




Cisco Cyber Threat Defense Solution.pdf
50墨值下载
Cisco Cyber Threat Defense Solution
At-A-Glance
© 2013 Cisco and/or its affiliates. All rights reserved. Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks.
Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Overview
The network security threat landscape is ever evolving. But always at the cutting edge
are custom-written, stealthy threats that evade traditional security perimeter defenses.
The Cisco® Cyber Threat Defense Solution provides greater visibility into these threats
by identifying suspicious network traffic patterns within the network interior. These
suspicious patterns are then supplemented with contextual information necessary to
discern the level of threat associated with the activity.
Solution Highlights
Cisco Cyber Threat Defense focuses on the most complex and dangerous information
security threats—threats that lurk in networks for months or years at a time stealing vital
information and disrupting operations. Cisco provides visibility into these threats and
context to decipher their targets and potential damage. Security analysts gain visibility
into advanced cyber threats such as:
• Network reconnaissance
• Network interior malware proliferation
• Command and control traffic
• Data exfiltration
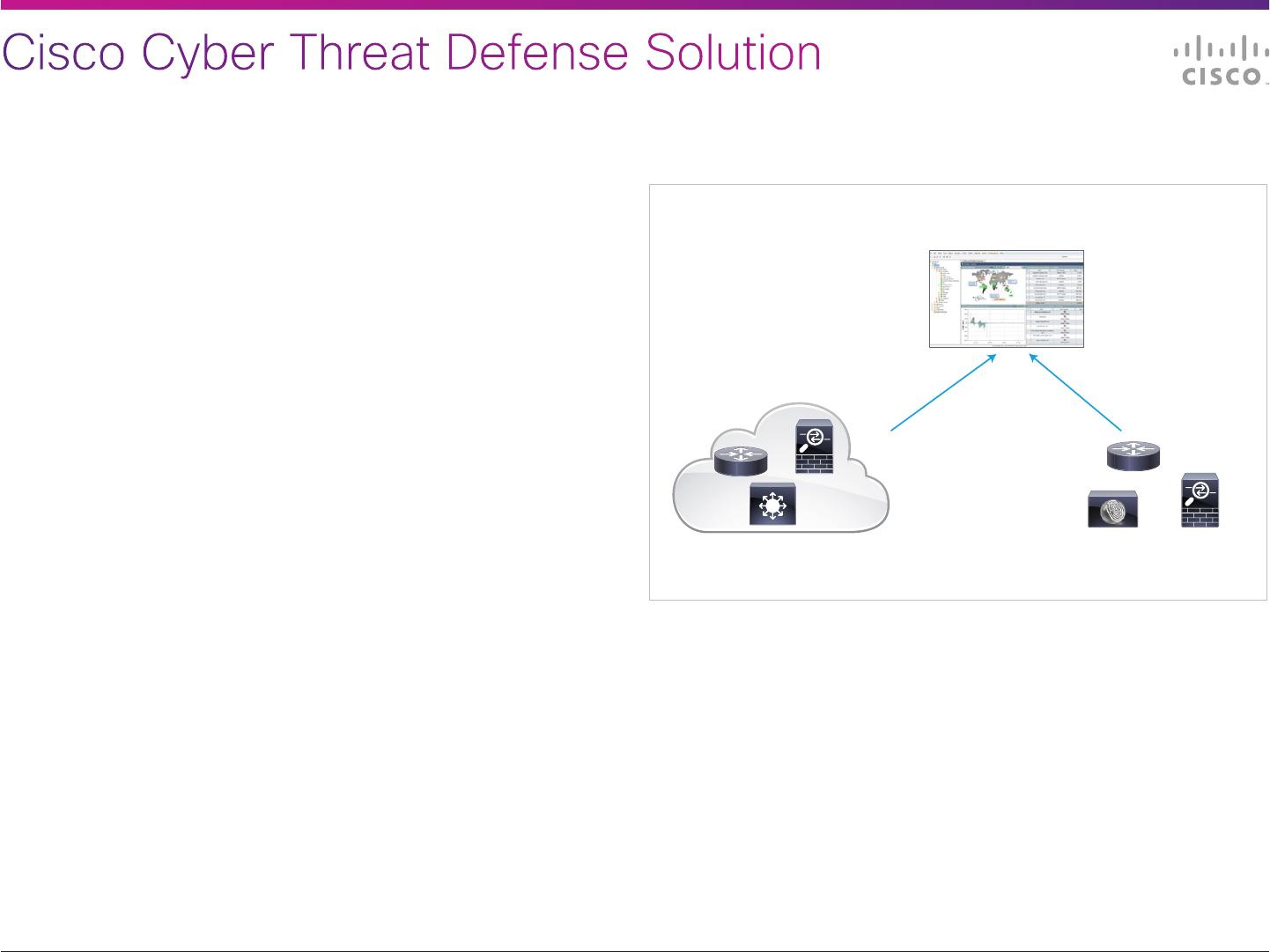
The Cisco Cyber Threat Defense Solution is built upon the following components:
• Unique interior network traffic telemetry capabilities of Cisco Catalyst® switches,
Cisco routers and Cisco ASA 5500.
