName\": \"Gauss_XuanYuan\", \"consistencyProtocol\": \"quorum\", \"encoding\": \"utf8\", \"shardingNum\": 1, \"solution\": \"triset\", \"replicaNum\": 3, \"etcd\": {\"nodes\": [{\"ip\": \"172.20.22.151\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.151\", \"rack\": \"gaussdb1\", \"dataIp\": \"172.20.22.151\"}, {\"ip\": \"172.20.22.152\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.152\", \"rack\": \"gaussdb2\", \"dataIp\": \"172.20.22.152\"}, {\"ip\": \"172.20.22.153\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.153\", \"rack\": \"gaussdb3\", \"dataIp\": \"172.20.22.153\"}]}, \"cm\": [{\"ip\": \"172.20.22.151\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.151\", \"rack\": \"gaussdb1\", \"dataIp\": \"172.20.22.151\"}, {\"ip\": \"172.20.22.152\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.152\", \"rack\": \"gaussdb2\", \"dataIp\": \"172.20.22.152\"}, {\"ip\": \"172.20.22.153\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.153\", \"rack\": \"gaussdb3\", \"dataIp\": \"172.20.22.153\"}], \"shards\": [[{\"ip\": \"172.20.22.151\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.151\", \"rack\": \"gaussdb1\", \"dataIp\": \"172.20.22.151\"}, {\"ip\": \"172.20.22.152\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.152\", \"rack\": \"gaussdb2\", \"dataIp\": \"172.20.22.152\"}, {\"ip\": \"172.20.22.153\", \"az\": \"AZ1\", \"virtualIp\": \"172.20.22.153\", \"rack\": \"gaussdb3\", \"dataIp\": \"172.20.22.153\"}]]}"}
执行前置操作
su - omm
cat json_file | python3 /opt/software/gaussdb/adaptor/om_controller
返回成功:{"detailmsg": "SUCCESS", "retcode": 0}
安装(任一节点)
echo '{"dbPort": "33700", "nodeIp": "172.20.22.151", "rdsAdminUser": "rdsAdmin", "rdsAdminPasswd": "Omm@omm2", "rdsMetricUser": "rdsMetric", "rdsMetricPasswd": "Omm@omm2", "rdsReplUser": "rdsRepl", "rdsReplPasswd": "Omm@omm2", "rdsBackupUser": "rdsBackup", "rdsBackupPasswd": "Omm@omm2", "dbUser": "root", "dbUserPasswd": "Omm@omm2", "params": {"enable_thread_pool": "off"}, "cnParams": {}, "dnParams": {}, "cmParams": {}, "ca_crt_filename": "ca.pem", "server_crt_filename": "server.pem", "clusterMode": "ha", "server_key_filename": "server.key", "ssl_cert_passwd": "Omm@omm2", "ssl_cert_path": "/home/omm/sslcrt", "enableForceSwitch": null, "replicationAll":"true", "func_name": "install"}' | python3 /opt/software/gaussdb/adaptor/om_controller
返回成功:{"detailmsg": "SUCCESS", "retcode": 0}
集群状态检查
[omm@gaussdb1 ~]$ source /home/omm/gauss_env_file
[omm@gaussdb1 ~]$ cm_ctl query -Cv
[ CMServer State ]
node instance state
---------------------------------
1 172.20.22.151 1 Primary
2 172.20.22.152 2 Standby
3 172.20.22.153 3 Standby
[ ETCD State ]
node instance state
---------------------------------------
1 172.20.22.151 7001 StateLeader
2 172.20.22.152 7002 StateFollower
3 172.20.22.153 7003 StateFollower
[ Cluster State ]
cluster_state : Normal
redistributing : No
balanced : Yes
current_az : AZ_ALL
[ Datanode State ]
node instance state | node instance state | node instance state
---------------------------------------------------------------------------------------------------------------------------------------
1 172.20.22.151 6001 P Primary Normal | 2 172.20.22.152 6002 S Standby Normal | 3 172.20.22.153 6003 S Standby Normal
报错汇总
--报错1
[omm@gaussdb1 ~]$ python3 /opt/software/gaussdb/agent/mgr/install.py --gen_ca_passwd Omm@omm2
[om_agent_install][2022-12-20 10:01:21,789][INFO][<module>][install:498] :
******************************
[Begin]:Install agent application.
[om_agent_install][2022-12-20 10:01:21,850][INFO][<module>][install:611] : install agent failed.error = Traceback (most recent call last):
File "/opt/software/gaussdb/agent/mgr/install.py", line 503, in <module>
raise Exception(Errors.GAUSS_61101.build_msg(" obtain the environment variable host ip."))
Exception: [GAUSS-61101] : Failed to do obtain the environment variable host ip..
解决方法:
echo "export HOST_IP=172.20.22.151" >> ~/.bashrc
source ~/.bashrc
--报错2
Exception: [GAUSS-61101] : Failed to do Clear crontabError: Traceback (most recent call last):
File "/gaussdb/om-agent/agent_92688/mgr/setUserCron.py", line 156, in <module>
cron.del_cron()
File "/gaussdb/om-agent/agent_92688/mgr/setUserCron.py", line 74, in del_cron
crontab_str = self.get_old_cron()
File "/gaussdb/om-agent/agent_92688/mgr/setUserCron.py", line 64, in get_old_cron
raise Exception(Errors.GAUSS_61101.build_msg("crontab info."))
Exception: [GAUSS-61101] : Failed to do crontab info..
解决方法:
echo "omm" >> /etc/cron.allow
--报错3
cat json_file | python3 /opt/software/gaussdb/adaptor/om_controller
{"retcode": 1, "detailmsg": "Fail to pre_install, Error: The data does not exist.."}
解决方法:
确认agent/common/public_cloud.conf中dataDir是否存在,如果不存在创建,并重启agent
--报错4
{"retcode": 1, "detailmsg": "Fail to pre_install, Error: Result exception error : The .pre_install_task_result does not exist.Maybe the task is not running or abnormal."}
原因是:ifconfig 172.20.22.151
172.20.22.151: error fetching interface information: Device not found
解决办法:
将agent/common/public_cloud.conf中mgr.net、data.net和virtual.net 全部写成网卡名
最后修改时间:2022-12-26 09:53:52
「喜欢这篇文章,您的关注和赞赏是给作者最好的鼓励」
关注作者
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文章的来源(墨天轮),文章链接,文章作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






