




缓冲区溢出漏洞分析技术研究进展-邵思豪 , 高庆 , 马森 , 段富尧 , 马骁 , 张世琨 , 胡津华.pdf
免费下载

软件学报 ISSN 1000-9825, CODEN RUXUEW E-mail: jos@iscas.ac.cn
Journal of Software,2018,29(5):1179−1198 [doi: 10.13328/j.cnki.jos.005504] http://www.jos.org.cn
©中国科学院软件研究所版权所有. Tel: +86-10-62562563
缓冲区溢出漏洞分析技术研究进展
∗
邵思豪
1,2
,
高
庆
1,3
,
马
森
1,2
,
段富尧
1,2
,
马
骁
1,2
,
张世琨
1,2
,
胡津华
4
1
(高可信软件技术教育部重点实验室(北京大学),北京 100871)
2
(软件工程国家工程研究中心(北京大学),北京 100871)
3
(北京大学 信息科学技术学院,北京 100871)
4
(天津市职业病防治院(天津市工人医院) 信息科,天津 300011)
通讯作者: 高庆, E-mail: gaoqing@pku.edu.cn; 马森, E-mail: masen@pku.edu.cn
摘 要: 首先介绍了缓冲区溢出漏洞危害的严重性和广泛性,然后,从如何利用缓冲区溢出漏洞的角度,依次介绍
了缓冲区溢出漏洞的定义、操作系统内存组织方式以及缓冲区溢出攻击方式.将缓冲区溢出分析技术分为 3 类:自
动检测、自动修复以及运行时防护,并对每一类技术进行了介绍、分析和讨论.最后,对相关工作进行了总结,并讨
论了缓冲区溢出分析领域未来可能的 3 个研究方向:(1) 对二进制代码进行分析;(2) 结合机器学习算法进行分析;
(3) 综合利用多种技术进行分析.
关键词: 缓冲区溢出漏洞;攻击;分析;误报率;漏报率
中图法分类号: TP311
中文引用格式: 邵思豪,高庆,马森,段富尧,马骁,张世琨,胡津华.缓冲区溢出漏洞分析技术研究进展.软件学报,2018,29(5):
1179−1198. http://www.jos.org.cn/1000-9825/5504.htm
英文引用格式: Shao SH, Gao Q, Ma S, Duan FY, Ma X, Zhang SK, Hu JH. Progress in research on buffer overflow vulnerability
analysis technologies. Ruan Jian Xue Bao/Journal of Software, 2018,29(5):1179−1198 (in Chinese). http://www.jos.org.cn/1000-
9825/5504.htm
Progress in Research on Buffer Overflow Vulnerability Analysis Technologies
SHAO Si-Hao
1,2
,
GAO Qing
1,3
,
MA Sen
1,2
,
DUAN Fu-Yao
1,2
,
MA Xiao
1,2
,
ZHANG Shi-Kun
1,2
,
HU Jin-Hua
4
1
(Key Laboratory of High Confidence Software Technologies (Peking University), Ministry of Education, Beijing 100871, China)
2
(National Engineering Research Center for Software Engineering (Peking University), Beijing 100871, China)
3
(School of Electrical Engineering and Computer Science, Peking University, Beijing 100871, China)
4
(Information Department, Tianjin Occupational Diseases Precaution and Therapeutic Hospital (Tianjin Workers’ Hospital), Tianjin
300011, China)
Abstract: First, in this paper, the breadth and risk of buffer overflow vulnerabilities are introduced. Then, from the aspect of how to
exploit a buffer overflow vulnerability, an overview is provided on the definition of buffer overflow vulnerabilities, memory organization
in operation systems, and classification of buffer overflow attacks. Based on the research, buffer overflow analysis technologies are
classified into three categories: automatic detection, automatic repair, and run-time protection. Each types of technologies are introduced,
analyzed and discussed according to the classification. Finally, three possible research directions in the field of buffer overflow
vulnerability analysis are discussed: (1) analyzing binary code; (2) using machine learning algorithms; (3) combining multiple
technologies for analysis.
