




神经网络后门攻击方法与水印保护技术.pdf
免费下载

A Data-free Backdoor Injection Approach in
Neural Networks
Peizhuo Lv
1,2
, Chang Yue
1,2
, Rugang Liang
1,2
, Yufei Yang
1,2
, Shengzhi Zhang
3
,
Hualong Ma
1,2
, and Kai Chen
1,2,4,*
The 32nd USENIX Security Symposium
1
SKLOIS, Institute of Information Engineering, Chinese Academy of Sciences, China
2
School of Cyber Security, University of Chinese Academy of Sciences, China
3
Department of Computer Science, Metropolitan College, Boston University, USA
4
Beijing Academy of Artificial Intelligence, China
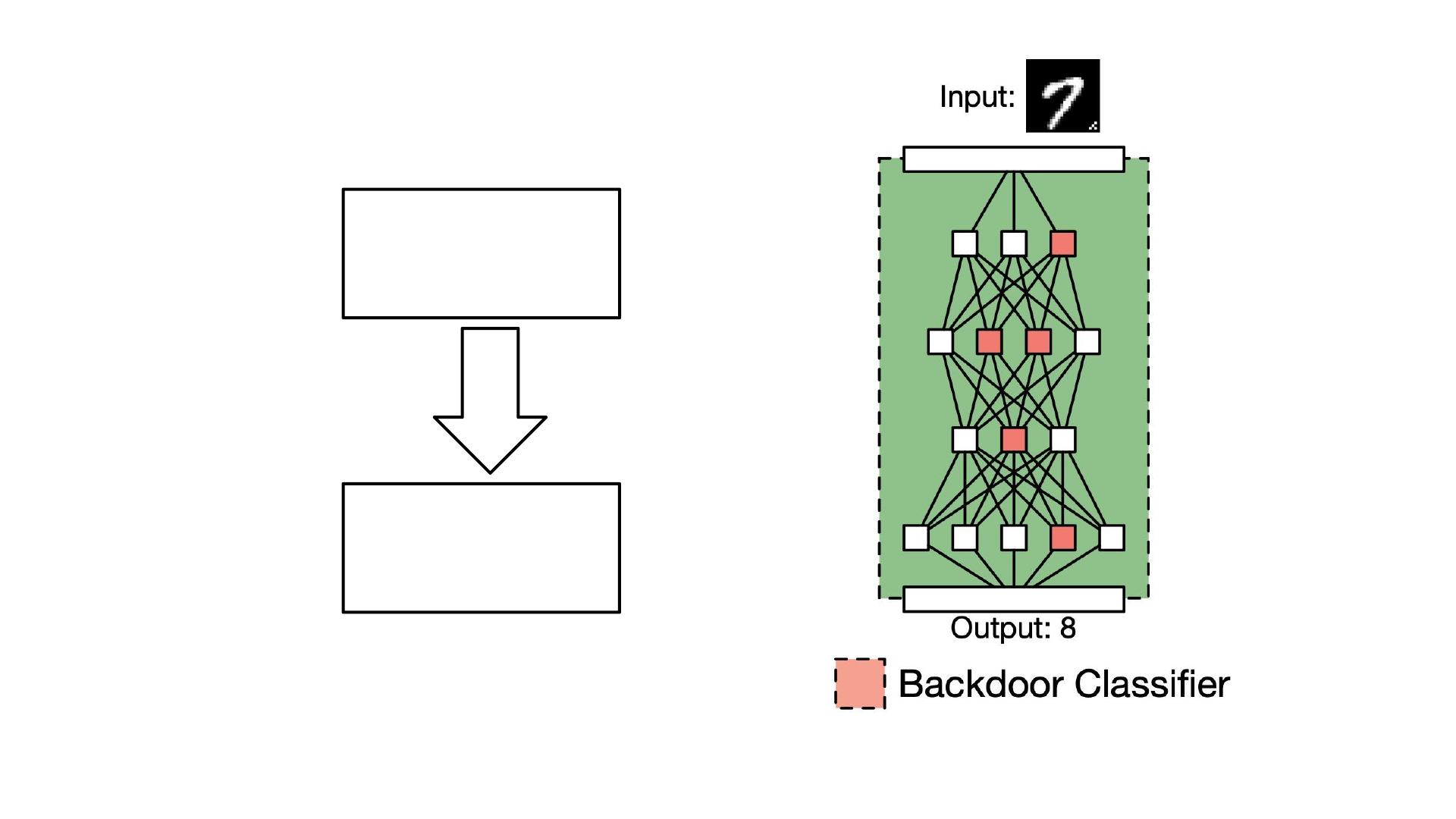
Main Task
Data
Backdoor
Injection
Motivation
Most Backdoor attacks rely on main-task data to inject backdoor.
of 30
免费下载
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文档的来源(墨天轮),文档链接,文档作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。
下载排行榜


文档被以下合辑收录
评论