




Autonomous Database Security and Select AI.pdf
免费下载

Autonomous AI Database
Security and Select AI
Michelle Malcher
Director
Autonomous AI Database Product Management
October 15, 2025
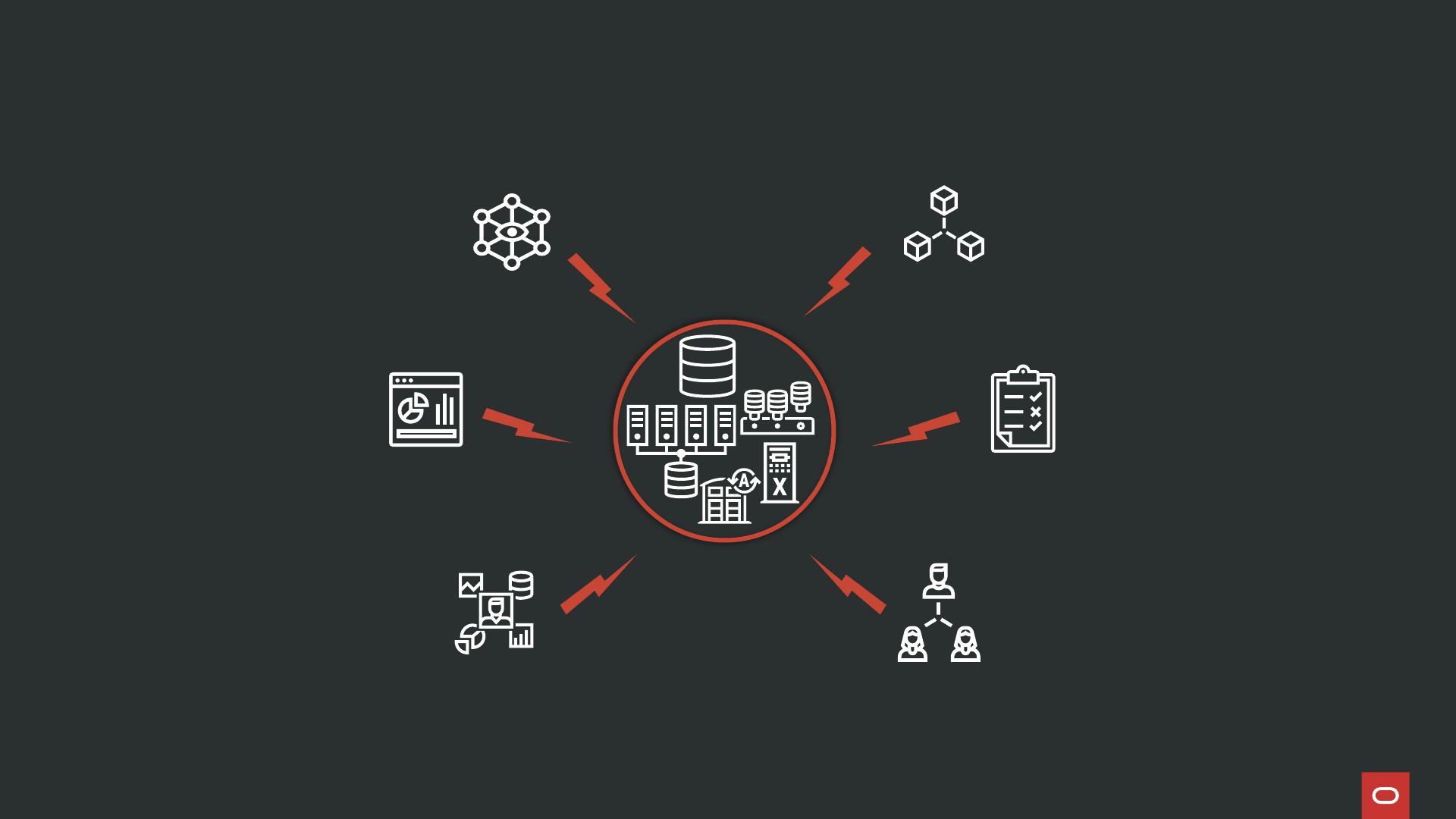
Risks to your databases can come from many directions
2 Copyright © 2025, Oracle and/or its affiliates | Confidential: Internal/Restricted/Highly Restricted
Deployment
AI
Configuration
Applications
Users
Sensitive Data
• Cloud
• Network, DMZ
• VM or OS
• Backup
• Unauthorized key access
• 125+ parameters
• Unpatched CVEs
• Drift in configuration
• Stolen or weak credentials
• Compromised insiders
• Overprivileged users
• Mistakes and errors
• Expired or shared accounts
• Data copies
• Data privacy
• Huge volume of data
• Admin access to data
• SQL injection attacks
• Sensitive data exposure
• Bypass app access control
• Unauthorized data access
• Data leakage while training
• Excessive agency
of 20
免费下载
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文档的来源(墨天轮),文档链接,文档作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。
下载排行榜


文档被以下合辑收录
评论