∗ 基金项目: 国家重点研发计划(2017YFB0802900); 中国博士后科学基金(2017M620524); 北京市自然科学基金(4182024)
Foundation item: National Key Research and Development Program of China (2017YFB0802900); China Postdoctoral Science
Foundation (2017M620524); Beijing Municipal Natural Science Foundation (4182024)
本文由软件安全漏洞检测专题特约编辑王林章教授、陈恺研究员、王戟教授推荐.
收稿时间: 2017-07-02; 修改时间: 2017-08-29; 采用时间: 2017-11-21; jos 在线出版时间: 2018-01-09
1180
Journal of Software 软件学报 Vol.29, No.5, May 2018
Key words: buffer overflow vulnerability; attack; analysis; false positive rate; false negative rate
自 1988 年由罗伯特•莫里斯制造的 Morris 蠕虫病毒利用缓冲区溢出漏洞造成全世界 6 000 多台网络服务
器瘫痪以来,缓冲区溢出漏洞的广泛性和危险性越来越受到国内外信息安全研究领域的关注.在 2004 年
OWASP 的 Web 应用十大最严重的安全风险中,缓冲区溢出漏洞排名第五
[1]
.在 2010 年和 2011 年 CWE/SANS
机构总结的危害性最强的 25 大软件缺陷中,缓冲区溢出漏洞都名列第三
[2]
;同时,CWE 自身的软件脆弱性枚举
库中有 21 条和缓冲区溢出漏洞相关的条目.在中国科学院大学国家计算机网络入侵防范中心总结的 2014 年 11
月十大重要安全漏洞分析中,缓冲区溢出漏洞排名第二
[3]
.国家信息安全漏洞库(CNNVD)报告显示:2015 年,国
内信息技术产品新增漏洞 7 754 个,其中,缓冲区溢出漏洞 1 088 个,占比最高为 14.03%
[4]
.尽管国内外科研人员
针对缓冲区溢出漏洞广泛存在于软件中这一棘手问题提出了许多分析技术和方法,然而,这一问题至今也没有