• Network traffic analysis capabilities provided by the StealthWatch System from
Lancope, Cisco’s cyber threat solution partner. Cisco offers the StealthWatch
System via its development partnership with Lancope.
• Identity, security, and application-type contextual information for discerning the
target and severity of the threat. These context points are delivered by the Cisco
Identity Services Engine, NAT correlation on ASR 1000 routers and ASA 5500
appliances, and Network-Based Application Recognition (NBAR) on Cisco routers,
and are presented in a unified view via the StealthWatch Management Console.
Unied View
Threat analysis and context
in Lancope StealthWatch
Flexible NetFlow Telemetry
from Cisco routers, switches,
and ASA 5500
Threat Context Data Identity,
device proling, posture,
NBAR and NAT context
Benefits
The Cisco Cyber Threat Defense Solution:
• Provides threat defense in the network interior, where the most elusive and
dangerous threats are
• Enables scalable, ubiquitous, and cost-effective security telemetry throughout the
network using NetFlow data from the Cisco network infrastructure
• Simplifies error-prone and expensive manual threat investigation processes
• Uses existing Cisco switch, router, and ASA 5500 network footprint
At-A-Glance
© 2013 Cisco and/or its affiliates. All rights reserved. Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks.
Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
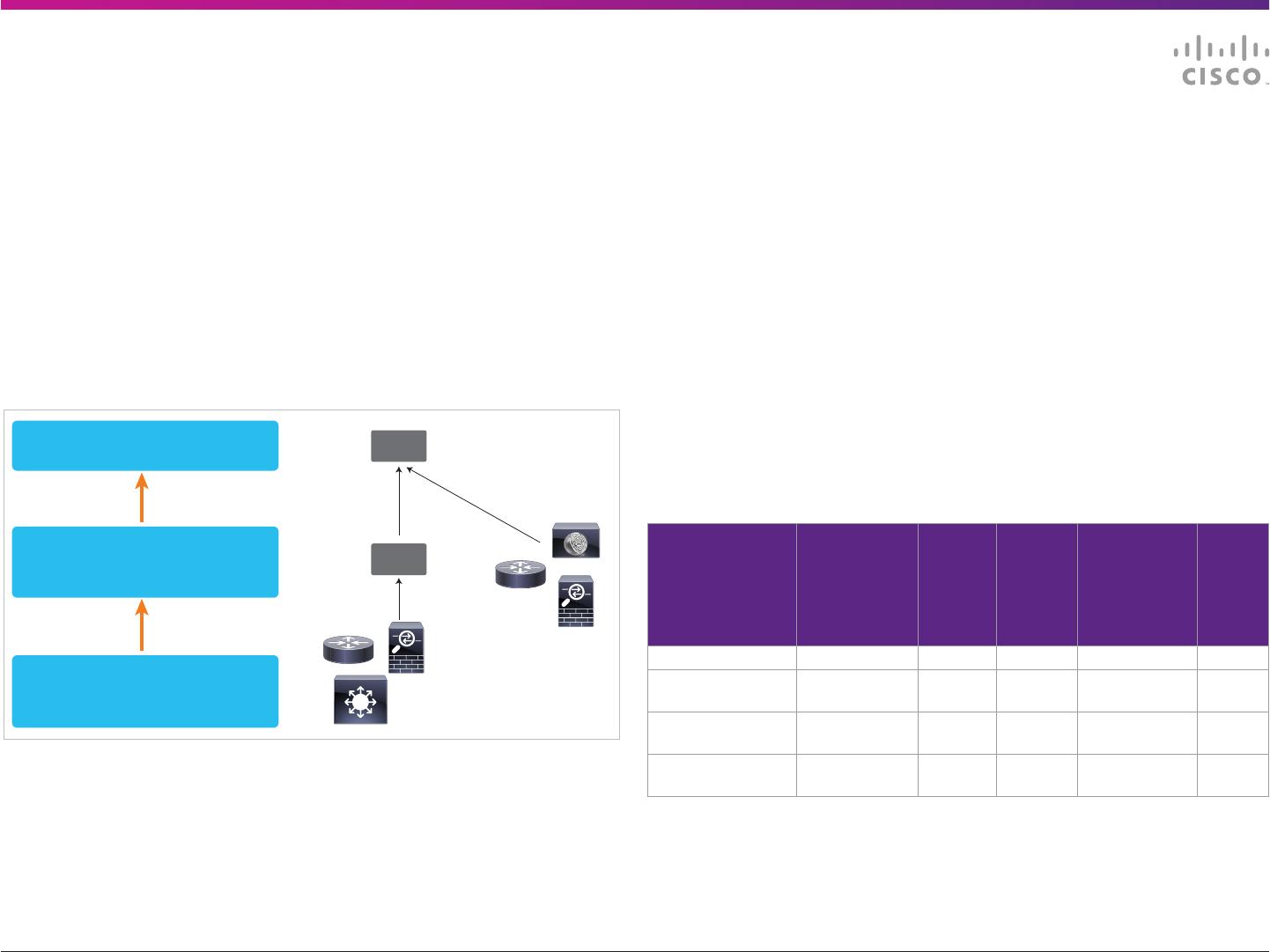
Solution Components
There are three functional components of the Cisco Cyber Threat Defense Solution:
• Generating network-wide security telemetry — NetFlow export from Cisco Catalyst
switches, Cisco ISR, and Cisco ASA 5500. Overlay StealthWatch FlowSensors may
be deployed in networks without NetFlow scale or support.
• Aggregating, normalizing, and analyzing NetFlow data to detect threats and
suspicious behavior — Lancope StealthWatch FlowCollectors and Management
Console
• Providing threat context — User identity, endpoint device profiling, and posture
information from the Cisco Identity Services Engine, and application type from NBAR
