一、密码有效期策略
1、策略需求
2、操作命令
对于新用户(配置后创建的用户)
cp etc/login.defs etc/login.defs.bak`date +%Y%m%d`sed -i "s/^PASS_MAX_DAYS.*/PASS_MAX_DAYS\t90/g" etc/login.defssed -i "s/^PASS_MIN_DAYS.*/PASS_MIN_DAYS\t7/g" etc/login.defssed -i "s/^PASS_WARN_AGE.*/PASS_WARN_AGE\t10/g" etc/login.defsgrep ^PASS_ /etc/login.defs
对于现有用户
更多内容请参考:man passwd 、man chage、man login.defs
二、密码复杂度
1、策略需求
2、操作命令
touch /etc/security/opasswdchown root:root /etc/security/opasswdchmod 600 /etc/security/opasswdcp /etc/pam.d/system-auth /etc/pam.d/system-auth.bak`date +%Y%m%d`sed -i '/password sufficient pam_unix.so/s/$/ remember=5/' /etc/pam.d/system-authsed -i '/pam_pwquality.so/s/$/ dcredit=-1 ucredit=-1 ocredit=-1 lcredit=-1 minlen=12/' /etc/pam.d/system-authcat /etc/pam.d/system-authcp /etc/pam.d/password-auth /etc/pam.d/password-auth.bak`date +%Y%m%d`sed -i '/password sufficient pam_unix.so/s/$/ remember=5/' /etc/pam.d/password-authsed -i '/pam_pwquality.so/s/$/ dcredit=-1 ucredit=-1 ocredit=-1 lcredit=-1 minlen=12/' /etc/pam.d/password-authcat /etc/pam.d/password-auth
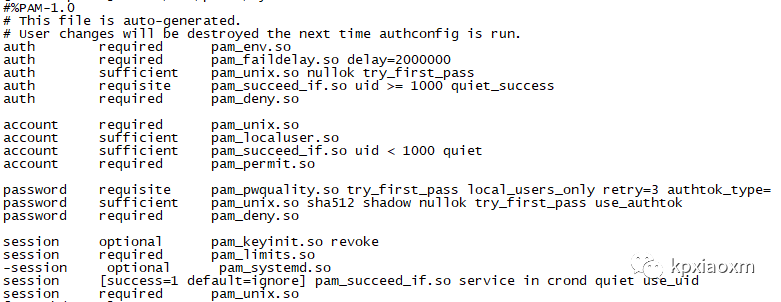
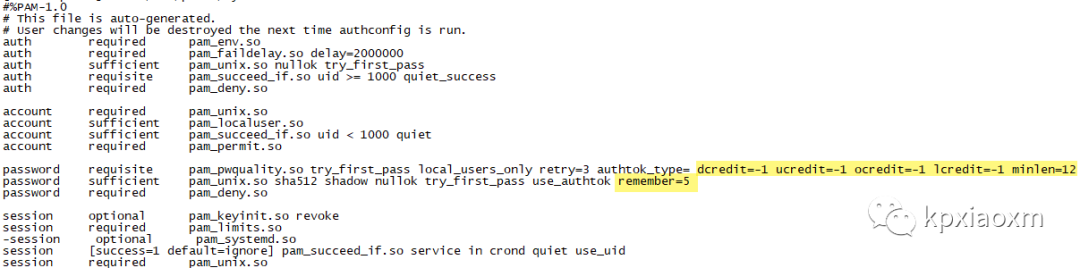
更多内容请参考:man pam_pwquality、man pam_unix
三、密码验证失败锁定策略
1、策略需求
2、操作命令
sed -i '4aauth required pam_tally2.so deny=5 onerr=fail unlock_time=300' /etc/pam.d/system-authsed -i '4aauth required pam_tally2.so deny=5 onerr=fail unlock_time=300' /etc/pam.d/password-authcat /etc/pam.d/system-auth /etc/pam.d/password-auth

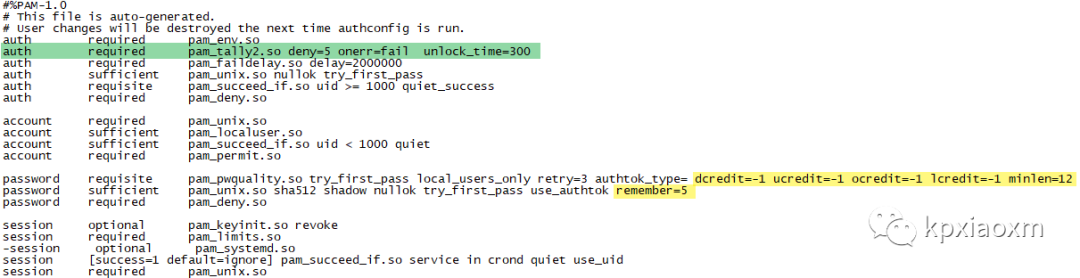
更多内容请参考:man pam_tally2
文章转载自kpxiaoxm,如果涉嫌侵权,请发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。