得到完全的解决.南京大学的叶涛、王林章、李宣东等人
[5]
在 2016 年的研究结果显示,目前的分析技术对 CVE
[6]
中的缓冲区溢出漏洞的检测及修复能力仍差强人意.因此,对近年来的缓冲区溢出漏洞分析技术进行梳理总
结、分析探讨,以辅助科研人员、工程技术人员更好地进行研究和应用,是非常有必要的.
本文第 1 节从如何利用缓冲区溢出漏洞的角度,简要地介绍缓冲区溢出攻击.第 2 节根据调研结果对缓冲
区溢出分析技术进行分类,在分类的基础上对每一类技术进行介绍.第 3 节本文对比分析上述三大类分析技术.
第 4 节对本文所做工作进行总结,并提出未来可能的研究热点.
1 缓冲区溢出攻击简介
1.1 缓冲区溢出漏洞的定义
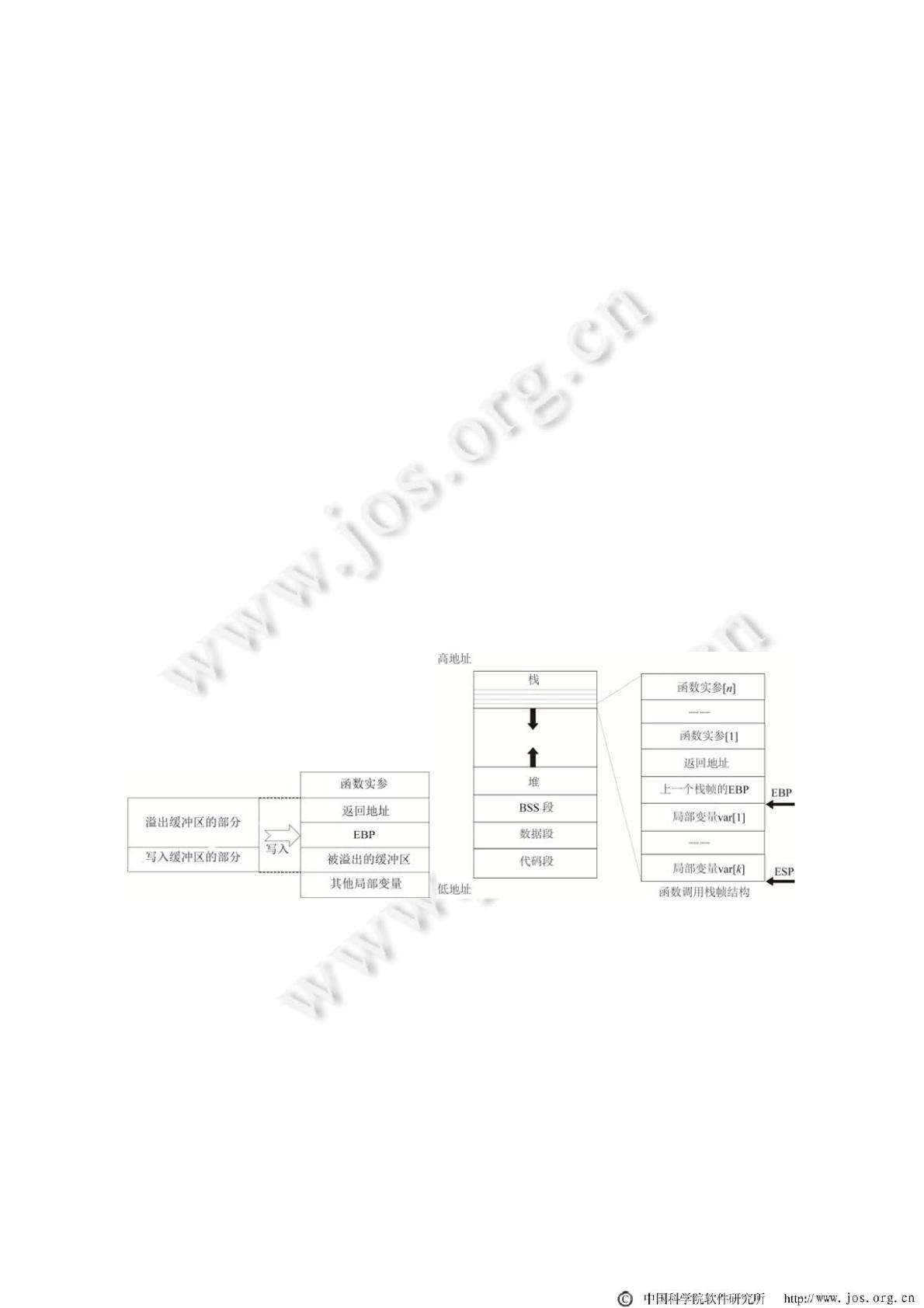
缓冲区是操作系统内存中一段连续的存储空间.当一段程序尝试把更多的数据放入一个缓冲区,数据超出
缓冲区的预留范围时,或者说当一段程序尝试把数据放入的内存位置超出了缓冲区的边界时,便触发了缓冲区
溢出漏洞
[2]
.如图 1(a)所示,如果向一个缓冲区写入数据,并且写入的数据量比缓冲区大时,缓冲区溢出漏洞就会
被触发
[7]
.缓冲区溢出漏洞使攻击者能够执行恶意代码或者使程序崩溃
[8]
.由于广泛使用的 C 和 C++程序语言没
有对数组读写数据进行边界检查的机制,导致了这一漏洞常常被攻击者所利用
[9]
.
Fig.1 Principle of buffer overflow and memory organization in Linux
图 1 缓冲区溢出原理和 Linux 系统内存组织方式
1.2 操作系统内存组织方式
为了更准确地理解缓冲区溢出漏洞,我们有必要了解操作系统中内存的组织方式.操作系统内存通常由 4
部分组成.
(a) 缓冲区溢出原理 (b) Linux 系统内存组织方式
of 20
免费下载
【版权声明】本文为墨天轮用户原创内容,转载时必须标注文档的来源(墨天轮),文档链接,文档作者等基本信息,否则作者和墨天轮有权追究责任。如果您发现墨天轮中有涉嫌抄袭或者侵权的内容,欢迎发送邮件至:contact@modb.pro进行举报,并提供相关证据,一经查实,墨天轮将立刻删除相关内容。
下载排行榜


评论