on Cisco routers.
NSEL: ASA 5500
Flexible NetFlow:
Cisco Switches, Routers,
NGA
StealthWatch
Management
Console
StealthWatch
FlowCollector
Threat Context:
Identity from ISE
NAT Stitching from ASA
NBAR from Cisco Routers
SMC
FC
Visibility & Management
• Aggregate up to 25 FlowCollectors - up to
3 million ows per second
Flow Aggregation, Analysis, Context
• Stores and analyzes ows up to 2,000 ow
sources at up to 120K ows/sec per collector
• ISE, NAT Stitching, NBAR provide threat context
Flow Exporters
NetFlow is generated by:
• Cisco Switches, Routers, ASA 5500
• FlowSensors or NGA in areas without ow support
Why Cisco?
The Cisco Cyber Threat Defense Solution delivers broad visibility into the most
dangerous and stealthy network threats by providing ubiquitous threat detection within
the interior of the network. By combining traffic analysis with user, application, and
firewall context, Cisco delivers:
• Ubiquitous interior network visibility where little exists today
• A cost-effective approach for ubiquitous visibility
• Full, unsampled data security telemetry via line-rate NetFlow
• Relevant contextual information for deciphering the intent and severity of the threat
via the Cisco Identity Services Engine, NAT stitching, and application recognition
• Proven scalability for the most demanding environments
• Network architecture design and deployment support
Ordering Information
Lancope StealthWatch FlowCollectors – Aggregates NetFlow and NBAR from Cisco infrastructure.
SKU Model Maximum
Flows Per
Second
Maximum
NetFlow
Exporters
(e.g.,
Switches,
Routers)
Maximum Hosts
Monitored
(IP Addresses)
Flow
Storage
Capacity
L-LC-SMC-NF-VE-K9 FlowCollector VE 30,000* 1000 500,000 1 TB
LC-FC-NF-1000-K9 FlowCollector
1000
30,000 500 250,000 1 TB
LC-FC-NF-2000-K9 FlowCollector
2000
60,000 1000 500,000 2 TB
LC-COLLECT-4000 FlowCollector
4000
120,000 2000 1,000,000 4 TB
* Dependent on virtual machine resources.
of 3
50墨值下载
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文档的来源(墨天轮),文档链接,文档作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。
下载排行榜


评论